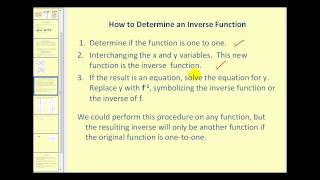
(New Version Available) Inverse Functions
New Version: https://youtu.be/q6y0ToEhT1E Define an inverse function. Determine if a function as an inverse function. Determine inverse functions. http://mathispower4u.wordpress.com/
From playlist Exponential and Logarithmic Expressions and Equations

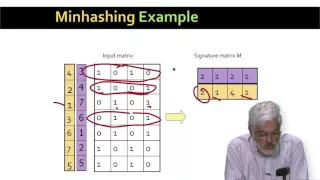
Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Define an inverse function. Determine if a function as an inverse function. Determine inverse functions.
From playlist Determining Inverse Functions

Lec 8 | MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503), Fall 2005
Lecture 08: Universal Hashing, Perfect Hashing View the complete course at: http://ocw.mit.edu/6-046JF05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.046J / 18.410J Introduction to Algorithms (SMA 5503),
MIT 6.006 Introduction to Algorithms, Spring 2020 Instructor: Jason Ku View the complete course: https://ocw.mit.edu/6-006S20 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63EdVPNLG3ToM6LaEUuStEY Hashing allows for faster search and dynamic operations on data structur
From playlist MIT 6.006 Introduction to Algorithms, Spring 2020

MIT 6.046J Design and Analysis of Algorithms, Spring 2015 View the complete course: http://ocw.mit.edu/6-046JS15 Instructor: Ling Ren In this recitation, problems related to dynamic programming are discussed. License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms
From playlist MIT 6.046J Design and Analysis of Algorithms, Spring 2015

Lecture 8: Hashing with Chaining
MIT 6.006 Introduction to Algorithms, Fall 2011 View the complete course: http://ocw.mit.edu/6-006F11 Instructor: Erik Demaine License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.006 Introduction to Algorithms, Fall 2011