
Network Security: Classical Encryption Techniques
Fundamental concepts of encryption techniques are discussed. Symmetric Cipher Model Substitution Techniques Transposition Techniques Product Ciphers Steganography
From playlist Network Security

Network Security, Part 2 : Public Key Encryption
Fundamental concepts of public key encryption are discussed. RSA encryption method explained with an example. Confidentiality of message is presented.
From playlist Cryptography, Security

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Encryption Explained Simply | What Is Encryption? | Cryptography And Network Security | Simplilearn
In today's video on encryption explained simply, we take a look at why cryptography is essential when it comes to protecting our privacy on the internet. We take a look at how what is encryption, how encryption and decryption works with simple step by step explanation, and move onto it's c
From playlist Cyber Security Playlist [2023 Updated]🔥

Best secure and private email services review - guide to Gmail alternatives and encrypted email
Secure your privacy and claim a new encrypted email at these secure and private email services. Follow my guide to gmail alternatives and end-to-end encryption using private email providers as part of degoogleify campaign. I made this channel because I believe standing up against power an
From playlist TUTORIALS & HOW TO's

Is ProtonMail lying about their encryption? In response to Nadim Kobeissi and LiveOverflow
As the most popular encrypted email provider, ProtonMail has been criticized for false security promises and weak guarantees of its end-to-end encryption infrastructure. Can be ProtonMail's marketing of their Swiss-based email service justified? The results might SHOCK you! These are encr
From playlist Analyses
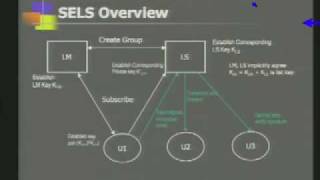
CERIAS Security: Minimizing Trust Liabilities in Secure Group Messaging Infrastructures 2/5
Clip 2/5 Speaker: Himanshu Khurana · University of Illinois at Urbana-Champaign Large-scale collaborative applications are characterized by a large number of users and other processing end entities that are distributed over geographically disparate locations. Therefore, these applicat
From playlist The CERIAS Security Seminars 2005 (1)

GORUCO 2018: Encryption Pitfalls and Workarounds by Melissa Wahnish
GORUCO 2018: Encryption Pitfalls and Workarounds by Melissa Wahnish
From playlist GORUCO 2018

Digital security PART 2 - how to protect yourself on the Internet
Part 2 of the digital security talk with Daniel from Safing.io. In this part, we discuss specific tools and strategies you can use to enhance your security online. Support me through Patreon: https://www.patreon.com/thehatedone - or donate anonymously: Monero: 84DYxU8rPzQ88SxQqBF6VBNf
From playlist TUTORIALS & HOW TO's

CERIAS Security: Minimizing Trust Liabilities in Secure Group Messaging Infrastructures 1/5
Clip 1/5 Speaker: Himanshu Khurana · University of Illinois at Urbana-Champaign Large-scale collaborative applications are characterized by a large number of users and other processing end entities that are distributed over geographically disparate locations. Therefore, these applicat
From playlist The CERIAS Security Seminars 2005 (1)

Computer Security | What Is Computer Security | Cyber Security Tutorial | Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security?utm_campaign=ComputerSecurity-cs3B0zcRJco&utm_medium=Descriptionff&utm_source=youtube 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecuri
From playlist Cyber Security Playlist [2023 Updated]🔥

This is how companies read your emails and why you need end-to-end encryption
Apple, Google, Microsoft and Yahoo all reserve the right to read your emails not just through machines, but by their employees too. Contents of your emails are for sale and scrutiny by poorly vetted actors, unless you start using end-to-end encryption and switch to secure email providers l
From playlist Analyses

Cyber Security Week Day - 4 | Cyber Security Interview Questions And Answers 2021 | Simplilearn
🔥Free Cyber Security Course: https://www.simplilearn.com/learn-cyber-security-basics-skillup?utm_campaign=CSWEEKNOV5&utm_medium=DescriptionFirstFold&utm_source=youtube This Simplilearn video on Cyber Security Interview Questions And Answers acquaints you with the top cyber security intervi
From playlist Simplilearn Live

Edureka Ethical Hacking Webinar | Ethical Hacking Tutorial For Beginners | Edureka Masterclass
(Edureka Meetup Community: http://bit.ly/2DQO5PL) Join our Meetup community and get access to 100+ tech webinars/ month for FREE: http://bit.ly/2DQO5PL Topics to be covered in this session: 1. What is Hacking? 2. What is Ethical Hacking? 3. How Does Ethical Hacking Work? 4. Hands-On Know
From playlist Webinars by Edureka!

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

