
How to Determine if Functions are Linearly Independent or Dependent using the Definition
How to Determine if Functions are Linearly Independent or Dependent using the Definition If you enjoyed this video please consider liking, sharing, and subscribing. You can also help support my channel by becoming a member https://www.youtube.com/channel/UCr7lmzIk63PZnBw3bezl-Mg/join Th
From playlist Zill DE 4.1 Preliminary Theory - Linear Equations

The TRUTH about TENSORS, Part 4: The Multiverse
In this video, I sketch the details of the proof that tensor products are commutative and associative. I then define multi-linear maps, which are essential for future videos. Commutativity: (0:00) Associativity: (5:40) Multi-linearity: (15:18)
From playlist The TRUTH about TENSORS

Local linearity for a multivariable function
A visual representation of local linearity for a function with a 2d input and a 2d output, in preparation for learning about the Jacobian matrix.
From playlist Multivariable calculus

Determine If an Ordered Pair is a Solution to a Linear Equation
This video explains how to determine if an ordered pair is a solution to a given linear equation. http://mathispower4u.com
From playlist Graphing Linear Equations Using a Table of Values

Determine if an Ordered Pair is a Solution to a System of Linear Equations
This video explains how to determine if an ordered pair is a solution to a system of linear equations. http://mathispower4u.com
From playlist Solving Systems of Linear Inequalities

In this video, I present a very classical example of a duality argument: Namely, I show that T^T is one-to-one if and only if T is onto and use that to show that T is one-to-one if and only if T^T is onto. This illustrates the beautiful interplay between a vector space and its dual space,
From playlist Dual Spaces
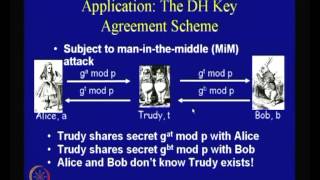
The Diffie-Hellman Problem and Security of ElGamal Systems
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Determine if an Ordered Pair is a Solution to a System of Linear Inequalities
This video explains how to determine if an ordered pair is a solution to a system of linear inequalities. http://mathispower4u.com
From playlist Solving Systems of Linear Inequalities

‘External’ and 'Internal' Drivers of the Indian monsoon (Lecture 9) by B N Goswami
ICTS Summer Course 2022 (www.icts.res.in/lectures/sc2022bng) Title : Introduction to Indian monsoon Variability, Predictability, and Teleconnections Speaker : Professor B N Goswami (Cotton University) Date : 23rd April onwards every week o
From playlist Summer Course 2022: Introduction to Indian monsoon Variability, Predictability, and Teleconnections

On The Complexity of Computing Roots and Residuosity Over Finite Fields - Swastik Kopparty
Swastik Kopparty Member, School of Mathematics February 1, 2011 We study the complexity of computing some basic arithmetic operations over GF(2^n), namely computing q-th root and q-th residuosity, by constant depth arithmetic circuits over GF(2) (also known as AC^0(parity)). Our main resul
From playlist Mathematics

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Adeline Roux-Langlois : Using structured variants in lattice-based cryptography - Lecture 1
CONFERENCE Recording during the thematic meeting : « Francophone Computer Algebra Days» the March 06, 2023 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Jean Petit Find this video and other talks given by worldwide mathematicians on CIRM's Audiov
From playlist Mathematical Aspects of Computer Science

Monsoon Intra-seasonal Variability (ISV) (Lecture 10) by B N Goswami
ICTS Summer Course 2022 (www.icts.res.in/lectures/sc2022bng) Title : Introduction to Indian monsoon Variability, Predictability, and Teleconnections Speaker : Professor B N Goswami (Cotton University) Date : 23rd April onwards every week o
From playlist Summer Course 2022: Introduction to Indian monsoon Variability, Predictability, and Teleconnections
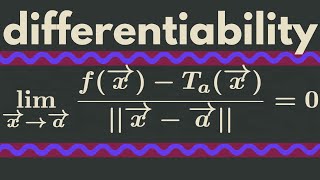
Multivariable Calculus | Differentiability
We give the definition of differentiability for a multivariable function and provide a few examples. http://www.michael-penn.net https://www.researchgate.net/profile/Michael_Penn5 http://www.randolphcollege.edu/mathematics/
From playlist Multivariable Calculus

CERIAS Security: Sphinx: A Compact and Provably Secure Mix Format 4/6
Clip 4/6 Speaker: Ian Goldberg · University of Waterloo Mix networks, originally proposed in 1981, provide a way for Internet users to send messages--such as email, blog posts, or tweets--without automatically revealing their identities or their locations. In this talk, we will describe
From playlist The CERIAS Security Seminars 2009

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security

DH Security - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Multivariable chain rule intuition
Get a feel for what the multivariable is really saying, and how thinking about various "nudges" in space makes it intuitive.
From playlist Multivariable calculus
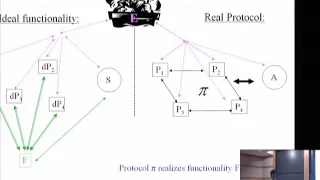
A Completeness Theorem for Pseudo-Linear Functions with App... - Charanjit Jutla
Charanjit Jutla IBM T. J. Watson Research Center February 28, 2010 We prove completeness results for certain class of functions which have implications for automatic proving of universally-composable security theorems for ideal and real functionalities composed of if-then-else programs wi
From playlist Mathematics
