
Recursive Functions (Discrete Math)
This video introduces recursive formulas.
From playlist Functions (Discrete Math)
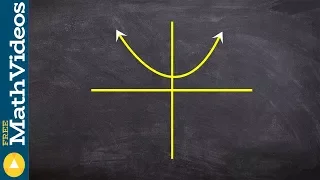
Using the vertical line test to determine if a graph is a function or not
👉 Learn how to determine whether relations such as equations, graphs, ordered pairs, mapping and tables represent a function. A function is defined as a rule which assigns an input to a unique output. Hence, one major requirement of a function is that the function yields one and only one r
From playlist What is the Domain and Range of the Function

Determine if a Function is a Polynomial Function
This video explains how to determine if a function is a polynomial function. http://mathispower4u.com
From playlist Determining the Characteristics of Polynomial Functions

Determine Function Values for a Recursive Functions
This video provides examples of how to determine function values given a recursive function.
From playlist Functions (Discrete Math)
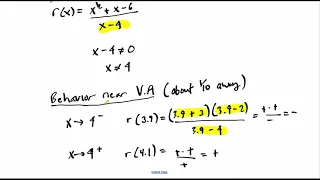
In this video we cover some rational function fundamentals, including asymptotes and interecepts.
From playlist Polynomial Functions

How to find the left and right hand limit by not using a calculator
👉 Learn how to evaluate the limit of a function involving rational expressions. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The limit of a function is usually evaluated by direct subst
From playlist Evaluate the Limit..........Help!

How to determine if a set of points is a function, onto, one to one, domain, range
👉 Learn how to determine whether relations such as equations, graphs, ordered pairs, mapping and tables represent a function. A function is defined as a rule which assigns an input to a unique output. Hence, one major requirement of a function is that the function yields one and only one r
From playlist What is the Domain and Range of the Function

👉 Learn how to evaluate the limit of a function involving rational expressions. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The limit of a function is usually evaluated by direct subst
From playlist Evaluate the Limit..........Help!

Zero Knowledge Proofs - Seminar 5 - NP languages have zero knowledge proofs
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs). This seminar covers the 1991 proof by Goldreich-Micali-Widgerson that every NP language has a zero knowledge proof. You can join this semi
From playlist Metauni

Zero Knowledge Proofs - Seminar 4 - From interactive to non-interactive
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs). This seminar explains how to construct *non-interactive* ZKPs which are much more practical than the schemes discussed so far in the semina
From playlist Metauni
Zero Knowledge Proofs - Seminar 4 - Non-interactive Zero Knowledge
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs). This seminar continues the development of non-interactive Zero Knowledge protocols, closing in on systems that can be used in practice. Yo
From playlist Metauni

Derandomization and its connections throughout complexity theory - Liije Chen
Computer Science/Discrete Mathematics Seminar II Topic: Derandomization and its connections throughout complexity theory Speaker: Liije Chen Affiliation: Massachusetts Institute of Technology Date: February 22, 2022 This is the second talk in a three-part series presented together with R
From playlist Mathematics

The Abel lectures: László Lovász and Avi Wigderson
0:30 Introduction by the Abel Prize Committee Chair, Hans Munthe-Kaas 02:42 László Lovász: Continuous limits of finite structures 49:27 Questions and answers 1:00:31 Avi Wigderson: The Value of Errors in Proofs 1:41:24 Questions and answers 1:50:20 Final remarks by John Grue, Chair of the
From playlist Abel Lectures

Guy Rothblum : Privacy and Security via Randomized Methods - 4
Recording during the thematic meeting: «Nexus of Information and Computation Theories » theJanuary 28, 2016 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent
From playlist Nexus Trimester - 2016 -Tutorial Week at CIRM

Jonathan Katz - Introduction to Cryptography Part 3 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography III" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will introduce the notions of zero-knowledge proofs, proofs of knowledge, and secure
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

L'Hopital's Rule sine x over x
👉 Learn how to evaluate the limit of a function involving trigonometric expressions. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The limit of a function is usually evaluated by direct
From playlist Evaluate Limits with Trig

Zero Knowledge Proofs - Seminar 8 - Completing the story of ZKSNARKS
This seminar series is about the mathematical foundations of cryptography. In this series Eleanor McMurtry is explaining Zero Knowledge Proofs (ZKPs). Last time Eleanor covered SNARKS, Succinct Non-interactive ARgument of Knowledge. Today this is extended to include: - Zero-knowledge - Ho
From playlist Metauni

How does Schnorr Signature Work?
Describe the theoretical aspect of Schnorr digital signature.
From playlist crypto

Efficient Zero Knowledge Proofs - A Modular Approach (Lecture 2) by Yuval Ishai
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

Using tiny numbers to evaluate the right hand limit of a rational function
👉 Learn how to evaluate the limit of a function involving rational expressions. The limit of a function as the input variable of the function tends to a number/value is the number/value which the function approaches at that time. The limit of a function is usually evaluated by direct subst
From playlist Evaluate the Limit (PC)