
Signature Validation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Can You Validate These Emails?
Email Validation is a procedure that verifies if an email address is deliverable and valid. Can you validate these emails?
From playlist Fun

Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography
How to sign a document in Microsoft Word
Doing this tutorial for a friend! He needed to know how to write his signature in a word document. Here is how you do it!
From playlist Microsoft Word Tutorials

Signature Validation - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Certificate Details - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Signing Certificates - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Signatures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

How to Create Signable PDF Documents (Tutorial)
Start sending free signable documents with Jotform: https://bit.ly/jotformsign Creating and sending signable documents is a must for any business. But isn't it complicated to make and manage these documents? Not with Jotform Sign! In this video, Scott Friesen shows you how easy it is to c
From playlist Productivity App Reviews for Entrepreneurs & Small Business

70-640 Certificate Services / 2008 R2 - Installing a Single Tier PKI (Detailed)
In this video we will demostrate all the details of how to install a single Tier Windows Server 2008 R2 Enterprise Root CA. This video is loaded with hints and tips to watch for durning the install. The perfect video for someone with a small company that want to setup a super simple PKI in
From playlist Cryptography, Security

Certificate Services: Stand-alone Certificate Authority
Certificate Services: Stand-alone Certificate Authority, CA
From playlist Cryptography, Security

PSHSummit 2022 - PKI for Mere Mortals by James Ruskin and Stephen Valdinger
PowerShell Summit videos are recorded on a "best effort" basis. We use a room mic to capture as much room audio as possible, with an emphasis on capturing the speaker. Our recordings are made in a way that minimizes overhead for our speakers and interruptions to our live audience. These re
From playlist PowerShell + DevOps Global Summit 2022

Speaker: PETER HANNAY SECURITY RESEARCHER, PHD STUDENT Smart phones and other portable devices are increasingly used with Microsoft Exchange to allow people to check their corporate emails or sync their calendars remotely. Exchange has an interesting relationship with its mobile clients.
From playlist DEFCON 20

DEFCON 18: DNS Systemic Vulnerabilities and Risk Management: A Discussion (Video Only) 2/4
Speakers: Rod Beckstrom, Dan Kaminsky, Paul Mockapetris, Ken Silva, Mark Weatherford The experts on this panel will provide their views on systemic risks facing the DNS and provide thoughts on measures that should be undertaken to remediate the risks. The panelists will discuss both the
From playlist DEFCON 18-1

DEFCON 18: An Observatory for the SSLiverse 3/4
Speakers: Peter Eckersley, Jesse Burns This talk reports a comprehensive study of the set of certificates currently in use on public HTTPS servers. We investigate who signed the certs, what properties they have, and whether there is any evidence of malicious certificates signed, directl
From playlist DEFCON 18-1

Black Hat USA 2010: State of SSL on the Internet: 2010 Survey Results and Conclusions 2/4
Speaker: Ivan Ristic SSL (TLS) is the technology that protects the Internet, but very little is actually known about its usage in real-life. How are the many Internet SSL servers configured? Which CA certificates do they use? Which protocols and cipher suites are supported? Answers to eve
From playlist BH USA 2010 - BIG PICTURE

DEFCON 18: Black Ops Of Fundamental Defense: Web Edition 4/4
Speaker: Dan Kaminsky Lets be honest: Year in, year out, we keep finding the same bugs in the same places, and wondering: Why don't they learn? Why don't developers use these beautiful tools we provide them -- parameterized queries, XSRF tokens, X.509 certificates, and escapes in all th
From playlist DEFCON 18-1

ShmooCon 2013: Apple iOS Certificate Tomfoolery
For more information and to download the video visit: http://bit.ly/shmoocon2013 Playlist ShmooCon 2013: http://bit.ly/Shmoo13 Speaker: Tim Medin Mobile devices rely on many complex systems for security, reintroducing mistakes in implementation and design that are reminiscent of the 1990
From playlist ShmooCon 2013
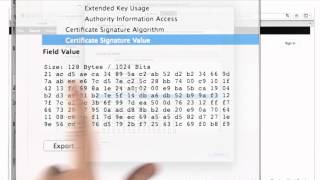
Certificates And Signatures - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography