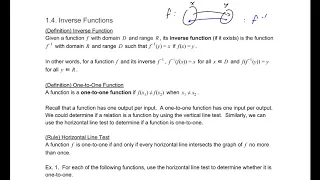
Definition, horizontal line test, and examples! Facebook: https://www.facebook.com/braingainzofficial Instagram: https://www.instagram.com/braingainzofficial Thanks for watching! Comment below with any questions / feedback and make sure to like / subscribe if you enjoyed!
From playlist Precalculus

Multivariable Taylor Polynomials
Free ebook http://tinyurl.com/EngMathYT A lecture on how to calculate Taylor polynomials and series for functions of two variables. Such ideas are useful in approximation of functions. We show where the polynomial representation comes from.
From playlist Mathematics for Finance & Actuarial Studies 2

Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Maclaurin Series for e^(2x)
From playlist Calculus 2 Exam 4 Playlist

All F chords are made from different permutations and combinations of the F,C and A notes
From playlist Music Lessons

Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language
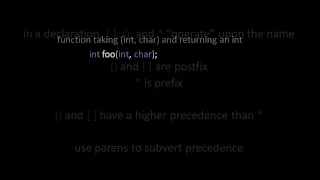
Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Stanford Seminar - Bugs in Crypto Implementations
Whether it’s by email, text, or social media platform, the average person will send over 60 messages per day—that's 22,000 messages per year. With billions of messages sent around the world each day, how can you be sure that your messages are safe and secure? Join professor Dan Boneh, on
From playlist Stanford Seminars

CERIAS Security: Watermarking Relational Databases 2/6
Clip 2/6 Speaker: Mohamed Shehab · Purdue University Proving ownership rights on outsourced relational databases is a crucial issue in today internet-based application environment and in many content distribution applications. In this talk, we will present mechanisms for proof of owne
From playlist The CERIAS Security Seminars 2005 (2)

Ruby Conf 2013 - Being Boring: A Survival Guide to Ruby Cryptography
We all know that security is hard, and that math is hard, but what happens when you put them together? Cryptography is an increasingly essential tool for building secure systems, but also a perilous minefield where any number of mistakes can lead to insecure systems. This talk will take y
From playlist Ruby Conf 2013 - Miami Beach, FL

R11. Cryptography: More Primitives
MIT 6.046J Design and Analysis of Algorithms, Spring 2015 View the complete course: http://ocw.mit.edu/6-046JS15 Instructor: Ling Ren In this recitation, problems related to cryptography are discussed. License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More c
From playlist MIT 6.046J Design and Analysis of Algorithms, Spring 2015

22C3: Anonymous Data Broadcasting by Misuse of Satellite ISPs
Speaker: Sven Löschner An open-source project to develop a tool for broadband satellite broadcasts The lecture focuses on satellite ISP technology and how to misuse it for anonymously broadcasting to an unlimited number of anonymous users while only one user pays for a standard dial-up c
From playlist 22C3: Private Investigations

Off-the-Record Messaging: Useful Security and Privacy for IM
May 23, 2007 lecture by Ian Goldberg for the Stanford University Computer Systems Colloquium (EE 380). In this talk, Ian discusses "Off-the-Record Messaging" (OTR), a widely used software tool for secure and private instant messaging; he outlines the properties of Useful Security and Priva
From playlist Course | Computer Systems Laboratory Colloquium (2006-2007)

DeepSec 2009: Reversing and Exploiting an Apple Firmware Update
Thanks to the DeepSec organisation for making these videos available and let me share the videos on YouTube. Speaker: K. Chen K. Chen explains how to use an Apple firmware update to get a foothold on the system. For more information visit: http://bit.ly/DeepSec_2009_information To down
From playlist DeepSec 2009

Working with Multiple Windows in Split View - Tips for Windows & Mac
Sign up for our Excel webinar, times added weekly: https://www.excelcampus.com/blueprint-registration/ In this video I explain tips for enabling split screen view in Windows and Mac. I share the mouse and keyboard shortcuts that make it quick and easy to work between two windows. Read t
From playlist Excel Tips & Shortcuts

Voicemod & Stream Deck Pairing on MacOS | Tutorial & Guide
Do you have Voicemod working on your Mac (see my other two videos on how to get this going below), but can't connect it with your Stream Deck? In this tutorial/guide, I explain how to set-up your working Voicemod in your Windows virtual machine with a Hotkey app called Quicksilver to get
From playlist Tech Tutorials
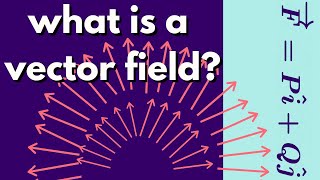
Multivariable Calculus | What is a vector field.
We introduce the notion of a vector field and give some graphical examples. We also define a conservative vector field with examples. http://www.michael-penn.net http://www.randolphcollege.edu/mathematics/
From playlist Multivariable Calculus