
Toy Substitution Cipher 2 Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

From playlist Week 2 2015 Shorts

MATH3411 Information, Codes and Ciphers This problem presents RSA encryption and asks us to use this scheme to encipher a message and to decipher a received message. We see that this is very easy and straight-forward. Presented by Thomas Britz, School of Mathematics and Statistics, Facul
From playlist MATH3411 Information, Codes and Ciphers

From playlist Week 2 2015 Shorts

Rsa Encryption - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography
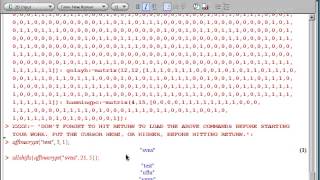
How to encrypt and decrypt the affine cipher using Maple software. Code from Into to Crypto and Coding Theory 2nd ed. by W. Trappe and LC Washington.
From playlist Cryptography and Coding Theory

Rsa Encryption Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

My stream schedule has changed, I will be skipping the morning stream and instead be keeping to the Sunday streams. When I have time I'll be streaming after work, but no set schedule at this time.
From playlist Channel updates

Early Silk Road | World History | Khan Academy
The early Silk Roads facilitated trade and the spread of ideas, technology, disease and religion across Eurasia in the beginning of the Common Era. Practice this yourself on Khan Academy right now: https://www.khanacademy.org/humanities/world-history/ancient-medieval/silk-road/e/key-conce
From playlist 600 BCE - 600 CE Second-Wave Civilizations | AP World History | Khan Academy

Fast, Furious and Insecure: Hacking Tesla S
Our research revealed several weaknesses in the Tesla Model S passive keyless entry and start system. The talk will be a comprehensive overview of how we reverse engineered the key fob, the issues we found and an efficient proof of concept attack. The proof of concept attack exploits the u
From playlist Security

Keeping Secrets: Cryptography In A Connected World
Josh Zepps, Simon Singh, Orr Dunkelman, Tal Rabin, and Brian Snow discuss how, since the earliest days of communication, clever minds have devised methods for enciphering messages to shield them from prying eyes. Today, cryptography has moved beyond the realm of dilettantes and soldiers to
From playlist Explore the World Science Festival

Cryptanalysis of Vigenere cipher: not just how, but why it works
The Vigenere cipher, dating from the 1500's, was still used during the US civil war. We introduce the cipher and explain a standard method of cryptanalysis based on frequency analysis and the geometry of vectors. We focus on visual intuition to explain why it works. The only background
From playlist Classical Cryptography

The Greatest Forms Of Self Defense In The 20th Century [4K] | The Greatest Ever | Spark
Fast paced head-spinning, and informative, Greatest Ever is a top ten count down of the marvels of modern technology. You may not agree, but you'll be grabbed and not let go as our picks are put through their paces in front of our cameras. -- Subscribe to Spark for more amazing science, te
From playlist The Greatest Ever

Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Who Will Be Driving on the Highway of the Future? with Chris Gerdes
Watch, learn and connect: https://stanfordconnects.stanford.edu/ Sharing some of the exciting work happening at Stanford around self-driving cars, Professor Chris Gerdes highlights the student-built P1 vehicle and Shelley, an Audi TTS. He emphasizes the importance of safety and the role of
From playlist STANFORD+CONNECTS

Math for Liberal Studies - Lecture 3.8.2 A Brief Discussion of Public-Key Cryptography
This is the second video lecture for Math for Liberal Studies, Section 3.8: More Modular Arithmetic and Public-Key Cryptography. In this lecture, I give you a brief overview of how we can use multiplicative ciphers in a public-key cryptography system. I also give a few examples of the secu
From playlist Math for Liberal Studies Lectures

MATH3411 Information, Codes and Ciphers This problem presents digital signatures via the DSS scheme. We are asked to find a public key from a private key, to generate a digital signature, and to check the validity of a received signature. Presented by Thomas Britz, School of Mathematics
From playlist MATH3411 Information, Codes and Ciphers
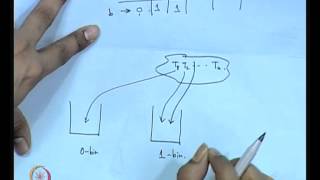
Side Channel Analysis of Cryptographic Implementations
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security