
Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

ADFGVX Cipher: Encryption and Decryption (Updated)
Encryption and Decryption of the World War One ADFGVX Cipher, through examples. This video replaces an earlier one with the same content, but has some improvements and corrections. #cryptography
From playlist Classical Cryptography

Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Re-coating a VERY LARGE telescope mirror
How are the four 8.2m mirrors at the Very Large Telescope moved and re-coated with aluminium? More form the VLT: http://bit.ly/VLT_Playlist Filmed at the European Southern Observatory's site at Paranal, Chile. Deep Sky Videos website: http://www.deepskyvideos.com/ Twitter: https://twitte
From playlist Inside the VLT

ADFGVX Cipher: Encryption and Decryption (OLD VERSION: SEE NEW VERSION LINK BELOW)
This video has been replaced with an updated video: visit https://youtu.be/T0xfKiU9Rr4 Encryption and Decryption of the World War One ADFGVX Cipher, through examples.
From playlist Classical Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

From playlist Week 2 2015 Shorts

When do you know if a relations is in linear standard form
👉 Learn how to determine if an equation is a linear equation. A linear equation is an equation whose highest exponent on its variable(s) is 1. The variables do not have negative or fractional, or exponents other than one. Variables must not be in the denominator of any rational term and c
From playlist Write Linear Equations

👉 Learn about graphing linear equations. A linear equation is an equation whose highest exponent on its variable(s) is 1. i.e. linear equations has no exponents on their variables. The graph of a linear equation is a straight line. To graph a linear equation, we identify two values (x-valu
From playlist ⚡️Graph Linear Equations | Learn About
Johannes Nicaise: The non-archimedean SYZ fibration and Igusa zeta functions - part 3/3
Abstract : The SYZ fibration is a conjectural geometric explanation for the phenomenon of mirror symmetry for maximal degenerations of complex Calabi-Yau varieties. I will explain Kontsevich and Soibelman's construction of the SYZ fibration in the world of non-archimedean geometry, and its
From playlist Algebraic and Complex Geometry

How To Write The Equation of a Line Given The Slope and a Point | Algebra
This algebra video tutorial explains how to write the equation of the line that passes through a point given a certain slope value. This video explains how to write the linear equation in slope-intercept form, in standard form, as well as in point slope form.
From playlist New Algebra Playlist

Hello all Happy Wednesday 3rd June 2020. Hope everyone is doing okay. Today's video looks st the remaining rules of circle theorem. Quick note. Aimed at higher tier GCSE. Thank you for watching, please as ever, subscribe to my channel, drop the video a like, enable notifications by pre
From playlist GCSE Maths!!

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
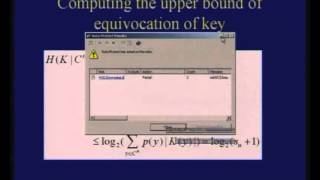
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Summary for graph an equation in Standard form
👉 Learn about graphing linear equations. A linear equation is an equation whose highest exponent on its variable(s) is 1. i.e. linear equations has no exponents on their variables. The graph of a linear equation is a straight line. To graph a linear equation, we identify two values (x-valu
From playlist ⚡️Graph Linear Equations | Learn About

What is Bill Cipher? (Scientific Analysis)
What is Bill Cipher? Today we discover the very very confusing science of what Gravity Fall's Bill Cipher is. =======WARNING VERY VERY CONFUSING======= This video talks about dimensions and alternate universes. Your mind might explode! Sources: -http://en.wikipedia.org/wiki/Four-dim...
From playlist Scientific Videos