
Which Incapacitating Agent is the Most Effective?
This time, we're ranking incapacitating agents! The term incapacitating agent is defined by the United States Department of Defense as: "An agent that produces temporary physiological or mental effects, or both, which will render individuals incapable of concerted effort in the performance
From playlist Chemistry Tierlists

Invasion of Iraq: How the British and Americans got it wrong
Strategy of the Iraq invasion by US and UK armies/politicians
From playlist History and Biographies

Luftwaffe BF110 Zerstorer - Battle of Kursk Aug 1943
Bf110 aircraft at the Battle of Kursk.
From playlist WW2 aircrafts

Is A DOS Attack A Weapon? | Idea Channel | PBS Digital Studios
Viewers like you help make PBS (Thank you 😃) . Support your local PBS Member Station here: https://to.pbs.org/donateidea Here's an idea: a DOS attack is a weapon. Denial of Service (DOS) or Distributed Denial of Service (DDOS) attacks take down servers by distracting them with meaningles
From playlist Newest Episodes

First the motorcycles are riding together, but then the farmer's motorcycle turns left
From playlist Stop Motion

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

M16 vs AK-47: Which One Would You Pick?
There are very few weapons in the world that are compared as often as the AK-47 and the M16. For more than 60 years, these two rival brothers fought for supremacy over each other on dozens of battlefields. They became the poster boys for conflict and warfare. They have more similarities
From playlist Combat Tech

Alain Couvreur - Comment domestiquer les codes de Goppa sauvages?
Le schéma de McEliece est un schéma de chiffrement basé sur les codes correcteurs d'erreurs dont la sécurité repose sur la difficulté à décoder un code aléatoire. Parmi les différentes familles de codes algébriques proposées pour ce schéma, les codes de Goppa classiques sont les seuls à ré
From playlist Journées Codage et Cryptographie 2014

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography
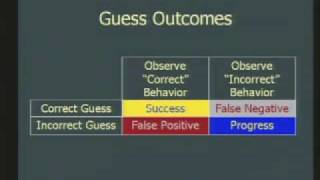
CERIAS Security: Instruction Set Randomization (ISR) 2/6
Clip 2/6 Speaker: David Evans · University of Virginia Instruction Set Randomization (ISR) has been proposed as a promising defense against code injection attacks. It defuses all standard code injection attacks since the attacker does not know the instruction set of the target machine.
From playlist The CERIAS Security Seminars 2005 (1)

27c3: News Key Recovery Attacks on RC4/WEP (en)
Speaker: Martin Vuagnoux In this paper, we present several weaknesses in the stream cipher RC4. First, we present a technique to automatically reveal linear correlations in the PRGA of RC4. With this method, 48 new exploitable correlations have been discovered. Then we bind these new b
From playlist 27C3: We come in peace

Black Hat USA 2010: Exploiting Timing Attacks in Widespread Systems 3/5
Speakers: Nate Lawson, Taylor Nelson Much has been written about timing attacks since they first appeared over 15 years ago. However, many developers still believe that they are only theoretically exploitable and don't make it a priority to fix them. We have notified vendors who declined
From playlist BH USA 2010 - NETWORK

DP-SGD Privacy Analysis is Tight!
A Google TechTalk, presented by Milad Nasr, 2020/08/21 ABSTRACT: Differentially private stochastic gradient descent (DP-SGD) provides a method to train a machine learning model on private data without revealing anything specific to that particular dataset. As a tool, differential privacy
From playlist Differential Privacy for ML

25c3: RF fingerprinting of RFID
Speakers: cryptocrat, Boris Danev In the lecture portion of this workshop we will present an overview of existing and our own novel methods for hacking electronic passports and driver's licenses including novel radio frequency fingerprinting techniques. In the the hands-on section we wi
From playlist 25C3: Nothing to hide

Mathematics of Post-Quantum Cryptograhy - Kristin Lauter
Woman and Mathematics - 2018 More videos on http"//video.ias.edu
From playlist My Collaborators

Kristin Lauter, Microsoft Research Redmond The Mathematics of Modern Cryptography http://simons.berkeley.edu/talks/kristin-lauter-2015-07-07
From playlist My Collaborators

Overview on Modern Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

The Generalization War: The Rise of General Fibonach
This is a response...nay! a RETALIATION video against General Papa Flamdameroo for his assault on our senses with the (honestly fantastic) generalization of the Gaussian Intägarahl, seen here: https://www.youtube.com/watch?v=BdnxgFO-3VM I challenge YOU, Papa, to a generalization-off, wher
From playlist The Generalization War
