
Some Comments on the Security of RSA
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

28C3: Introducing Osmo-GMR (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: Sylvain Munaut Building a sniffer for the GMR satphones The latest member of the Osmocom-family projects, osmo-gm
From playlist 28C3: Behind Enemy Lines

Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography

Two Way Radio - FCC, FRS, GMRS, MURS, CB and DMR (MotoTRBO-Digital) - Pt3
Please support my content creation by using my Amazon Store: http://astore.amazon.com/m0711-20 Or anything on Amazon: http://www.amazon.com/?_encoding=UTF8&camp=212353&creative=380557&linkCode=sb1&tag=m0711-20 ------------------------------ Click "Show more" -------------------------------
From playlist Consumer Reviews - Two-way radios FCC, FRS, GMRS, MURS, CB

Two Way Radio - FCC, FRS, GMRS, MURS, CB and DMR (MotoTRBO-Digital) - Pt1
Please support my content creation by using my Amazon Store: http://astore.amazon.com/m0711-20 Or anything on Amazon: http://www.amazon.com/?_encoding=UTF8&camp=212353&creative=380557&linkCode=sb1&tag=m0711-20 ------------------------------ Click "Show more" -------------------------------
From playlist Consumer Reviews - Two-way radios FCC, FRS, GMRS, MURS, CB

Two Way Radio - FCC, FRS, GMRS, MURS, CB and DMR (MotoTRBO-Digital) - Pt2
Please support my content creation by using my Amazon Store: http://astore.amazon.com/m0711-20 Or anything on Amazon: http://www.amazon.com/?_encoding=UTF8&camp=212353&creative=380557&linkCode=sb1&tag=m0711-20 ------------------------------ Click "Show more" -------------------------------
From playlist Consumer Reviews - Two-way radios FCC, FRS, GMRS, MURS, CB

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

GRCon21 - Lightning Talk - Deepwave Digital: Artificial Intelligence Radio Transceiver with ...
Lightning Talk - Deepwave Digital: Artificial Intelligence Radio Transceiver with on-board GPU presented by Jeff Zurita at GNU Radio Conference 2021
From playlist GRCon 2021

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Two Way Radio Review / Range Tests - Part 1
Review and tests of 10 two-way radios, FCC and licensing. Full review data and links here: http://www.mjlorton.com/two-way-radio-handset-handy-talkies-hts-tests-walkie-talkies-the-results/ ------------------------------ Click "Show more" ------------------------------------------- Motorola
From playlist Two-Way Radio Review

Two Way Radio Review / Range Tests - Part 2
Review and tests of 10 two-way radios, FCC and licensing. Full review data and links here: http://www.mjlorton.com/two-way-radio-handset-handy-talkies-hts-tests-walkie-talkies-the-results/ ------------------------------ Click "Show more" ------------------------------------------- Motorola
From playlist Two-Way Radio Review
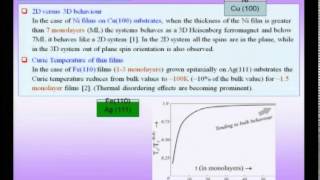
Mod-01 Lec-23 Electrical, Magnetic and Optical Properties of Nanomaterials
Nanostructures and Nanomaterials: Characterization and Properties by Characterization and Properties by Dr. Kantesh Balani & Dr. Anandh Subramaniam,Department of Nanotechnology,IIT Kanpur.For more details on NPTEL visit http://nptel.ac.in.
From playlist IIT Kanpur: Nanostructures and Nanomaterials | CosmoLearning.org

Common Drain Amplifier Explained
https://www.patreon.com/edmundsj If you want to see more of these videos, or would like to say thanks for this one, the best way you can do that is by becoming a patron - see the link above :). And a huge thank you to all my existing patrons - you make these videos possible. Common Drain
From playlist Electronics II: Analog Circuits

DEFCON 15: Re-Animating Drives & Advanced Data Recovery
Speaker: Scott Moulton Forensic Strategy Services, LLC. / System Specialist NEW!! Advanced Data Recovery Material. Even people who think they know everything about a hard drive will be surprised at what they will learn in this presentation. Everyone will learn something new about hard dr
From playlist DEFCON 15

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
