Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security

Fundamental concepts of IPSec are discussed. Authentication Header is explained. Encapsulating Security Payload (ESP) and Internet Key Exchange (IKE) are analyzed.
From playlist Network Security

RSA Conference USA 2010: There's No ""Point"" to Security Anymore 2/3
Clip 2/3 Speaker: David DeWalt, President & CEO, McAfee, Inc. The era of providing complete protection by installing multiple best-of-breed security products has passed. Today's world of sophisticated malware, targeted threats, and multi-stage attacks requires security that is smart,
From playlist RSA Conference USA 2010

Transport Layer Security: Part 1
Fundamental concepts of TLS are discussed. SSL is analyzed. HTTPS & SSH are presented.
From playlist Network Security

Why isn’t the Netherlands underwater? - Stefan Al
Dig into the incredible engineering of the Netherlands’ Delta Works— the most sophisticated flood prevention system in the world. -- In January 1953, a tidal surge shook the North Sea. The titanic waves flooded the Dutch coastline, killing almost 2,000 people. 54 years later, a similar
From playlist Epic engineering: How did this get made

신입SW인력을 위한 실전 JSP Servlet 동영상과정 - 제 07강 Servlet 본격적으로 살펴보기-III
신입SW인력을 위한 실전 JSP Servlet 동영상과정 - 제 07강 Servlet 본격적으로 살펴보기-III 이번 강의는 Servlet 본격적으로 살펴보기-III입니다. "저희는 도구를 드립니다. 여러분은 창의력으로 만들어주세요." PC로 보실때는 서울산업진흥원(www.sba.kr)에서 제작한 유튜브 동영상에서 HD 동영상을 보시는 것이 좋습니다. 1080p로 설정해서 보시면 글자가 잘 보입니다. 오른쪽 하단 톱니모양에서 1080p를 선택하세요. 그리고 모바일로 보실 때에는 유튜브 앱으로
From playlist 자바-JSP-Spring 강좌

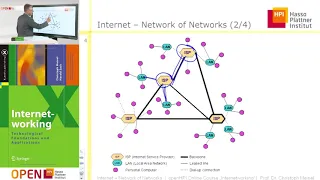
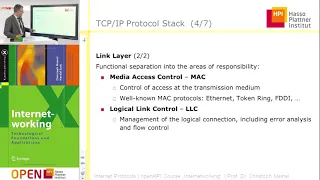
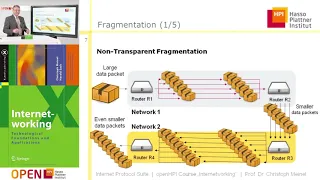
An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

EEVblog #43 - Fluke 233 Multimeter Review
Buy the Fluke 233 here: http://www.amazon.com/gp/product/B002ZNPRKI?ie=UTF8&tag=ee04-20&linkCode=as2&camp=1789&creative=9325&creativeASIN=B002ZNPRKI Dave gets his hands on the first Fluke 233 meter in the country. Gimmick?, or the biggest innovation in multimeters since autoranging?
From playlist Multimeter Reviews

Lecture 21: HP Model & Interlocked Chains
MIT 6.849 Geometric Folding Algorithms: Linkages, Origami, Polyhedra, Fall 2012 View the complete course: http://ocw.mit.edu/6-849F12 Instructor: Erik Demaine This lecture presents the hydrophobicity (HP) model for protein folding and optimization using parity cases. Interlocked 3D chains
From playlist MIT 6.849 Geometric Folding Algorithms, Fall 2012

Len Lye Centre: Building a Museum with BIM | The B1M
Len Lye was a famous kinetic artist. The Len Lye Centre is dedicated to his work and is New Zealand’s first single-artist museum. Here we look at how building information modelling (BIM) helped to deliver this impressive facility. For more by The B1M subscribe now - http://ow.ly/GxW7y Re
From playlist Construction Around The World | The B1M

CS3 Lecture 2: Design in Computing - Richard Buckland UNSW COMP2911
This is the second lecture of Computing 3 (COMP2911) from 2010. I've uploaded this quickly and will eventually follow behind with a cleaned edited higher quality version. Please don't distribute this version. As it it is a low resolution unedited version without proper attributions and
From playlist CS3: Design in Computing - Richard Buckland UNSW

States with non-uniform temperature profiles in conformal field theory by Krzysztof Gawedzki
Large deviation theory in statistical physics: Recent advances and future challenges DATE: 14 August 2017 to 13 October 2017 VENUE: Madhava Lecture Hall, ICTS, Bengaluru Large deviation theory made its way into statistical physics as a mathematical framework for studying equilibrium syst
From playlist Large deviation theory in statistical physics: Recent advances and future challenges

Making an Illuminated Action Figure Display Stand!
Our next laser cutter project is an exercise of designing with slot joints to piece together a clear acrylic display stand that houses LED lights for underlighting. Norm walks through his design process and prototyping for this action figure platform, the lessons learned in vector design,
From playlist Toys, Models and Collectibles