
Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Combination Locks - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Randomness Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Pairwise Distribution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
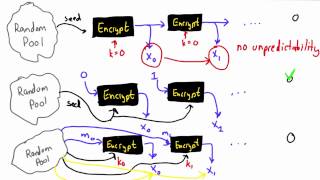
Pseudo Random Number Generator Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
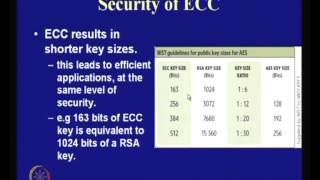
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Zoé Amblard - Cryptographie quantique, intrication et violations du réalisme local...
Cryptographie quantique, intrication et violations du réalisme local pour les systèmes tridimensionnels
From playlist Journées Codage et Cryptographie 2014

WRI TwitchTalks Cryptography 101719
Presenter: Dariia Porechna Wolfram Research developers demonstrate the new features of Version 12 of the Wolfram Language that they were responsible for creating. Previously broadcast live on October 17, 2019 at twitch.tv/wolfram. For more information, visit: https://www.wolfram.com/langu
From playlist Twitch Talks
What is Cryptography? | Introduction to Cryptography | Cryptography for Beginners | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl Cryptography is essential to protect the information shared across the internet. This video on What is cryptography explaines you the fundamental concep
From playlist Cyber Security Training for Beginners | Edureka

Speaker: Stephanie Wehner An introduction Entanglement is possibly the most intriguing element of quantum theory. This talk gives a gentle introduction to the phenomenon of entanglement and nonlocality. Uses of entanglement in quantum cryptography and quantum computing are also presente
From playlist 22C3: Private Investigations

In the modern world, cryptography is omnipresent. In this talk, Dariia Porechna will introduce recent and future developments to Wolfram Language cryptography functionality in the areas of digital signing and key and certificate management, as well as discussing efforts in teaching cryptog
From playlist Wolfram Technology Conference 2020

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Elliptic Curve Cryptography and Applications
At the SIAM Annual Meeting held in Minneapolis in July, Dr. Kristin Lauter of Microsoft Research discussed Elliptic Curve Cryptography as a mainstream primitive for cryptographic protocols and applications. The talk surveyed elliptic curve cryptography and its applications, including appli
From playlist What is math used for?

Roberto La Scala, Università di Bari
Roberto La Scala, Università di Bari Ciphers and difference equations
From playlist Spring 2021 Online Kolchin Seminar in Differential Algebra

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Mathematics in Cryptography II - Toni Bluher
2018 Program for Women and Mathematics Topic: Mathematics in Cryptography II Speaker: Toni Bluher Affiliation: National Security Agency Date: May 21, 2018 For more videos, please visit http://video.ias.edu
From playlist Mathematics

