How from DC motor to AC generator 2!!!
In this video i show how from DC motor can make AC current. Enjoy!!!
From playlist ELECTROMAGNETISM

How from DC motor to AC generator!!!
In this video i show how from DC motor can make AC current. Enjoy!!!
From playlist ELECTROMAGNETISM

Inside an Inverter Generator, Car Alternator, AC
Inside an Inverter generator. This video explains what is the difference between an Inverter Generator and a Regular Generator. Also explains why car alternators are not the best choice for wind turbines. DC generator or DC motors work for power generation. The most efficient generator is
From playlist DIY ALTERNATOR WIND TURBINE

http://www.mekanizmalar.com/napier_deltic_engine.html Working principle of a Napier Deltic Engine.
From playlist Engines

Pseudorandom Number Generation and Stream Ciphers
Fundamental concepts of Pseudorandom Number Generation are discussed. Pseudorandom Number Generation using a Block Cipher is explained. Stream Cipher & RC4 are presented.
From playlist Network Security

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

A Tutorial on Network Protocols
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Andreas Antonopoulos on Bitcoin Wallet Encryption
In this video, Andreas Antonopoulos covers Elliptic Curve Crypto (ECC) & EC Digital Signature Algorithm (ECDSA), Key formats (hex, compressed, b58, b58check, Key types, Key mnemonic word list (BIP0039), and Key encryption (BIP0038).
From playlist Bitcoin Talks by Andreas M. Antonopoulos

Live CEOing Ep 544: Language Design in Wolfram Language [Ciphers & WFR Submissions] [Part 01]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

RSA and DSA Encryption Algorithms Explained | Cryptography & Network Security Tutorial | Simplilearn
In today's video on the RSA and DSA encryption algorithms explained, we cover the two most well known symmetric encryption algorithms in our cryptography & network security tutorial. We learn the steps needed to encrypt digital signatures and general data using RSA and DSA algorithms. The
From playlist Cyber Security Playlist [2023 Updated]🔥

The private key: How to digitally sign a message?
In this video we're going in some depth on what it means to sign a message cryptographically with a public-key private-key scheme. Here I use an Ethereum blockchain python library and its elliptic curve.
From playlist Programming

Stanford Seminar - How Not to Generate Random Numbers
"How not to generate random numbers" - Nadia Heninger of University of Pennsylvania Colloquium on Computer Systems Seminar Series (EE380) presents the current research in design, implementation, analysis, and use of computer systems. Topics range from integrated circuits to operating syst
From playlist Engineering

Live CEOing Ep 216: Cryptography in Wolfram Language
Watch Stephen Wolfram and teams of developers in a live, working, language design meeting. This episode is about Cryptography in the Wolfram Language.
From playlist Behind the Scenes in Real-Life Software Design

Speakers: djb | Nadia Heninger | Tanja Lange RSA factorization in the real world RSA is the dominant public-key cryptosystem on the Internet. This talk will explain the state of the art in techniques for the attacker to figure out your secret RSA keys. A typical 1024-bit RSA public key
From playlist 29C3: Not my department

How To Create Bitcoin Wallet From Scratch In C | Session 03 | #blockchain
Don’t forget to subscribe! In this project series, you will learn to create a Bitcoin wallet from scratch in C. This project will take you through all the steps to help you create a Bitcoin wallet. Through this series, you will learn about Bitcoin, C language, and the Nbitcoin library.
From playlist Create Bitcoin Wallet From Scratch In C

Cyber Security Week Day - 1 |Cryptography Full Course | Cryptography & Network Security| Simplilearn
🔥Advanced Executive Program In Cybersecurity: https://www.simplilearn.com/pgp-advanced-executive-program-in-cyber-security 🔥Caltech Cybersecurity Bootcamp(US Only): https://www.simplilearn.com/cybersecurity-bootcamp This video on Cryptography full course will acquaint you with cryptograph
From playlist Simplilearn Live
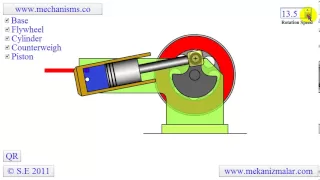
http://www.mekanizmalar.com A wobbler is usually the first type engine made by small engine builders. The wobbler does not need tiny moving valves which makes manufacturing simple.
From playlist Engines