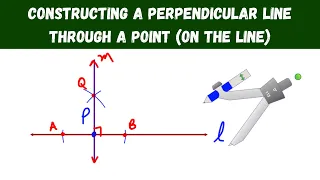
constructing a perpendicular line through a point (on the line) - geometry constructions
In this video, I show how to construct a perpendicular line through a point on the line. I use a compass and straightedge to construct the perpendicular line. The technique used in video is similar to the construction of a perpendicular bisector. Outside of this computer software, this is
From playlist Geometry

How to determine the distance from a point to a line. The ideas involve projection of vectors. Free ebook https://bookboon.com/en/introduction-to-vectors-ebook (updated link) Test your understanding via a short quiz http://goo.gl/forms/wHGVJKuSvu
From playlist Introduction to Vectors

Quick tips for setting up a line in desmos from a point and slope
From playlist desmos
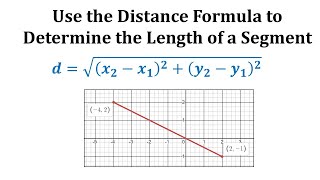
Example: Determine the Distance Between Two Points
This video shows an example of determining the length of a segment on the coordinate plane by using the distance formula. Complete Video List: http://www.mathispower4u.yolasite.com or http://www.mathispower4u.wordpress.com
From playlist Using the Distance Formula / Midpoint Formula

Frame formats | Networking tutorial (6 of 13)
Comparison of point-to-point and multipoint networks and frame formats of Ethernet and PPP Support me on Patreon: https://www.patreon.com/beneater This video is part 6 of an intro to networking tutorial: https://www.youtube.com/playlist?list=PLowKtXNTBypH19whXTVoG3oKSuOcw_XeW
From playlist Networking tutorial
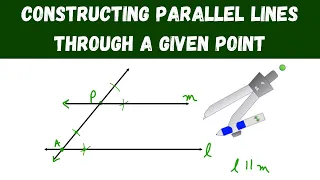
constructing parallel lines through a given point - geometry
In this video, I show how to use a compass to construct parallel lines through a given point. The techniques used in this video are similar to the copying an angle construction. Outside of this computer software, this is my favorite type of compass to use: https://amzn.to/38BGoPG If thi
From playlist Geometry

28C3: Cellular protocol stacks for Internet (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: Harald Welte Almost everyone uses the packet oriented transmission modes of cellular networks. However, unlike TCP/I
From playlist 28C3: Behind Enemy Lines

DEFCON 19: Cipherspaces/Darknets: An Overview Of Attack Strategies
Speaker: Adrian Crenshaw "Irongeek" Tenacity Institute and Irongeek.com Darknets/Cipherspaces such as Tor and I2P have been covered before in great detail. Sometimes it can be hard to follow attack strategies that have been used against them as the papers written on the topic have been a
From playlist DEFCON 19

Communications and Network Security | CISSP Training Videos
🔥 Enroll for FREE CISSP Course & Get your Completion Certificate: https://www.simplilearn.com/learn-cloud-security-basics-skillup?utm_campaign=CCSP&utm_medium=DescriptionFirstFold&utm_source=youtube Communication and Network Security : Domain 4 of the CISSP certification course offered by
From playlist Cyber Security Playlist [2023 Updated]🔥

DEFCON 16: Generic, Decentralized, Unstoppable Anonymity: The Phantom Protocol
Speaker: Magnus Bråding, Security Researcher, Fortego Security Recent years, and especially this past year, have seen a notable upswing in developments toward anti online privacy around the world, primarily in the form of draconian surveillance and censorship laws (both passed and attempt
From playlist DEFCON 16

Speaker: Jens Kubieziel An introduction into anonymous communication with I2P I2P is a message-based anonymizing network. It builds a virtual network between the communication endpoints. This talk will introduce the technical details of I2P and show some exemplary applications. My talk
From playlist 24C3: Full steam ahead

Speaker: Brad Hedlund, VMware This session is a 201 level technical deep dive on the VMware/Nicira Network Virtualization Platform (NVP). NVP is a virtual networking platform powering many OpenStack production environments as the networking engine behind Quantum. In this session we'll e
From playlist OpenStack Summit Portland 2013

What Is IPSec Protocols? | IPSec Protocol Explained | Computer Networks Tutorial | Simplilearn
In this video on 'What Is IPSec Protocol?', we will examine the introductory knowledge regarding the processes, features, and working of the IPsec protocol. Along with the various steps involved in establishing a secure network channel for data transmission. Topics covered in this video o
From playlist Networking

Black Hat USA 2010: PSUDP: A Passive Approach to Network-Wide Covert Communication 3/4
Speaker: Kenton Born This presentation analyzes a novel approach to covert communication over DNS by introducing PSUDP, a program demonstrating passive network-wide covert communication. While several high-bandwidth DNS tunnel implementations are freely available, they all use similar str
From playlist BH USA 2010 - NETWORK

SOURCE Boston 2009: Introducing Heyoka: DNS Tunneling 2.0
Speakers: Alberto Revelli, Portcullis Nico Leidecker, Portcullis DNS Tunneling is a well known technique, and various free tools are available to play with it. However, its full power has not been fully unleashed yet: several of the existing tools are mostly targeted to read email for f
From playlist Latest uploads

Defcon14 V36 Geers and Eisen IPv6 World Update
From playlist DEFCON 14