Pretty Good Privacy
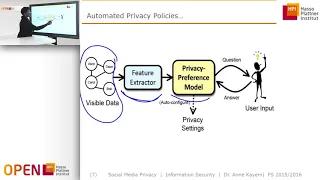
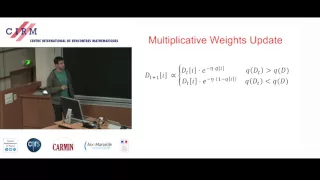
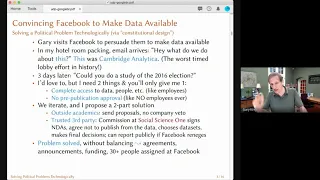
Pretty Good Privacy (PGP) is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991. PGP and similar software follow the , an open standard of PGP encryption software, standard (RFC 4880) for encrypting and decrypting data. (Wikipedia).