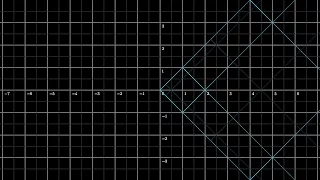
Ex 2: Find the Inverse of a Function
This video provides two examples of how to determine the inverse function of a one-to-one function. A graph is used to verify the inverse function was found correctly. Library: http://mathispower4u.com Search: http://mathispower4u.wordpress.com
From playlist Determining Inverse Functions
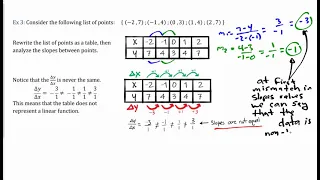
Define linear functions. Use function notation to evaluate linear functions. Learn to identify linear function from data, graphs, and equations.
From playlist Algebra 1
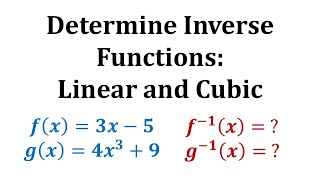
Ex 1: Find the Inverse of a Function
This video provides two examples of how to determine the inverse function of a one-to-one function. A graph is used to verify the inverse function was found correctly. Library: http://mathispower4u.com Search: http://mathispower4u.wordpress.com
From playlist Determining Inverse Functions
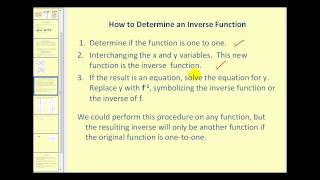
(New Version Available) Inverse Functions
New Version: https://youtu.be/q6y0ToEhT1E Define an inverse function. Determine if a function as an inverse function. Determine inverse functions. http://mathispower4u.wordpress.com/
From playlist Exponential and Logarithmic Expressions and Equations

Determine if a Function is a Polynomial Function
This video explains how to determine if a function is a polynomial function. http://mathispower4u.com
From playlist Determining the Characteristics of Polynomial Functions

Calculus 3.04b - Numerical Derivatives
How to approximate derivatives numerically using a calculator.
From playlist Calculus Ch 3 - Derivatives

Tim Taubert: Keeping secrets with JavaScript | JSConf EU 2014
With the web slowly maturing as a platform the demand for cryptography in the browser has risen, especially in a post-Snowden era. Many of us have heard about the upcoming Web Cryptography API but at the time of writing there seem to be no good introductions available. We will take a look
From playlist JSConf EU 2014

Part III: Partial Derivatives, Lec 3 | MIT Calculus Revisited: Multivariable Calculus
Part III: Partial Derivatives, Lecture 3: Directional Derivatives Instructor: Herbert Gross View the complete course: http://ocw.mit.edu/RES18-007F11 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT Calculus Revisited: Multivariable Calculus

undetermined coefficients, diff eq, sect4.5#19
solve a non-homogeneous second order differential equation with constant coefficients, method of undetermined coefficients,
From playlist Method of Undetermined Coefficients again, (Nagle Sect4.5)

Alain Passelègue - RKA Security for PRFs Beyond the Linear Barrier
RKA Security for PRFs Beyond the Linear Barrier
From playlist Journées Codage et Cryptographie 2014

CERIAS Security: PrivacyEnhancing k-Anonymization of Customer Data 3/9
Clip 3/9 Speaker: Sheng Zhong · SUNY at Buffalo In order to protect individuals' privacy, the technique of k-anonymization has been proposed to de-associate sensitive attributes from the corresponding identifiers. In this work, we provide privacy-enhancing methods for creating k-anony
From playlist The CERIAS Security Seminars 2005 (2)

Machine Learning with JAX - From Zero to Hero | Tutorial #1
❤️ Become The AI Epiphany Patreon ❤️ https://www.patreon.com/theaiepiphany 👨👩👧👦 Join our Discord community 👨👩👧👦 https://discord.gg/peBrCpheKE With this video I'm kicking off a series of tutorials on JAX! JAX is a powerful and increasingly more popular ML library built by the Goog
From playlist JAX

Chem 131A. Lec 04. Quantum Principles: Complementarity, Quantum Encryption, Schrodinger Equation
UCI Chem 131A Quantum Principles (Winter 2014) Lec 04. Quantum Principles -- Complementarity, Quantum Encryption, Schrodinger Equation -- View the complete course: http://ocw.uci.edu/courses/chem_131a_quantum_principles.html Instructor: A.J. Shaka, Ph.D License: Creative Commons BY-NC-SA
From playlist Chem 131A: Week 2

Building Generating Functions for Sequences Using Differencing
This video explains how to build generating functions for various sequences using the technique of differencing. mathispower4u.com
From playlist Additional Topics: Generating Functions and Intro to Number Theory (Discrete Math)

Shmoocon 2010: WLCCP - Analysis of a Potentially Flawed Protocol 4/6
Clip 4/6 Speakers: Enno Rey & Oliver Roeschke The world of "Enterprise WLAN solutions" is full of obscure and "non-standard" elements and technologies. One prominent example is Cisco's Structured Wireless-Aware Network (SWAN) architecture, composed of autonomous access points combined
From playlist ShmooCon 2010