
Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

From playlist Week 2 2015 Shorts

Classify a polynomial then determining if it is a polynomial or not
👉 Learn how to determine whether a given equation is a polynomial or not. A polynomial function or equation is the sum of one or more terms where each term is either a number, or a number times the independent variable raised to a positive integer exponent. A polynomial equation of functio
From playlist Is it a polynomial or not?

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Determining if a equation is a polynomial or not
👉 Learn how to determine whether a given equation is a polynomial or not. A polynomial function or equation is the sum of one or more terms where each term is either a number, or a number times the independent variable raised to a positive integer exponent. A polynomial equation of functio
From playlist Is it a polynomial or not?
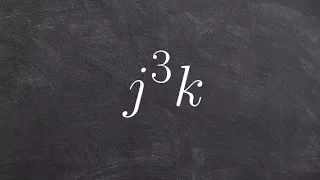
Is it a polynomial with two variables
👉 Learn how to determine whether a given equation is a polynomial or not. A polynomial function or equation is the sum of one or more terms where each term is either a number, or a number times the independent variable raised to a positive integer exponent. A polynomial equation of functio
From playlist Is it a polynomial or not?

Cyber Security Week Day - 1 |Cryptography Full Course | Cryptography & Network Security| Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp This video on Cryptography full course will acquaint you with cryptograph
From playlist Simplilearn Live

Cryptography Full Course | Cryptography And Network Security | Cryptography | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=CryptographyFCAug17&utm_medium=DescriptionFirstFold&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity
From playlist Simplilearn Live

🔥Cryptography And Network Security Full Course 2022 | Cryptography | Network Security | Simplilearn
🔥Free Cyber Security Course With Completion Certificate: https://www.simplilearn.com/learn-cyber-security-basics-skillup?utm_campaign=CryptographyNetworkSecurityFC4Aug22&utm_medium=DescriptionFirstFold&utm_source=youtube This video on the Cryptography and network security full course will
From playlist Simplilearn Live

Learn how to identify if a function is a polynomial and identify the degree and LC
👉 Learn how to determine whether a given equation is a polynomial or not. A polynomial function or equation is the sum of one or more terms where each term is either a number, or a number times the independent variable raised to a positive integer exponent. A polynomial equation of functio
From playlist Is it a polynomial or not?

The Art and Science of Secret Messages: Some Glimpses (ONLINE) by Geetha Venkataraman
KAAPI WITH KURIOSITY THE ART AND SCIENCE OF SECRET MESSAGES: SOME GLIMPSES (ONLINE) SPEAKER: Geetha Venkataraman (Dr. B. R. Ambedkar University Delhi, Delhi) WHEN: 4:00 pm to 5:30 pm Sunday, 19 September 2021 WHERE: Livestream via the ICTS YouTube channel Abstract:- In the modern worl
From playlist Kaapi With Kuriosity (A Monthly Public Lecture Series)

Affine Cipher - Decryption (Known Plaintext Attack)
In this video I talk about ways to decrypt the Affine Cipher when the key is NOT known. Specifically, I go over an example of the known plaintext attack. 3^(-1) = 9 (mod 26) math worked out (Euclidean Algorithm): 1. Forwards: 26 = 3(8) + 2 3 = 2(1) + 1 2. Backwords: 1 = 3 -
From playlist Cryptography and Coding Theory
What is Cryptography? | Introduction to Cryptography | Cryptography for Beginners | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl Cryptography is essential to protect the information shared across the internet. This video on What is cryptography explaines you the fundamental concep
From playlist Cyber Security Training for Beginners | Edureka

DEFCON 18: Tales from the Crypt 1/4
Speaker: G. Mark Hardy Learn how to crack crypto contests like a pro. The speaker has awarded half a dozen free round-trip plane tickets to previous contest winners. Maybe you'll be next. From the daily newspaper puzzle to badge contests to codes that keep the National Security Agency a
From playlist DEFCON 18-1

From playlist Week 2 2015 Shorts

Perfect Cipher - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
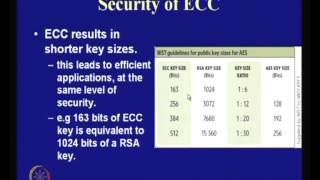
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security