
Hashing And EKE - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Private Messages Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Countermeasures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Definition of an Injective Function and Sample Proof
We define what it means for a function to be injective and do a simple proof where we show a specific function is injective. Injective functions are also called one-to-one functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear https://amzn.to/3BFvcxp (these are my affil
From playlist Injective, Surjective, and Bijective Functions

Steganography Tutorial - Hide Messages In Images
Steganography is the hiding of a secret message within an ordinary message and the extraction of it at its destination. Steganography takes cryptography a step further by hiding an encrypted message so that no one suspects it exists. Ideally, anyone scanning your data will fail to know it
From playlist Ethical Hacking & Penetration Testing - Complete Course

Correctness And Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
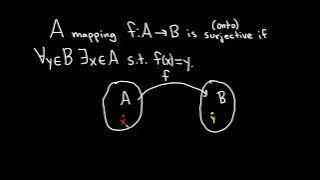
Definition of a Surjective Function and a Function that is NOT Surjective
We define what it means for a function to be surjective and explain the intuition behind the definition. We then do an example where we show a function is not surjective. Surjective functions are also called onto functions. Useful Math Supplies https://amzn.to/3Y5TGcv My Recording Gear ht
From playlist Injective, Surjective, and Bijective Functions

What is an Injective Function? Definition and Explanation
An explanation to help understand what it means for a function to be injective, also known as one-to-one. The definition of an injection leads us to some important properties of injective functions! Subscribe to see more new math videos! Music: OcularNebula - The Lopez
From playlist Functions

Cbc Implementation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cyber Security Week Day - 1 |Cryptography Full Course | Cryptography & Network Security| Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp This video on Cryptography full course will acquaint you with cryptograph
From playlist Simplilearn Live

Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CryptographyFCAug17&utm_medium=DescriptionFirstFold&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity
From playlist Simplilearn Live

🔥Cryptography And Network Security Full Course 2022 | Cryptography | Network Security | Simplilearn
🔥Free Cyber Security Course With Completion Certificate: https://www.simplilearn.com/learn-cyber-security-basics-skillup?utm_campaign=CryptographyNetworkSecurityFC4Aug22&utm_medium=DescriptionFirstFold&utm_source=youtube This video on the Cryptography and network security full course will
From playlist Simplilearn Live

Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
In this video on Top Hashing Algorithms In Cryptography, we will cover the technical aspects of hashing while going through some well-known hash functions and algorithms at the end. We cover the basics of cryptography and its applications. We also have detailed MD5 and SHA265 Explained sec
From playlist Cyber Security Playlist [2023 Updated]🔥

Cryptography Tutorial For Beginners | Cybersecurity Training | Edureka | Cybersecurity Live - 2
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "Cryptography Tutorial" gives an introduction to the Cryptography and talks about its basic concepts. 🔴Subscribe to our channel to get video updates. Hit the subscribe butto
From playlist Edureka Live Classes 2020

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

AES and DES Algorithm Explained | Difference between AES and DES | Network Security | Simplilearn
In today's video on AES and DES algorithm explained, we cover a major aspect of network security in encryption standards.The origins and working of both the data encryption standard and advanced encryption standard are covered. We also look into the applications and differences between AES
From playlist Cyber Security Playlist [2023 Updated]🔥
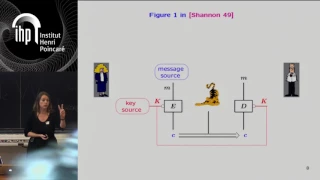
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100

25c3: Vulnerability discovery in encrypted closed source PHP applications
Speaker: Stefan Esser Security audits of PHP applications are usually performed on a source code basis. However sometimes vendors protect their source code by encrypting their applications with runtime (bytecode-)encryptors. When these tools are used source code analysis is no longer poss
From playlist 25C3: Nothing to hide

RSA and DSA Encryption Algorithms Explained | Cryptography & Network Security Tutorial | Simplilearn
In today's video on the RSA and DSA encryption algorithms explained, we cover the two most well known symmetric encryption algorithms in our cryptography & network security tutorial. We learn the steps needed to encrypt digital signatures and general data using RSA and DSA algorithms. The
From playlist Cyber Security Playlist [2023 Updated]🔥
