
Math for Liberal Studies: Decoding a Message Using the Bifid Cipher
In this video, we work through an example decoding a message using the bifid cipher. For more info, visit the Math for Liberal Studies homepage: http://webspace.ship.edu/jehamb/mls/index.html
From playlist Math for Liberal Studies

Math for Liberal Studies: Encoding a Message Using the Bifid Cipher
In this video, we work through an example encoding a message using the bifid cipher. For more info, visit the Math for Liberal Studies homepage: http://webspace.ship.edu/jehamb/mls/index.html
From playlist Math for Liberal Studies

Math for Liberal Studies - Lecture 3.6.2 The Bifid Cipher
This is the second video lecture for Math for Liberal Studies Section 3.6: An Introduction to Cryptography. In this lecture, we discuss a new method for encrypting and decrypting messages: the bifid cipher. This method relies on converting the letters in the message to coordinates in a let
From playlist Math for Liberal Studies Lectures
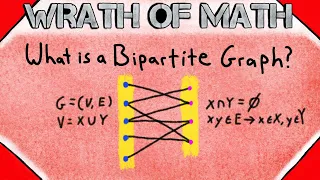
What is a Bipartite Graph? | Graph Theory
What is a bipartite graph? We go over it in today’s lesson! I find all of these different types of graphs very interesting, so I hope you will enjoy this lesson. A bipartite graph is any graph whose vertex set can be partitioned into two disjoint sets (called partite sets), such that all e
From playlist Graph Theory

Math for Liberal Studies - Lecture 3.7.2 The Vigenère and Autokey Ciphers
This is the second video for Math for Liberal Studies Section 3.7: Modular Arithmetic and Ciphers. In this video, we apply the modular arithmetic ideas from the previous lecture to cryptography. Specifically, we learn how to replace the letters in a message with numbers and perform "letter
From playlist Math for Liberal Studies Lectures
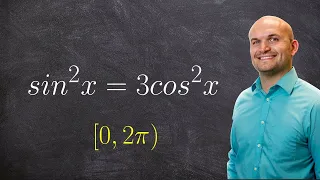
Solving a trig function with sine and cosine
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric equations, they include factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the given eq
From playlist Solve Trigonometric Equations by Factoring

Dimples! They're so cute, but surprisingly mysterious! What causes them naturally and how can we make them happen? Hosted by: Hank Green ---------- Support SciShow by becoming a patron on Patreon: https://www.patreon.com/scishow ---------- Dooblydoo thanks go to the following Patreon supp
From playlist Uploads
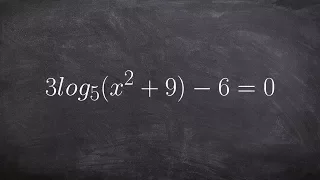
Isolating a logarithm and using the power rule to solve
👉 Learn how to solve logarithmic equations. Logarithmic equations are equations with logarithms in them. To solve a logarithmic equation, we first isolate the logarithm part of the equation. After we have isolated the logarithm part of the equation, we then get rid of the logarithm. This i
From playlist Solve Logarithmic Equations

Composing Trig & Inverse Trig Functions (2)
Evaluating compositions of #trig & inverse #trig functions: More quick formative assessment via #geogebra: https://www.geogebra.org/m/rwpkkmt7 & https://www.geogebra.org/m/hcw4fr6t #MTBoS #ITeachMath #trigonometry #precalc #math #mathchat
From playlist Trigonometry: Dynamic Interactives!

Row and column polynumbers | Arithmetic and Geometry Math Foundations 65 | N J Wildberger
This video introduces a two-dimensional aspect to arithmetic by considering both polynumbers written as columns and as rows, and then putting those two ideas together to define bipolynumbers, whose coefficients form a rectangle. The associated polynomials are written in two variables, alph
From playlist Math Foundations

What are Complete Bipartite Graphs? | Graph Theory, Bipartite Graphs
What are complete bipartite graphs? We'll define complete bipartite graphs and show some examples and non-examples in today's video graph theory lesson! Remember a graph G = (V, E) is bipartite if the vertex set V can be partitioned into two sets V1 and V2 (called partite sets) such that
From playlist Graph Theory

Solving an equation with sine on both sides
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric identities, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the give
From playlist Solve Trigonometric Equations

Follow-up: Barbie electronic typewriter
Here is a copy of the description from the Barbie video: ---- I first found this story on the crypto museum website, which has great information about the Barbie typewriter (and other cipher machines) https://www.cryptomuseum.com/crypto/mehano/barbie/ ------- Thanks to Sarah Everett fr
From playlist My Maths Videos

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Solving for sine with no constraints
👉 Learn how to solve trigonometric equations. There are various methods that can be used to evaluate trigonometric identities, they include by factoring out the GCF and simplifying the factored equation. Another method is to use a trigonometric identity to reduce and then simplify the give
From playlist Solve Trigonometric Equations