
Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Fundamental concepts of intrusion detection are discussed. Various types of intrusion are analyzed. Password management is explained.
From playlist Network Security

Tutorial: GeoHTTP Remote Buffer Overflow and DoS
A real example of a Buffer Overflow/Denial of Service attack! My favorite video: http://www.youtube.com/watch?v=z00kuZIVXlU Visit http://binslashshell.wordpress.com and join our forum community!!! This is a video showing what a Buffer Overflow Aattck can do to a Web Server. For th
From playlist Denial of Service attacks
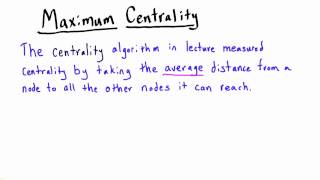
Centrality - Intro to Algorithms
This video is part of an online course, Intro to Algorithms. Check out the course here: https://www.udacity.com/course/cs215.
From playlist Introduction to Algorithms

Cipher Block Chaining Mode - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Challenge Question - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Manifold Mixup: Better Representations by Interpolating Hidden States
Standard neural networks suffer from problems such as un-smooth classification boundaries and overconfidence. Manifold Mixup is an easy regularization technique that rectifies these problems. It works by interpolating hidden representations of different data points and then train them to p
From playlist Deep Learning Architectures

Toy Substitution Cipher 2 Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Eavesdropper - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Mod-01 Lec-01 Introduction and Overview
Advanced Numerical Analysis by Prof. Sachin C. Patwardhan,Department of Chemical Engineering,IIT Bombay.For more details on NPTEL visit http://nptel.ac.in
From playlist IIT Bombay: Advanced Numerical Analysis | CosmoLearning.org

Near-optimal Evasion of Randomized Convex-inducing Classifiers in Adversarial Environments | AISC
For slides and more information on the paper, visit https://aisc.a-i.science/events/2019-05-23 Discussion lead: Pooria Madani Motivation: Classifiers are often used to detect malicious activities in adversarial environments. Sophisticated adversaries would attempt to find information a
From playlist Generative Models

RailsConf 2015 - Metasecurity: Beyond Patching Vulnerabilities
by Chase Douglas Rails comes with many powerful security protections out of the box, but no code is perfect. This talk will highlight a new approach to web app security, one focusing on a higher level of abstraction than current techniques. We will take a look at current security processe
From playlist RailsConf 2015

Engineering CEE 20: Engineering Problem Solving. Lecture 20
UCI CIvil & Environmental Engineering 20 Engineering Problem Solving (Spring 2013) Lec 20. Engineering Problem Solving View the complete course: http://ocw.uci.edu/courses/cee_20_introduction_to_computational_engineering_problem_solving.html Instructor: Jasper Alexander Vrugt, Ph.D. Licen
From playlist Engineering CEE 20: Engineering Problem Solving

Strata Summit 2011: Marc Goodman, "The Business Of Illegal Data..."
While businesses around the world struggle to understand the how to profit from the information revolution, one class of enterprise has successfully mastered the challenge—international organized crime. Globally crime groups are rapidly transforming themselves into consumers of big data. L
From playlist Strata NY 2011

Guido Kings: Motivic Eisenstein cohomology, p-adic interpolation and applications
The lecture was held within the framework of the Hausdorff Trimester Program: K-Theory and Related Fields. Guido Kings: Motivic Eisenstein cohomology, p-adic interpolation and applications Abstract: Motivic Eisenstein classes have been defined in various situations, for example for G =
From playlist HIM Lectures: Trimester Program "K-Theory and Related Fields"

CIC News 07-01-2014: Malware warnings | Interpol office Singapore | OpenSSL defacement
Sources: How to make malware warnings more effective?: http://bit.ly/CIC140107-1 Interpol cybercrime office taps Japanese: http://bit.ly/CIC140107-2 YouTube INTERPOL GLOBAL COMPLEX FOR INNOVATION: http://bit.ly/CIC140107-3 How did OpenSSL's home page get defaced?: http://zd.net/19NnLDG Mo
From playlist Vlogs

How Do JavaScript Frameworks Impact the Security of Applications?
The best way to enable developers to create secure applications is to “shift left” in security. That means providing developers with the tools and techniques that help build more secure applications from the get-go. Developers may get security controls into their applications in different
From playlist JavaScript

SYN Flood Denial of Service attack using perl script and hping3 tool.
From playlist Denial of Service attacks

Mark Giesbrecht 4/23/15 Part 2
Title: I. Approximate Computation with Differential Polynomials: Approximate GCRDs II. Sparsity, Complexity and Practicality in Symbolic Computations Symbolic-Numeric Computing Seminar
From playlist Symbolic-Numeric Computing Seminar
