
For more cryptography, subscribe @JeffSuzukiPolymath
From playlist Elliptic Curves - Number Theory and Applications
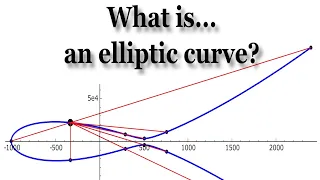
In this talk, we will define elliptic curves and, more importantly, we will try to motivate why they are central to modern number theory. Elliptic curves are ubiquitous not only in number theory, but also in algebraic geometry, complex analysis, cryptography, physics, and beyond. They were
From playlist An Introduction to the Arithmetic of Elliptic Curves

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security
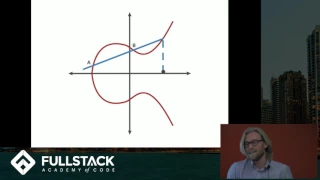
Elliptic Curve Cryptography Tutorial - Understanding ECC through the Diffie-Hellman Key Exchange
Learn more advanced front-end and full-stack development at: https://www.fullstackacademy.com Elliptic Curve Cryptography (ECC) is a type of public key cryptography that relies on the math of both elliptic curves as well as number theory. This technique can be used to create smaller, fast
From playlist Elliptic Curves - Number Theory and Applications

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

From playlist Cryptography Lectures

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Benjamin Smith, Isogenies in genus 2 for cryptographic applications
VaNTAGe seminar, October 4, 2022 License: CC-BY-NC-SA
From playlist New developments in isogeny-based cryptography

Mathematics in Post-Quantum Cryptography - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators

Bitcoin Q&A: Important Terminology Explained
I am confused by terminology in Bitcoin. Please explain the following terms: private / public keys, hash functions, elliptic curve, addresses, and signatures. How can you create an address offline? How does the Bitcoin network "find out" about the address? Chapters 0:00 I'm confused by th
From playlist Bitcoin Q&A

Mathematics in Post-Quantum Cryptography II - Kristin Lauter
2018 Program for Women and Mathematics Topic: Mathematics in Post-Quantum Cryptography II Speaker: Kristin Lauter Affiliation: Microsoft Research Date: May 22, 2018 For more videos, please visit http://video.ias.edu
From playlist My Collaborators

WRI TwitchTalks Cryptography 101719
Presenter: Dariia Porechna Wolfram Research developers demonstrate the new features of Version 12 of the Wolfram Language that they were responsible for creating. Previously broadcast live on October 17, 2019 at twitch.tv/wolfram. For more information, visit: https://www.wolfram.com/langu
From playlist Twitch Talks

!!Con 2016 - Making Money Disappear with Hash Functions! By Brendan Cordy
Making Money Disappear with Hash Functions! By Brendan Cordy What is a Bitcoin address? Where do all those weird letters and numbers come from!? Once we figure it out, we can dig deep between the cushions of the cryptocurrency couch and find lost coins claimed by bugs. You might think thi
From playlist RailsConf 2016

John Cremona: The symplectic type of congruences between elliptic curves
In this talk I will describe a systematic investigation into congruences between the mod $p$ torsion modules of elliptic curves defined over $\mathbb{Q}$. For each such curve $E$ and prime $p$ the $p$-torsion $E[p]$ of $E$, is a 2-dimensional vector space over $\mathbb{F}_{p}$ which carrie
From playlist Number Theory

Failing to Hash Into Supersingular Isogeny Graphs
CFAIL 2022. Authors: Jeremy Booher, Ross Bowden, Javad Doliskani, Tako Boris Fouotsa, Steven D. Galbraith, Sabrina Kunzweiler, Simon-Philipp Merz, Christophe Petit, Benjamin Smith, Katherine Stange, Yan Bo Ti, Christelle Vincent, José Felipe Voloch, Charlotte Weitkämper and Lukas Zobernig
From playlist My Math Talks

Kritin Lauter, Supersingular isogeny graphs in cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Charles, Goren, Lauter 2007: https://doi.org/10.1007/s00145-007-9002-x Mackenzie 2008: https://doi.org/10.1126/science.319.5869.1481 Pizer 1990: https://doi.org/10.1090/S0273-0979-1990-15
From playlist New developments in isogeny-based cryptography

