
Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

Block Cipher Operation (BCO): Part 1
Fundamental concepts of Block Cipher Operation are discussed. Various extensions of DES are presented. Encryption modes for long messages are explained. Double DES, Triple DES, DES-X Encryption Modes for long messages: Electronic Code Book (ECB) Cipher Block Chaining (CBC) Cipher Feedback
From playlist Cryptography, Security

Toy Substitution Cipher 2 Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

From playlist Week 2 2015 Shorts

Block Cipher Operation (BCO): Part 2
Fundamental concepts of Block Cipher Operation are discussed. Various extensions of DES are presented. Encryption modes for long messages are explained. Double DES, Triple DES, DES-X Encryption Modes for long messages: Electronic Code Book (ECB) Cipher Block Chaining (CBC) Cipher Feedback
From playlist Network Security

I know Kung Fu! (or neo4j on Rails without jRuby)
"Reality is a graph, embrace it!" Sure graph databases are really cool and have a timestamp dated next week, but do you know when you should actually use one? Sometimes living on the bleeding edge pays off and in this talk, I'll show you how you can simplify your application and model your
From playlist Cascadia Ruby 2012

ADFGVX Cipher: Encryption and Decryption (OLD VERSION: SEE NEW VERSION LINK BELOW)
This video has been replaced with an updated video: visit https://youtu.be/T0xfKiU9Rr4 Encryption and Decryption of the World War One ADFGVX Cipher, through examples.
From playlist Classical Cryptography

OWASP AppSecUSA 2012: Reverse Engineering Secure HTTP API's With an SSL Proxy
Speakers: Alejandro Caceres and Mark Haase The proliferation of mobile devices has led to increased emphasis on native applications, such as Objective-C applications written for iOS or Java applications written for Android. Nonetheless, these native client applications frequently use HTTP
From playlist OWASP AppSecUSA 2012

ADFGVX Cipher: Encryption and Decryption (Updated)
Encryption and Decryption of the World War One ADFGVX Cipher, through examples. This video replaces an earlier one with the same content, but has some improvements and corrections. #cryptography
From playlist Classical Cryptography

Lions, Skunks, and Kangaroos: Geo-Distributed Learning on the Flickr-Mammal Dataset
A Google TechTalk, 2020/7/29, presented by Phillip Gibbons, Carnegie Mellon University ABSTRACT:
From playlist 2020 Google Workshop on Federated Learning and Analytics

From playlist CS50 Walkthroughs (Problem Sets)

Speaker: Philip R. Zimmermann The time for secure encrypted VoIP for the masses is upon us. The Zfone Project has come a long way in the two years since Phil Zimmermann demoed a prototype at Black Hat. It's now a family of products, running on Symbian and Windows mobile phones, soft VoIP
From playlist DEFCON 15

From playlist Week 2 2015 Shorts

Zig Zag Decryption - Computerphile
XOR encryption is flawed. Professor Brailsford explains the zig-zag method that can reveal the precious key stream. Fishy Codes – Bletchley's Other Secret: https://youtu.be/Ou_9ntYRzzw XOR and the Half Adder: https://youtu.be/VPw9vPN-3ac Colossus & Bletchley Park: https://youtu.be/9HH-as
From playlist Subtitled Films

Hunting for the Zodiac Killer | History's Greatest Mysteries (Season 4)
The Zodiac Killer is one of the most elusive serial killers of all time. See more in this clip from Season 4, Episode 2, "Who is the Zodiac Killer?" Watch all new episodes of History's Greatest Mysteries, returning Monday, January 30 at 9/8c, and stay up to date on all of your favorite Th
From playlist History's Greatest Mysteries | Official Series Playlist | History

Ruby Conf 2011 Better Than ROT13 by Bradley Grzesiak
We use encryption every day, from SSL to SSH to passing notes to your crush during Social Studies class. But how does it actually work? I'll avoid most of the math but cover the concepts of both symmetric and asymmetric encryption, including hashing and signing. I'll also show how to use O
From playlist Ruby Conference 2011

The Archaeology Iceberg Explained
I have returned from my four month long hiatus! I hope this 50 minute video makes up for it. Today, we will explore some of the most bizarre and obscure stories and facts related to the field of archaeology. In this video, I talk about everything from mummies to Giant Aztec Snake statues t
From playlist Anthropology Profile

Courses on Khan Academy are always 100% free. Start practicing—and saving your progress—now: https://www.khanacademy.org/humanities/grammar/usage-and-style/style/v/irony-final Irony, puns, and sarcasm are some of the toughest concepts in English. This video attempts to explain all three.
From playlist Grammar

Face-to-Face with a Bear - Meet the Expert | National Geographic
Have you ever been face-to-face with a bear? Our host Lizzie Daly is joined by Dr. Rae Wynn-Grant, a large carnivore ecologist whose work involves tracking and studying wild bears. ➡ Subscribe: http://bit.ly/NatGeoSubscribe About National Geographic: National Geographic is the world's pre
From playlist Newest Clips | National Geographic
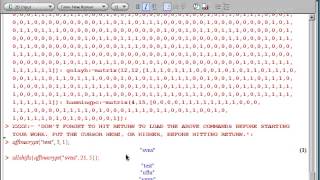
How to encrypt and decrypt the affine cipher using Maple software. Code from Into to Crypto and Coding Theory 2nd ed. by W. Trappe and LC Washington.
From playlist Cryptography and Coding Theory