
Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

From playlist Cryptography Lectures

Hash Tables and Hash Functions
This computer science video describes the fundamental principles of the hash table data structure which allows for very fast insertion and retrieval of data. It covers commonly used hash algorithms for numeric and alphanumeric keys and summarises the objectives of a good hash function. Co
From playlist Data Structures

https://en.wikipedia.org/wiki/SHA-1#Examples_and_pseudocode If you have any questions of want to contribute to code or videos, feel free to write me a message on youtube or get my contact in the About section or googling my contacts.
From playlist Programming

Hacktivity 2010: Writing Your Own Password Cracker Tool
Speaker: Marcell Major
From playlist Hacktivity 2010

Clip 4/7 Speaker: Dan Kaminsky For more information go to: http://events.ccc.de/congress/2009/Fahrplan/events/3658.en.html
From playlist 26C3: Here be dragons day 3

Cryptographic Hash Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How Apple scans your phone (and how to evade it) - NeuralHash CSAM Detection Algorithm Explained
#apple #icloud #privacy Apple recently announced scanning all images uploaded to iCloud for CSAM (child abuse material), and that this scan would happen locally on users' phones. We take a look at the technical report and explore how the system works in detail, how it is designed to prese
From playlist Papers Explained

22C3: "Xbox" and "Xbox 360" Hacking
Speakers: Felix Domke, Michael Steil 17 Mistakes Microsoft Made in the Xbox Security System & Xbox 360 Hacking A lot about Xbox hacking has been published earlier. This talk summarizes all this, explains some very cool new hacks and analyzes the 15 mistakes Microsoft made in the Xbox sec
From playlist 22C3: Private Investigations

Merkle Tree In Blockchain | What Is The Merkle Tree In Blockchain | Merkle Tree | Simplilearn
🔥Professional Certificate Program In Blockchain: https://www.simplilearn.com/blockchain-certification-training-course?utm_campaign=MerkleTreeinBlockchain&utm_medium=Descriptionff&utm_source=youtube 🔥 Caltech Blockchain Bootcamp (US Only): https://www.simplilearn.com/blockchain-developer-ce
From playlist Blockchain Tutorial Videos 🔥[2022 Updated] | Simplilearn

Lecture 18: Fork Consistency, Certificate Transparency
Lecture 18: Fork Consistency, Certificate Transparency MIT 6.824: Distributed Systems (Spring 2020) https://pdos.csail.mit.edu/6.824/
From playlist MIT 6.824 Distributed Systems (Spring 2020)

Ethical Hacking using Python | Password Cracker Using Python | Python For Beginners | Simplilearn
This video on ethical hacking using python is dedicated to helping the aspiring ethical hackers with the fundamentals of cybersecurity. This python for beginners tutorial will cover the step-by-step procedure that explains the learners to design and develop a password cracker using python.
From playlist Python For Beginners 🔥[2022 Updated]
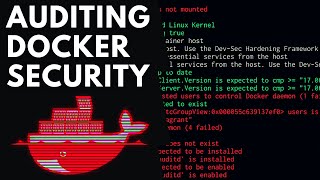
In this video, we will be taking a look at how to audit the security of the Docker platform with various tools in order to establish a baseline security benchmark. Docker Security Essentials eBook: https://bit.ly/3j9qRs8 Timestamps 0:00 Introduction 2:13 What we will be covering 3:07 Un
From playlist Docker

Securing Your Site by Thomas Pomfret
Rails makes it very easy to rapidly develop web applications, but doesn't always make it so simple to deploy or secure them. This talk is going to focus on best practices to secure your rails application, learnt through multiple high profile projects and penetration tests. The talk will b
From playlist Rails Conf 2012

From playlist Cryptography Lectures

Bitcoin Q&A: Important Terminology Explained
I am confused by terminology in Bitcoin. Please explain the following terms: private / public keys, hash functions, elliptic curve, addresses, and signatures. How can you create an address offline? How does the Bitcoin network "find out" about the address? Chapters 0:00 I'm confused by th
From playlist Bitcoin Q&A

