Cryptography lists and comparisons
List of ciphertexts
Some famous ciphertexts (or cryptograms), in chronological order by date, are: (Wikipedia).

Cryptography lists and comparisons
Some famous ciphertexts (or cryptograms), in chronological order by date, are: (Wikipedia).


One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Symmetric Key Cryptography: The Caesar Cipher
This is the first in a series about cryptography; an extremely important aspect of computer science and cyber security. It introduces symmetric key cryptography with a well known substitution cipher, namely the Caesar Cipher. It includes a few examples you can try for yourself using diff
From playlist Cryptography

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security
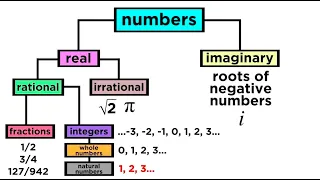
What are the Types of Numbers? Real vs. Imaginary, Rational vs. Irrational
We've mentioned in passing some different ways to classify numbers, like rational, irrational, real, imaginary, integers, fractions, and more. If this is confusing, then take a look at this handy-dandy guide to the taxonomy of numbers! It turns out we can use a hierarchical scheme just lik
From playlist Algebra 1 & 2

Learn how to read key-value pairs from a text file into a HashMap.
From playlist Intermediate Java

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

An intro to the core protocols of the Internet, including IPv4, TCP, UDP, and HTTP. Part of a larger series teaching programming. See codeschool.org
From playlist The Internet

Stanford Seminar - Bugs in Crypto Implementations
Whether it’s by email, text, or social media platform, the average person will send over 60 messages per day—that's 22,000 messages per year. With billions of messages sent around the world each day, how can you be sure that your messages are safe and secure? Join professor Dan Boneh, on
From playlist Stanford Seminars

Jonathan Katz - Introduction to Cryptography Part 1 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography I" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will serve as a "crash course" in modern cryptography for those with no prior exposure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Presented by WWCode Blockchain Speaker: Swetha Srinivasan, Google This talk will give an overview of introductory concepts in security such as confidentiality, integrity, availability, authentication and authorization. It will cover how cryptography is used in real world systems and funda
From playlist Center for Applied Cybersecurity Research (CACR)

Tackling Enigma (Turing's Enigma Problem Part 2) - Computerphile
Just how did the team at Bletchley Park tackle the problem of decoding Enigma? In Part Two of our series on "The Real" Imitation Game, Professor Brailsford explains how they did it. Part One of this series: Turing's Enigma Problem: http://youtu.be/d2NWPG2gB_A Professor Brailsford's no
From playlist Subtitled Films

RSA Encryption Algorithm | Rivest–Shamir–Adleman | RSA Algorithm Explained | Simplilearn
In this video on the RSA Encryption Algorithm, we learn about the global standard in asymmetric encryption, designed by Rivest-Shamir-Adleman. We understand the basics of asymmetric encryption, handling of digital signatures, and how we can use RSA encryption algorithm in the verification
From playlist Cyber Security Playlist [2023 Updated]🔥

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Discrete Structures: Digital certificates and implementing RSA
Our last session on RSA and public key cryptography. We'll learn about digital certificates and see how to implement the core RSA algorithms in Python.
From playlist Discrete Structures, Spring 2022

Discrete Structures: Modular Arithmetic & Simple Ciphers
In this session we'll introduce modular arithmetic and apply the principles to simple crytographic ciphers such as the shift cipher (also called the Caesar cipher) and the linear cipher.
From playlist Discrete Structures, Spring 2022
What is Cryptography? | Introduction to Cryptography | Cryptography for Beginners | Edureka
🔵Edureka Cyber Security Masters Program: https://bit.ly/3pfHHIN 🔥Edureka CompTIA Security+ Certification Training: https://bit.ly/3nxeVRl Cryptography is essential to protect the information shared across the internet. This video on What is cryptography explaines you the fundamental concep
From playlist Cyber Security Training for Beginners | Edureka

ASCII and Unicode Character Sets
This video describes the fundamental principles of character sets, character encoding, ASCII and Unicode. In particular, it covers the limitations of ASCII and the plethora of extended ASCII code pages. It also covers the design goals of Unicode, and describes the way control bits are al
From playlist GCSE Computer Science