
Null space of a matrix example
In today's lecture I work through an example to show you a well-known pitfall when it comes to the null space of a matrix. In the example I show you how to create the special cases and how to use them to represent the null space. There is also a quick look at the NullSpace function in Ma
From playlist Introducing linear algebra

Linear ODE with Constant Coefficients: The Homogenized Equation
https://bit.ly/PavelPatreon https://lem.ma/LA - Linear Algebra on Lemma http://bit.ly/ITCYTNew - Dr. Grinfeld's Tensor Calculus textbook https://lem.ma/prep - Complete SAT Math Prep
From playlist Partial Differential Equations

From playlist Unlisted LA Videos

Null space of a matrix using sympy
In this video I give a brief overview of the null space of a matrix and how to calculate (y hand) the column vectors that will make up the null space of the column. This becomes much easier in sympy, by simply using the nullspace function. If you want to learn more about the null space o
From playlist Modern linear algebra using Python instead of a textbook
Null points and null lines | Universal Hyperbolic Geometry 12 | NJ Wildberger
Null points and null lines are central in universal hyperbolic geometry. By definition a null point is just a point which lies on its dual line, and dually a null line is just a line which passes through its dual point. We extend the rational parametrization of the unit circle to the proj
From playlist Universal Hyperbolic Geometry

Zig Zag Decryption - Computerphile
XOR encryption is flawed. Professor Brailsford explains the zig-zag method that can reveal the precious key stream. Fishy Codes – Bletchley's Other Secret: https://youtu.be/Ou_9ntYRzzw XOR and the Half Adder: https://youtu.be/VPw9vPN-3ac Colossus & Bletchley Park: https://youtu.be/9HH-as
From playlist Subtitled Films

Week 2: Friday - CS50 2007 - Harvard University
Functions, continued. Global variables. Parameters. Return values. Stack. Frames. Scope. Arrays. Strings. Command-line arguments. Cryptography.
From playlist CS50 Lectures 2007

Null Space: Is a Vector in a Null Space? Find a Basis for a Null Space
This video explains how to determine if a vector is in a null space and how to find a basis for a null space.
From playlist Column and Null Space

DEFCON 19: Speaking with Cryptographic Oracles
Speaker: Daniel Crowley Application Security Consultant, Trustwave - SpiderLabs Cryptography is often used to secure data, but few people have a solid understanding of cryptography. It is often said that if you are not strictly a cryptographer, you will get cryptography wrong. For that ma
From playlist DEFCON 19
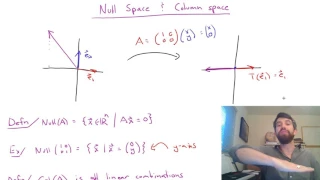
Null Space and Column Space of a Matrix
Given a matrix A(ie a linear transformation) there are several important related subspaces. In this video we investigate the Nullspace of A and the column space of A. The null space is the vectors that are "killed" by the transformation - ie sent to zero. The column space will be the image
From playlist Older Linear Algebra Videos

🔥Kotlin Tutorial for Beginners | Kotlin Android Tutorial | Kotlin for Android | Simplilearn
🔥Post Graduate Program In Full Stack Web Development: https://www.simplilearn.com/pgp-full-stack-web-development-certification-training-course?utm_campaign=BasicsOfKotlinLangauge:KotlinTutorialForBeginners-OTOurOIXH9Q&utm_medium=DescriptionFF&utm_source=youtube 🔥Caltech Coding Bootcamp (US
From playlist Kotlin

DEFCON 19: Steganography and Cryptography 101
Speaker: eskimo There are a lot of great ways to hide your data from prying eyes this talk will give a crash course in the technology and some tools that can be used to secure your data. Will also discuss hiding your files in plain site so an intruder will have no idea that hidden files
From playlist DEFCON 19

Shmoocon 2010: GSM: SRSLY? 5/6
Clip 5/6 Speakers: Chris Paget and Karsten Nohl The worlds most popular radio system has over 3 billion handsets in 212 countries and not even strong encryption. Perhaps due to cold-war era laws, GSM's security hasn't received the scrutiny it deserves given its popularity. This bothere
From playlist ShmooCon 2010

Prove a Null Space is a Subspace
This video provides a basic proof that a null space is a subspace.
From playlist Column and Null Space

Week 2: Wednesday - CS50 2008 - Harvard University
Functions, continued. Global variables. Parameters. Return values. Stack. Frames. Scope. Arrays. Strings. Command-line arguments. Cryptography.
From playlist CS50 Lectures 2008

Week 3: Monday - CS50 2010 - Harvard University
Linear search. Binary search. Asymptotic notation. Recursion. Bubble sort. Selection sort. Insertion sort. Debugging.
From playlist CS50 Lectures 2010

In this video I start to discuss the idea of the null space of a matrix. In these situations, the right-hand side of all the equations in the linear system is equal to zero. There is the trivial solution, where all the elements of the solution is zero. We are more interested in the spec
From playlist Introducing linear algebra
Cabling of knots in overtwisted contact manifolds - Rima Chatterjee
Joint IAS/Princeton/Montreal/Paris/Tel-Aviv Symplectic Geometry Title: Cabling of knots in overtwisted contact manifolds Speaker: Rima Chatterjee Affiliation: Cologne Date: October 8, 2021 Abstract: Knots associated to overtwisted manifolds are less explored. There are two types of kno
From playlist Mathematics

Finding a basis for Nul(A), the nullspace/kernel of A, by row-reducing Check out my Matrix Algebra playlist: https://www.youtube.com/playlist?list=PLJb1qAQIrmmAIZGo2l8SWvsHeeCLzamx0 Subscribe to my channel: https://www.youtube.com/channel/UCoOjTxz-u5zU0W38zMkQIFw
From playlist Matrix Algebra
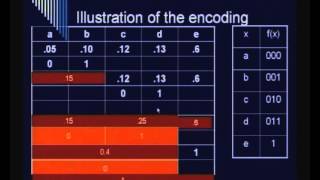
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security