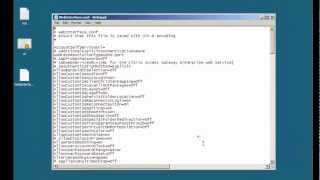
Citrix : Web Interface website for the Citrix Access Gateway
More videos like this online at http://www.theurbanpenguin.com Here we take a look at creating a Citrix Web Interface web site to support the Citrix Access Gateway. In doing so we will also look at the importance of backing up the webinterface.conf and using that as a template fro new site
From playlist Citrix
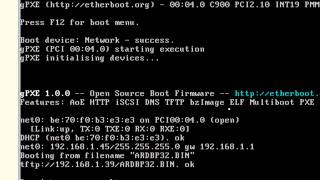
CITRIX: Provisioning Services - Assigning vDisks to users
More videos like this on http://www.theurbanpenguin.com : In this short presentation we look at Citrix Provisioning Services and assigning vDisks to user groups.
From playlist Citrix

Citrix : Web Interface enabling HTTPS
More videos like this online at http://www.theurbanpenguin.com In this video we take a look at enabling HTTPS access with SSL to the WebInterface Server. With the later Citrix Receivers HTTPS is becoming the Protocol of choice and certainly when used with the Citrix Access Gateway we shoul
From playlist Citrix
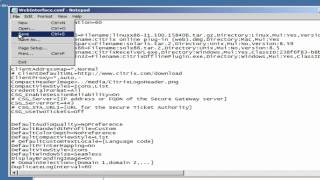
Citrix : Using the Web Interface to deliver clients
More videos like this can be found at http://www.theurbanpenguin.com This is just a quick step though in delivering the Citrix Receiver via the Web interface that ships with XenApp 6.5. It does mean an edit to the WebInterface.Conf as the change is not exposed in the Web Console.
From playlist Citrix

What is DevOps? | DevOps Introduction | DevOps Tools | DevOps Tutorial For Beginners | Simplilearn
🔥DevOps Engineer Master Program (Discount Code: YTBE15): https://www.simplilearn.com/devops-engineer-masters-program-certification-training?utm_campaign=WhatisDevops-CIK-pVOCV4E&utm_medium=DescriptionFF&utm_source=youtube 🔥Post Graduate Program In DevOps: https://www.simplilearn.com/pgp-d
From playlist DevOps Tutorial For Beginners 🔥 | Simplilearn [Updated]
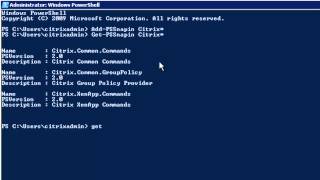
More videos like this online at http://www.theurbanpenguin.com if you are looking to make a start with PowerShell this may help you on your way using PowerShell with Citrix XenApp. We look at how you can list command by the module and the associated verb or noun
From playlist Citrix

Building A Trading Bot On Interactive Broker TWS API via QuantConnect | Session 01 | #programming
Don’t forget to subscribe! This project series is about building and backtesting a trading bot on interactive broker TWS API via QuantConnect. Building an Insider Trading Activity Stocks/ETFs Trading Bot on Interactive Broker TWS API then backtesting and forward-testing it using both Pyt
From playlist Building A Trading Bot On Interactive Broker TWS API via QuantConnect

CITRIX: License Server Install
More videos like this on http://www.theurbanpenguin.com : In this video we look at installing the Licensing Server to use with Citrix XenApp. We install on Server 2008 R2 and view the ports in use with netsat and resource monitor once complete
From playlist Citrix

QTL and Association mapping by Bruce Walsh
Second Bangalore School on Population Genetics and Evolution URL: http://www.icts.res.in/program/popgen2016 DESCRIPTION: Just as evolution is central to our understanding of biology, population genetics theory provides the basic framework to comprehend evolutionary processes. Population
From playlist Second Bangalore School on Population Genetics and Evolution
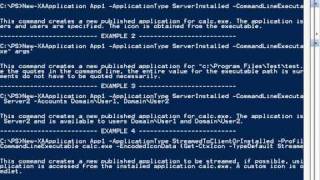
PowerShell: XenApp 6 Integration
More videos like this on http://www.theurbanpenguin.com : PowerShell simply cannot be ignored. Its power within Microsoft has been utilized for several years now and we are seeing increased third-pary support. Citris supply PowerShell Modules to manage there RD systems as standard with X
From playlist Citrix

Physics 50. Math Methods. Lecture 3.1
UCI Physics 50: Math Methods (Spring 2014). Lec 3.1. Math Methods -- Matrices -- View the complete course: http://ocw.uci.edu/courses/physics_50_math_methods.html Instructor: Micahel Dennin, Ph.D. License: Creative Commons CC-BY-SA Terms of Use: http://ocw.uci.edu/info. More courses at ht
From playlist Physics 50: Math Methods
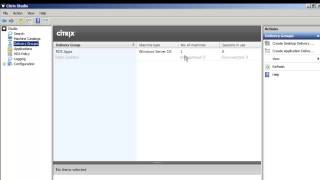
Citrix : Publishing Server and Desktop Application with Exaclibur
More videos like this online at http://www.theurbanpenguin.com . So now we take a look at how we can publish applications from or Desktop or Server machines using Citrix Studio in the Excalibur project, the next generation XenApp and XenDesktop. CReating a Application Delivery Group and ad
From playlist Citrix

Citrix XenDesktop 5 CCA Licensing
More videos like this online at http://www.theurbanpenguin.com In this video we look at licensing of XenDesktop 5 and the licensing server. Even the free Express Edition required licenses. The License server can be shared between XenApp and XenDesktop
From playlist Citrix XenDesktop 5 CCA

Ilya Dumanski - Schubert varieties in the Beilinson-Drinfeld Grassmannian
Ilya Dumanski (MIT) The Borel-Weil theorem states that the space of sections of a certain line bundle on the flag variety is isomorphic to the irreducible representation of the corresponding reductive group. The classical result of Demazure describes the restriction of sections to the Sch
From playlist Azat Miftakhov Days Against the War

Breaking enen barrier...Monomer-Dimer Entropy - Leonid Gurvits
Leonid Gurvits City University of New York September 29, 2014 Two important breakthroughs on the permanent had been accomplished in 1998: A. Schrijver proved Schrijver-Valiant Conjecture on the minimal exponential growth of the number of perfect matchings in k-regular bipartite graphs wit
From playlist Mathematics

EEVblog #642 - TI Connected Launchpad
Dave checks out the $20 TI EK-TM4C1294XL Tiva C Series TM4C1294 Connected Launchpad Internet of Things. ARM Cortex M4 processor with Ethernet and IoT demo application. http://www.ti.com/ww/en/launchpad/launchpads-connected-ek-tm4c1294xl.html How useful is it out of the box? http://www.eev
From playlist Arduino & Microcontrollers

Citrix : XenServer xe vm-import from Windows
More videos like this online at http://www.theurbanpenguin.com In this video we look at using xe.exe and vm-import to import a virtual machine appliacance into our Citrix XenServer host. XE is part of the XenCeter install on windows and we can access in the %PROGRAMFILES%\Citrix\XenCenter
From playlist Citrix

Mirror symmetry for complex projective space and optimal towers of algebraic curves by Sergey Galkin
Date/Time: Monday, March 2, 4:00 pm Title: Mirror symmetry for complex projective space and optimal towers of algebraic curves Abstract: I will speak about mirror symmetry for projective threespace, and how with Sergey Rybakov we used it to construct an optimal tower of algebraic curves
From playlist Seminar Series

