
Adeline Roux-Langlois : Using structured variants in lattice-based cryptography - Lecture 2
CONFERENCE Recording during the thematic meeting : « Francophone Computer Algebra Days» the March 07, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker : Guillaume Hennenfent Find this video and other talks given by worldwide mathematicians on CIR
From playlist Mathematical Aspects of Computer Science

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Mathematics of Post-Quantum Cryptograhy - Kristin Lauter
Woman and Mathematics - 2018 More videos on http"//video.ias.edu
From playlist My Collaborators
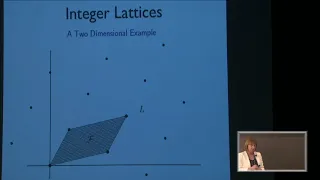
Mathematical Ideas in Lattice Based Cryptography - Jill Pipher
2018 Program for Women and Mathematics Topic: Mathematical Ideas in Lattice Based Cryptography Speaker: Jill Pipher Affiliation: Brown University Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

Adeline Roux-Langlois : Using structured variants in lattice-based cryptography - Lecture 1
CONFERENCE Recording during the thematic meeting : « Francophone Computer Algebra Days» the March 06, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Jean Petit Find this video and other talks given by worldwide mathematicians on CIRM's Audiov
From playlist Mathematical Aspects of Computer Science

Phong NGUYEN - Recent progress on lattices's computations 1
This is an introduction to the mysterious world of lattice algorithms, which have found many applications in computer science, notably in cryptography. We will explain how lattices are represented by computers. We will present the main hard computational problems on lattices: SVP, CVP and
From playlist École d'Été 2022 - Cohomology Geometry and Explicit Number Theory

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

From playlist Exploratory Data Analysis

2022 I E Block Community Lecture: AI and Cryptography
July 13, 2022 How is Artificial Intelligence (AI) changing your life and the world? How can you expect your data to be kept secure and private in an AI-driven future? Kristin Lauter of Meta AI Research gives the I. E. Block Community Lecture titled "Artificial Intelligence and Cryptograph
From playlist SIAM Conference Videos
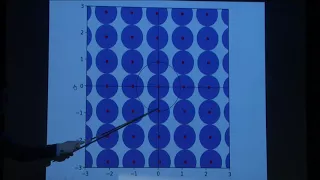
Lattices: from geometry to cryptography - Oded Regev
Ruth and Irving Adler Expository Lecture in Mathematics Topic: Lattices: from geometry to cryptography Speaker: Oded Regev Affiliation: New York University Date: November 29, 2017 For more videos, please visit http://video.ias.edu
From playlist Mathematics

The Year in Post-quantum Crypto
The world is finally catching on to the urgency of deploying post-quantum cryptography: cryptography designed to survive attacks by quantum computers. EVENT: media.ccc.de 2018 SPEAKERS: Daniel J. Bernstein and Tanja Lange PUBLICATION PERMISSIONS: Original video was published with the
From playlist Blockchain

Chris Peikert - Post Quantum assumptions - IPAM at UCLA
Recorded 27 July 2022. Chris Peikert of the University of Michigan presents "Post Quantum assumptions" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Learn more online at: https://www.ipam.ucla.edu/programs/summer-schools/graduate-summer-school-on-post-quantum-and-
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Secure Computation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Phong NGUYEN - Recent progress on lattices's computations 2
This is an introduction to the mysterious world of lattice algorithms, which have found many applications in computer science, notably in cryptography. We will explain how lattices are represented by computers. We will present the main hard computational problems on lattices: SVP, CVP and
From playlist École d'Été 2022 - Cohomology Geometry and Explicit Number Theory

Kritin Lauter, Supersingular isogeny graphs in cryptography
VaNTAGe Seminar, September 20, 2022 License: CC-BY-NC-SA Some of the papers mentioned in this talk: Charles, Goren, Lauter 2007: https://doi.org/10.1007/s00145-007-9002-x Mackenzie 2008: https://doi.org/10.1126/science.319.5869.1481 Pizer 1990: https://doi.org/10.1090/S0273-0979-1990-15
From playlist New developments in isogeny-based cryptography

