Symmetry and Quantum Electrodynamics (The Standard Model Part 1)
The Standard Model of Particle Physics is an absolutely incredible theory and a triumph of modern physics capable of explaining almost all of the physical phenomena we observe in nature. However, to understand it, we need to dive into some deep ideas including symmetry and how these relate
From playlist Standard Model

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

2022 I E Block Community Lecture: AI and Cryptography
July 13, 2022 How is Artificial Intelligence (AI) changing your life and the world? How can you expect your data to be kept secure and private in an AI-driven future? Kristin Lauter of Meta AI Research gives the I. E. Block Community Lecture titled "Artificial Intelligence and Cryptograph
From playlist SIAM Conference Videos

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Instance-Hiding Schemes for Private Distributed Learning -Sanjeev Arora
Seminar on Theoretical Machine Learning Topic: Instance-Hiding Schemes for Private Distributed Learning Speaker: Sanjeev Arora Affiliation: Princeton University; Distinguishing Visiting Professor, School of Mathematics Date: June 25, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

Cybersecurity Tutorial | Demo On Man In The Middle Attack | Cybersecurity Training | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl This "Cybersecurity tutorial" video presented by edureka gives an indepth information about the Cyber Security world and talks about its basic concepts.
From playlist Cyber Security Training for Beginners | Edureka

Complete Ethical Hacking Course | Ethical Hacking Training for Beginners | Edureka
🔥Certified Ethical Hacking Course - CEH v11 Training : https://www.edureka.co/ceh-ethical-hacking-certification-course 🔵 Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥 Ethical Hacking New Full Course video - 10 Hours: https://www.youtube.com/watch?v=dz7Ntp7KQGA This Edure
From playlist Cyber Security Training for Beginners | Edureka

Classical Verification of Quantum Computations - Urmila Mahadev
Computer Science/Discrete Mathematics Seminar I Topic: Classical Verification of Quantum Computations Speaker: Urmila Mahadev Affiliation: UC Berkeley Date: November 26, 2018 For more video please visit http://video.ias.edu
From playlist Mathematics

What is Man-in-the-Middle Attack | MITM Attack Explained | Edureka | Cybersecurity Rewind - 4
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "What is Man-in-the-Middle Attack" will help you understand what is Man-in-the-Middle Attack and how you can prevent it. Cybersecurity Training Playlist: https://bit.ly/2NqcTQ
From playlist Edureka Live Classes 2020
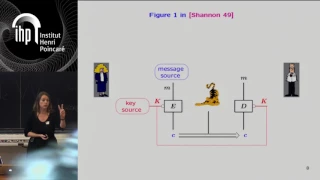
Shannon 100 - 26/10/2016 - Anne CANTEAUT
Comment concevoir un algorithme de chiffrement sûr et efficace : l'héritage de Shannon Anne Canteaut (INRIA) Dans son article fondateur publié en 1949 posant les fondements de la cryptographie, Claude Shannon a énoncé deux méthodes de conception visant à éviter les attaques statistiques
From playlist Shannon 100

GRCon21 - Rampart Communications: Cryptographic Modulation: Zero-Attack-Surface Wireless
Presented by Keith Palmisano at GNU Radio Conference 2021 Wireless communication is the fabric of modern connectivity, but no one thinks of wireless as inherently secure. Fundamentally, it’s a means of easily increasing access and mobility, but as much as we want high-speed no-drop 5G/wif
From playlist GRCon 2021

Efficient Verification of Computation on Untrusted Platforms - Yael Kalai
Computer Science/Discrete Mathematics Seminar I Topic: Efficient Verification of Computation on Untrusted Platforms Speaker: Yael Kalai Affiliation: Massachusetts Institute of Technology/Microsoft Date: February 13, 2023 Efficient verification of computation is fundamental to computer sc
From playlist Mathematics

Do Not Implement Your Own Crypto Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

GoGaRuCo 2012 - Modern Cryptography
Modern Cryptography by: John Downey Once the realm of shadowy government organizations, cryptography now permeates computing. Unfortunately, it is difficult to get correct and most developers know just enough to be harmful for their projects. Together, we’ll go through the basics of moder
From playlist gogaruco 2012