
Other Public Key Cryptosystems: Part 1
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

Other Public Key Cryptosystems: Part 2
Fundamental concepts of Diffie-Hellman Key exchange are discussed. ElGamal Cryptosystem is presented. Elliptic curves are Analyzed.
From playlist Network Security

This video gives a general introduction to cryptography WITHOUT actually doing any math. Terms covered include cryptology vs cryptography vs cryptanalysis, symmetric vs public key systems, and "coding theory." NOTE: Yes, I said and wrote "cryptOanalysis" when it's actually "cryptanalysis
From playlist Cryptography and Coding Theory

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Stanford Seminar - The Evolution of Public Key Cryptography
EE380: Computer Systems Colloquium Seminar The Evolution of Public Key Cryptography Speaker: Martin Hellman, Stanford EE (Emeritus) While public key cryptography is seen as revolutionary, after this talk you might wonder why it took Whit Diffie, Ralph Merkle and Hellman so long to discov
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

Primality (1 of 2: Fermat's Test)
From playlist Cryptography

A History of Primes - Manindra Agrawal [2002]
2002 Annual Meeting Clay Math Institute Manindra Agrawal, American Academy of Arts and Sciences, October 2002
From playlist Number Theory

26C3: How you can build an eavesdropper for a quantum cryptosystem 2/6
Clip 2/6 Speakers: Qin Liu ,Sebastien Sauge This presentation will show the first experimental implementation of an eavesdropper for quantum cryptosystem. Although quantum cryptography has been proven unconditionally secure, by exploiting physical imperfections (detector vulnerabilit
From playlist 26C3: Here be dragons day 1

Asymmetric Cryptosystems - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Nexus Trimester - Delaram Kahrobaei (City University of New York)
Cryptosystems Based on Group-Theoretic Problems: A Survey, New Results, Open Problems Delaram Kahrobaei (City University of New York) March 31, 2016 Abstract: In this talk I will survey some of the cryptosystems based on group theoretic problems and their computational complexity such as
From playlist Nexus Trimester - 2016 - Secrecy and Privacy Theme

One Way Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptanalysis of Classical Ciphers
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

26C3: Yes We Cant - on kleptography and cryptovirology 5/6
Clip 5/6 Speaker: Moti Yung In this talk I will survey some of the results (with Adam Young) on Cryptovirology (the art of employing public key cryptography maliciously as part of a malware attack, such as in ransomware) and the related Kleptography (the art of embedding cryptographic
From playlist 26C3: Here be dragons day 3
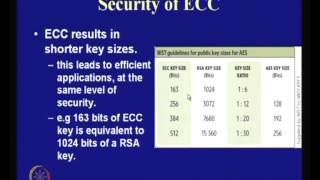
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Discrete Logarithm Problem (DLP)
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Few other Cryptanalytic Techniques
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security


