
C34 Expanding this method to higher order linear differential equations
I this video I expand the method of the variation of parameters to higher-order (higher than two), linear ODE's.
From playlist Differential Equations

(2.3.1) Introduction to Higher Order Linear Differential Equations and Related Theorem
The video introduces higher order linear differential equations and related theorems on superposition, existence and uniqueness, and linear independence. https://mathispower4u.com
From playlist Differential Equations: Complete Set of Course Videos
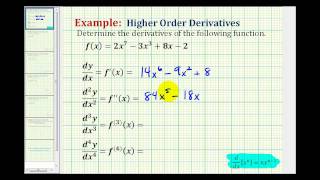
Ex 1: Determine Higher Order Derivatives
This video provides an example of how to determine the first, second, third, and fourth derivative of a function. Complete Video List at http://www.mathispower4u.com
From playlist Higher Order Differentiation

11_8_1 Higher Order Partial Derivatives Part 1
Just as there are second, third, and higher-order derivatives in single variable calculus, so there are higher-order partial derivatives in multivariable calculus. the only differences being that these are partial derivatives and the can be combined in certain orders.
From playlist Advanced Calculus / Multivariable Calculus

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security
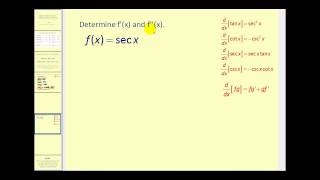
Higher Order Derivatives of Trigonometric Functions
The video explains how to determine higher order derivatives of trigonometric functions. http://mathispower4u.wordpress.com/
From playlist Differentiation

Reduction of Order - Linear Second Order Homogeneous Differential Equations Part 2
This video explains how to apply the method of reduction of order to solve a linear second order homogeneous differential equations. Site: http://mathispower4u
From playlist Second Order Differential Equations: Reduction of Order

C81 More complex Laplace tranformations
Building on the initial set of Laplace transforms to more complex expressions.
From playlist Differential Equations

I continue the look at higher-order, linear, ordinary differential equations. This time, though, they have variable coefficients and of a very special kind.
From playlist Differential Equations

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

CERIAS Security: Recent Attacks on MD5 4/6
Clip 4/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

High-Order Ordinary Differential Equations with More Derivatives (from Physics)
Here we show how to derive higher-order differential equation systems, with higher-order derivatives, from F=ma by chaining together simple systems. Our example is combining two spring-mass systems to get a fourth order equation. Playlist: https://www.youtube.com/playlist?list=PLMrJAk
From playlist Engineering Math: Differential Equations and Dynamical Systems

Lilya Budaghyan : On APN and AB power functions
CONFERENCE Recording during the thematic meeting : « ALgebraic and combinatorial methods for COding and CRYPTography» the February 23, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent Find this video and other talks given b
From playlist Combinatorics

Block Ciphers and Data Encryption Standard (DES) - Part 1
Fundamental concepts of Block Cipher Design Principles are discussed. DES is presented. Differential and linear cryptanalysis are explained . Block Cipher Principles Data Encryption Standard (DES) Differential and Linear Cryptanalysis Block Cipher Design Principles
From playlist Network Security

Cryptanalysis of Vigenere cipher: not just how, but why it works
The Vigenere cipher, dating from the 1500's, was still used during the US civil war. We introduce the cipher and explain a standard method of cryptanalysis based on frequency analysis and the geometry of vectors. We focus on visual intuition to explain why it works. The only background
From playlist Classical Cryptography

Block Ciphers and Data Encryption Standard (DES): Part 2
Fundamental concepts of Block Cipher Design Principles are discussed. Differential cryptanalysis and linear cryptanalysis are explained.
From playlist Network Security

CERIAS Security: Recent Attacks on MD5 5/6
Clip 5/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

CERIAS Security: Recent Attacks on MD5 6/6
Clip 6/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006

(2.3.2) Intro to Higher Order Linear Homogeneous Differential Equations wit Constant Coefficients
This video introduces higher order linear homogeneous differential equations with constant coefficients. https://mathispower4u.com
From playlist Differential Equations: Complete Set of Course Videos

Overview on Modern Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security