Compute D Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Security Of RSA - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Correctness Of RSA - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

RSA Conference USA 2010: Will the Internet Ever Be Secure? Not Without Trust 1/3
Clip 1/3 Speaker: James Bidzos, Executive Chairman, VeriSign, Inc. Technologies and policies are important, but the future of Internet security rests upon trust. Without trust, people and organizations wont freely share information or purchase online. VeriSign has been building trust
From playlist RSA Conference USA 2010

Summary - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Invertibility Of RSA Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Security Of Rsa Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Nadia Heninger | djb | Tanja Lange This was a busy year for crypto. TLS was broken. And then broken again. Discrete logs were computed. And then computed again.
From playlist 30C3
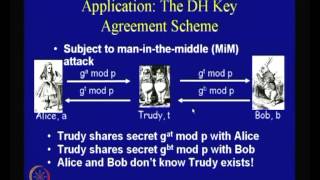
The Diffie-Hellman Problem and Security of ElGamal Systems
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

RSA Conference 2010 USA: The Cryptographers Panel 3/6
Clip 3/6 MODERATOR: Ari Juels, Chief Scientist and Director, RSA Laboratories PANELISTS: Whitfield Diffie, Martin Hellman, Ronald Rivest, Adi Shamir, Brian Snow Join the founders of the field for an engaging discussion about the latest advances in cryptography, research areas to wa
From playlist RSA Conference USA 2010

OWASP AppSecUSA 2011:How NOT to Implement Cryptography for the OWASP Top 10 (Reloaded)
Speaker: Anthony J. Stieber This talk is an update of a talk in 2008 at the OWASP Minneapolis-St.Paul Chapter which was about encryption as it applies to parts of the OWASP Top Ten. The new talk uses fresh examples of application cryptography successes and failures, and also incorporates
From playlist OWASP AppSecUSA 2011

RSA Conference USA 2010: Will the Internet Ever Be Secure? Not Without Trust 3/3
Clip 3/3 Speaker: James Bidzos, Executive Chairman, VeriSign, Inc. Technologies and policies are important, but the future of Internet security rests upon trust. Without trust, people and organizations wont freely share information or purchase online. VeriSign has been building trust
From playlist RSA Conference USA 2010

Stanford Seminar - The Evolution of Public Key Cryptography
EE380: Computer Systems Colloquium Seminar The Evolution of Public Key Cryptography Speaker: Martin Hellman, Stanford EE (Emeritus) While public key cryptography is seen as revolutionary, after this talk you might wonder why it took Whit Diffie, Ralph Merkle and Hellman so long to discov
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

The Year in Post-quantum Crypto
The world is finally catching on to the urgency of deploying post-quantum cryptography: cryptography designed to survive attacks by quantum computers. EVENT: media.ccc.de 2018 SPEAKERS: Daniel J. Bernstein and Tanja Lange PUBLICATION PERMISSIONS: Original video was published with the
From playlist Blockchain
Side Channel Analysis of Cryptographic Implementations
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

30C3: The Year in Crypto (DE - translated)
For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speakers: Nadia Heninger | djb | Tanja Lange This was a busy year for crypto. TLS was broken. And then broken again. Discrete logs were computed. And then computed again.
From playlist 30C3

Limit Theorems for Spatial Interacting Models by Yogeshwaran D
PROGRAM: TOPICS IN HIGH DIMENSIONAL PROBABILITY ORGANIZERS: Anirban Basak (ICTS-TIFR, India) and Riddhipratim Basu (ICTS-TIFR, India) DATE & TIME: 02 January 2023 to 13 January 2023 VENUE: Ramanujan Lecture Hall This program will focus on several interconnected themes in modern probab
From playlist TOPICS IN HIGH DIMENSIONAL PROBABILITY