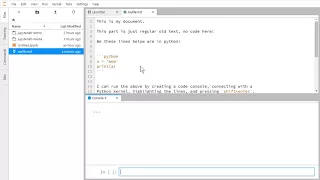
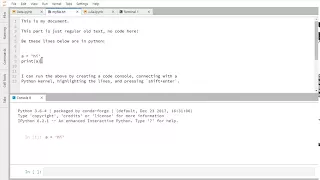
Signing - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

In this video, you’ll learn strategies for breaking down media messages to better understand their meaning. Visit https://edu.gcfglobal.org/en/digital-media-literacy/deconstructing-media-messages/1/ to learn even more. We hope you enjoy!
From playlist Digital Media Literacy

Determining the negation of a hypothesis and conclusion from a statement
👉 Learn how to find the negation of a statement. The negation of a statement is the opposite of the statement. It is the 'not' of a statement. If a statement is represented by p, then the negation is represented by ~p. For example, The statement "It is raining" has a negation of "It is not
From playlist Negation of a Statement

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

In this video, you’ll learn more about using Messages in LinkedIn. Visit https://edu.gcfglobal.org/en/linkedin/keeping-up-with-linkedin/1/ for our text-based lesson. We hope you enjoy!
From playlist LinkedIn

What is the negation of a statement and examples
👉 Learn how to find the negation of a statement. The negation of a statement is the opposite of the statement. It is the 'not' of a statement. If a statement is represented by p, then the negation is represented by ~p. For example, The statement "It is raining" has a negation of "It is not
From playlist Negation of a Statement
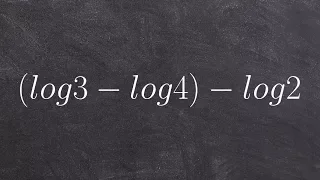
Condensing a logarithmic expression and simplifying the expression
👉 Learn how to condense logarithmic expressions. A logarithmic expression is an expression having logarithms in it. To condense logarithmic expressions means to use the logarithm laws to reduce logarithm expressions from the expanded form to a condensed form. Knowledge of the logarithm law
From playlist Condense Logarithms with Brackets

Stanford Seminar - Bugs in Crypto Implementations
Whether it’s by email, text, or social media platform, the average person will send over 60 messages per day—that's 22,000 messages per year. With billions of messages sent around the world each day, how can you be sure that your messages are safe and secure? Join professor Dan Boneh, on
From playlist Stanford Seminars