
Network Security, Part 1 : Basic Encryption Techniques
Fundamental concepts of network security are discussed. It provides a good overview of secret Key and public key Encryption. Important data encryption standards are presented.
From playlist Network Security

RSA Conference USA 2010: Shifts in the Security Paradigm What Cloud and Collaboration Demand 3/4
Clip 3/4 Speaker: Dave Hansen, Corporate Senior Vice President & General Manager, CA Security Business Unit PANELISTS: Steve Riley,Timothy Christin, Dr. Larry Ponemon, Curt Aubley Cloud computing and Collaboration technologies are changing the way we communicate and do business. As t
From playlist RSA Conference USA 2010

Fundamental concepts of IPSec are discussed. Authentication Header is explained. ESP & IKE are analyzed.
From playlist Network Security
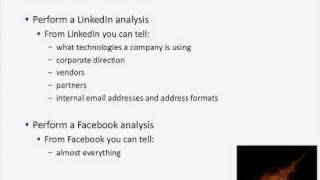
O'Reilly Webcast: Information Security and Social Networks
Social networks are an information security game changer, and enterprises and their management are struggling to understand and deal with the security risks of social networks. Traditional information security protected your corporate IT perimeter. But that won't help in the web 2.0 era
From playlist O'Reilly Webcasts

CERIAS Security: Tor: Anonymous communications for government agencies, corporations and you 1/7
Clip 1/7 Speakers: Paul Syverson & Roger Dingledine What do the Department of Defense and the Electronic Frontier Foundation have in common? They have both funded the development of Tor (torproject.org), a free-software anonymizing network that helps people around the world use the In
From playlist The CERIAS Security Seminars 2008

Amazon Virtual Private Cloud (VPC) | AWS Tutorial For Beginners | AWS Training Video | Simplilearn
🔥 Cloud Architect Master's Program (Discount Code: YTBE15): https://www.simplilearn.com/cloud-solutions-architect-masters-program-training?utm_campaign=AWS-fpxDGU2KdkA&utm_medium=DescriptionFirstFold&utm_source=youtube 🔥 Caltech Cloud Computing Bootcamp (US Only): https://www.simplilearn.c
From playlist AWS Tutorial Videos For Beginners 🔥[2022 Updated] | Simplilearn

AWS Certification | Which AWS Certification To Choose? | AWS Certification Path | Simplilearn
This video tutorial AWS Certification will help every individual learn why completing an AWS certification is essential in their career. If you're looking for an AWS job or planning to move to an AWS position in your current company, earning an AWS certification can be a brilliant investme
From playlist Cloud Computing Tutorial For Beginners 🔥[2023 Updated]

Top 10 Cloud Certifications For 2021 | Best Cloud Certifications | Cloud Computing | Edureka
🔥Cloud Masters Program: https://www.edureka.co/masters-program/cloud-architect-training 📢Top 10 Certifications for 2021: https://youtu.be/SY4TWhXyr0I 📢 Cloud Computing is one of the most trending technologies in today's market and this video on 'Top 10 Cloud Certifications for 2021' lists
From playlist Top Trending Technologies to Learn in 2021 | Edureka

Azure Certification Path | Azure Certification Roadmap | Azure Training For Beginners | Simplilearn
🔥 Azure Cloud Architect Master's Program (Discount Code: YTBE15): https://www.simplilearn.com/azure-cloud-architect-certification-training-course?utm_campaign=AzureCertificationPath-JXUdhgKJGko&utm_medium=Descriptionff&utm_source=youtube 🔥 Caltech Cloud Computing Bootcamp (US Only): https:
From playlist Cloud Computing Tutorial For Beginners 🔥[2023 Updated]

OWASP AppSecUSA 2012: Building Predictable Systems Using Behavioral Security Modeling
Speaker: John Benninghoff Behavioral Security Modeling (BSM), first presented at AppSec USA 2011 in Minneapolis, was conceived as a way of modeling interactions between information and people in terms of socially defined roles and the expected behaviors of the system being designed. By re
From playlist OWASP AppSecUSA 2012

CompTIA Security+ Certification | CompTIA Security+ SY0-601 | Cybersecurity Training | Edureka
🔥Edureka CompTIA Security+ Certification Training: https://www.edureka.co/comptia-security-plus-certification-training This Edureka video on 'CompTIA Security+ Certification' will give you all the details about the latest CompTIA Security+ Certification including the exam details. Here are
From playlist Cyber Security Training for Beginners | Edureka

CERIAS Security: Tor: Anonymous communications for government agencies, corporations and you 7/7
Clip 7/7 Speakers: Paul Syverson & Roger Dingledine What do the Department of Defense and the Electronic Frontier Foundation have in common? They have both funded the development of Tor (torproject.org), a free-software anonymizing network that helps people around the world use the In
From playlist The CERIAS Security Seminars 2008

Networking Services in AWS | Top Networking services in AWS | AWS Training | Edureka | AWS Live - 3
🔥Edureka AWS Architect Training: https://www.edureka.co/aws-certification-training This Edureka "Networking Services in AWS” video will introduce you to the top networking services provided by AWS. Check out our AWS Playlist: https://goo.gl/8qrfKU 🔴Subscribe to our channel to get video u
From playlist Edureka Live Classes 2020

Going Hungry is not Great for your Health
About 50 million people in the United States don't have access to enough food to support a healthy lifestyle. The technical term for this is food insecurity, and over 40% of people in the United States will experience it during their adult lives. This pervasive problem has a lot of associa
From playlist Healthcare Triage

How to create EC2 Instance in AWS | AWS EC2 Tutorial | AWS Tutorial | Edureka | AWS Rewind - 3
🔥Edureka AWS Architect Training: https://www.edureka.co/aws-certification-training This Edureka's How to create EC2 Instance in AWS will help you learn one of the key AWS services called AWS EC2 and it also includes a demo on launching an AWS EC2 instance.This AWS EC2 tutorial is important
From playlist AWS Tutorial Videos

CERIAS Security: Tor: Anonymous communications for government agencies, corporations and you 4/7
Clip 4/7 Speakers: Paul Syverson & Roger Dingledine What do the Department of Defense and the Electronic Frontier Foundation have in common? They have both funded the development of Tor (torproject.org), a free-software anonymizing network that helps people around the world use the In
From playlist The CERIAS Security Seminars 2008

How to create EC2 Instance in AWS | AWS EC2 Tutorial | AWS Tutorial | Edureka | AWS Rewind - 4
🔥Edureka AWS Architect Training: https://www.edureka.co/aws-certification-training This Edureka's How to create EC2 Instance in AWS will help you learn one of the key AWS services called AWS EC2 and it also includes a demo on launching an AWS EC2 instance.This AWS EC2 tutorial is important
From playlist AWS Tutorial Videos

CERIAS Security: Tor: Anonymous communications for government agencies, corporations and you 3/7
Clip 3/7 Speakers: Paul Syverson & Roger Dingledine What do the Department of Defense and the Electronic Frontier Foundation have in common? They have both funded the development of Tor (torproject.org), a free-software anonymizing network that helps people around the world use the In
From playlist The CERIAS Security Seminars 2008

