
Cryptographic Hash Functions: Part 1
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

Cryptographic Hash Functions: Part 2
Cryptographic Hash Functions Applications of Crypto Hash Functions Birthday Problem Secure Hash Algorithm (SHA)
From playlist Network Security

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Clip 5/7 Speaker: Dan Kaminsky For more information go to: http://events.ccc.de/congress/2009/Fahrplan/events/3658.en.html
From playlist 26C3: Here be dragons day 3

From playlist Cryptography Lectures

Top Hashing Algorithms In Cryptography | MD5 and SHA 256 Algorithms Explained | Simplilearn
In this video on Top Hashing Algorithms In Cryptography, we will cover the technical aspects of hashing while going through some well-known hash functions and algorithms at the end. We cover the basics of cryptography and its applications. We also have detailed MD5 and SHA265 Explained sec
From playlist Cyber Security Playlist [2023 Updated]🔥

Clip 4/7 Speaker: Dan Kaminsky For more information go to: http://events.ccc.de/congress/2009/Fahrplan/events/3658.en.html
From playlist 26C3: Here be dragons day 3

Cryptographic Hash Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptography Tutorial For Beginners | Cybersecurity Training | Edureka | Cybersecurity Live - 2
🔥Edureka Cyber Security Course: https://www.edureka.co/cybersecurity-certification-training This Edureka video on "Cryptography Tutorial" gives an introduction to the Cryptography and talks about its basic concepts. 🔴Subscribe to our channel to get video updates. Hit the subscribe butto
From playlist Edureka Live Classes 2020
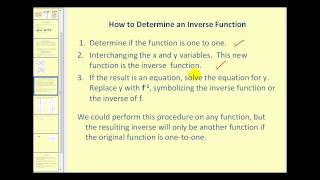
(New Version Available) Inverse Functions
New Version: https://youtu.be/q6y0ToEhT1E Define an inverse function. Determine if a function as an inverse function. Determine inverse functions. http://mathispower4u.wordpress.com/
From playlist Exponential and Logarithmic Expressions and Equations

the evolution of my c++ openGL MD2 reader. I wrote the code for the program but the model and its animation is not mine.
From playlist 3D Programming

C# Delegates Explained | C# Delegates And Events Tutorial | C# Delegates Example | Simplilearn
🔥Post Graduate Program In Full Stack Web Development: https://www.simplilearn.com/pgp-full-stack-web-development-certification-training-course?utm_campaign=CSharpDelegates-vOlLd2SsKM4&utm_medium=DescriptionFF&utm_source=youtube 🔥Caltech Coding Bootcamp (US Only): https://www.simplilearn.co
From playlist C# Training 🔥[2022 Updated]

How To Create A Currency Converter Web App | Session 05 | #HTML5 | #Springboot
Don’t forget to subscribe! This project series will guide you on how to build a complete currency converter web app for converting between monetary currencies. The project is divided into two parts: frontend design for the web app and backend design. The Frontend will be designed using s
From playlist Create A Currency Converter Web App
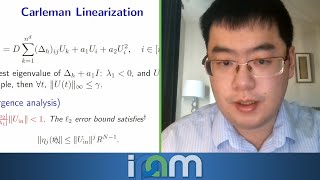
Jin-Peng Liu - Efficient quantum algorithms for nonlinear ODEs and PDEs - IPAM at UCLA
Recorded 27 January 2022. Jin-Peng Liu of the University of Maryland presents "Efficient quantum algorithms for nonlinear ODEs and PDEs" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: Nonlinear dynamics play a prominent role in many domains and are notoriously difficult to
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Top C# Interview Questions And Answers | C# Interview Preparation | C# Training | Simplilearn
This video covers the Top C# Interview Questions and Answers. You will learn the best C# interview questions that are frequently asked to freshers as well as experienced professionals. Learn the conceptual and practical questions to ace C# interview. 🔥 Explore our FREE Courses with Comp
From playlist C# Training 🔥[2022 Updated]

How To Build E-Learning Website In ASP.net / C# | Session 03 | #aspnet | #programming
Don’t forget to subscribe! In this project, you will learn to build an E-learning website in ASP.net and C#. This project consists of detailed system analysis and design techniques for creating a web app like an e-learning website. from database design to final working c# code, this pro
From playlist Build E-Learning Website In ASP.net / C#

From playlist Cryptography Lectures

How To Create Crime Incident Web App In C# | Session 03 | #webapp | #programming
Don’t forget to subscribe! In this tutorial, you will learn to create a crime incident reporting web app in C#. Through this series, we are going to look at the Crimeometer API and create a crime aware app out of it by calling its API functions This project would teach you how to cal
From playlist Create Crime Incident Web App In C#

