
This 59 second video gives you a glimpse of what Flipping Physics is all about. Algebra Based Physics Videos: http://www.flippingphysics.com/algebra.html Calculus Based Physics Videos (AP Physics C): http://www.flippingphysics.com/calculus.html
From playlist Miscellaneous

Flipped Learning Meta-Analysis
I share quotes from an article about a meta-analysis of flipped learning. The article → https://brook.gs/3lY8j0F More about flipped learning → http://flippingphysics.com/flipping.html Content Times: 0:00 Flipped Learning 1:11 The Article 1:99 Quote #1 2:44 Quote #2 3:16 Quote #3 #Flipped
From playlist Miscellaneous

What is the difference between rotating clockwise and counter clockwise
👉 Learn how to rotate a figure and different points about a fixed point. Most often that point or rotation will be the original but it is important to understand that it does not always have to be at the origin. When rotating it is also important to understand the direction that you will
From playlist Transformations

Why I love 4294967296? MegaFavNumbers.
Bitonic sorter: https://en.wikipedia.org/wiki/Bitonic_sorter Fast Fourier Transform https://en.wikipedia.org/wiki/Fast_Fourier_transform#:~:text=A%20fast%20Fourier%20transform%20(FFT,frequency%20domain%20and%20vice%20versa. #MegaFavNumbers I know that this video is horrible, but an invite
From playlist MegaFavNumbers

Spinlaunch Throw Rockets into Space (with something which looks like Nikola Tesla turbine)!!!
The concept behind that system is simple. Essentially, SpinLaunch wants to get to orbit by using a large, vacuum-sealed chamber and a hypersonic tether to spin a spacecraft at a high enough velocity up to 5000 miles per hour to escape the atmosphere. That means no rocket, no rocket engines
From playlist SPACE

From playlist Magnetism

Awesome Turn on lighter (slow motion)!!!
Amazing Turn on lighter in slow motion!!!
From playlist THERMODYNAMICS

Math of the twisting somersault
Mathematical models can be used to obtain an understanding of the mechanics of twists during somersaults. The twisting somersault can be described by a formula, which factors in the airborne time of the diver, the time spent in various stages of the dive, the number of somersaults, the num
From playlist What is math used for?

From playlist Magnetism

24C3: Mifare (Little Security, Despite Obscurity)
Speakers: Karsten Nohl, Henryk Plötz Mifare are the most widely deployed brand of secure RFID chips, but their security relies on proprietary and secret cryptographic primitives. We analyzed the hardware of the Mifare tags and found weaknesses in several parts of the cipher. For more i
From playlist 24C3: Full steam ahead

CERIAS Security: Recent Attacks on MD5 4/6
Clip 4/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

Instance-Hiding Schemes for Private Distributed Learning -Sanjeev Arora
Seminar on Theoretical Machine Learning Topic: Instance-Hiding Schemes for Private Distributed Learning Speaker: Sanjeev Arora Affiliation: Princeton University; Distinguishing Visiting Professor, School of Mathematics Date: June 25, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

OWASP AppSec 2010: BitFlip: Determine a Data's Signature Coverage from Within the Application 1/2
Clip 1/2 Speaker: Henrich Christopher Poehls, University of Passau - ISL Despite applied cryptographic primitives applications are working on data that was not protected by them. We show by abstracting the message flow between the application and the underlying wire, that protection is
From playlist OWASP AppSec 2010

CS224W: Machine Learning with Graphs | 2021 | Lecture 16.4 - Robustness of Graph Neural Networks
For more information about Stanford’s Artificial Intelligence professional and graduate programs, visit: https://stanford.io/3Csn5T7 Jure Leskovec Computer Science, PhD For the last segment of our discussion on advanced GNN topics, we discuss the robustness of GNNs. We first introduce th
From playlist Stanford CS224W: Machine Learning with Graphs

Modes of Operation of Block Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Universal Adversarial Perturbations and Language M… | Pamela Mishkin | OpenAI Scholars Demo Day 2020
Learn more: https://openai.com/blog/openai-scholars-2020-final-projects#pamela
From playlist Events and Talks

30C3: Security of the IC Backside (EN)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: nedos In the chain of trust of most secure schemes is an electronic chip that holds secret information. These schemes often employ cryptographically secure protocol
From playlist 30C3

30C3: Security of the IC Backside (DE - translated)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: nedos In the chain of trust of most secure schemes is an electronic chip that holds secret information. These schemes often employ cryptographically secure protocol
From playlist 30C3
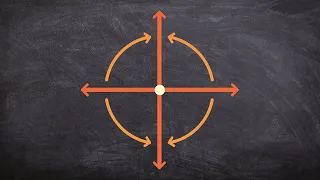
Determining clockwise vs counter clockwise rotations
👉 Learn how to rotate a figure and different points about a fixed point. Most often that point or rotation will be the original but it is important to understand that it does not always have to be at the origin. When rotating it is also important to understand the direction that you will
From playlist Transformations

Fault-tolerant federated and distributed learning
A Google TechTalk, 2020/7/30, presented by Sanmi Koyejo, University of Illinois at Urbana-Champaign ABSTRACT: Distributed machine learning models are routinely trained using devices that are susceptible to hardware, software, and communication errors, along with other robustness concerns.
From playlist 2020 Google Workshop on Federated Learning and Analytics