
In this video I briefly explain what minimum distance is and why it is helpful. Then I explain how to find it "the long way" and the "shortcut." Also during the process, I explain what Hamming Weight and Distance are and how to find them. Codewords from Generating Matrix Video: https://w
From playlist Cryptography and Coding Theory

2 2 Computing Minimum Edit Distance 5 54
From playlist CS124 - Full Course
Maximum and Minimum of a set In this video, I define the maximum and minimum of a set, and show that they don't always exist. Enjoy! Check out my Real Numbers Playlist: https://www.youtube.com/playlist?list=PLJb1qAQIrmmCZggpJZvUXnUzaw7fHCtoh
From playlist Real Numbers

Finding the Class Limits, Width, Midpoints, and Boundaries from a Frequency Table
Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys Finding the Class Limits, Width, Midpoints, and Boundaries from a Frequency Table
From playlist Statistics

Maximum and Minimum Values (Closed interval method)
A review of techniques for finding local and absolute extremes, including an application of the closed interval method
From playlist 241Fall13Ex3

One Time Pad - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Finding the Minimum Number - Integer Word Problem
In this video, I go through a minimum number integer word problem. The question focuses on finding the minimum number of buses needed to transport 151 students to a football game. The buses involved can hold 25 and 34 people, and the goal is to use as few buses as possible with as few left
From playlist PreAlgebra
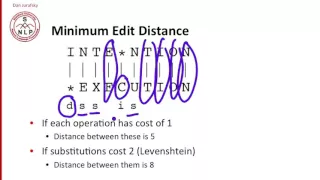
2 1 Defining Minimum Edit Distance 7 04
From playlist CS124 - Full Course

MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: George Verghese This lecture starts with historical applications of error control and convolutional codes in space programs. Convolutional codes are
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

NEURAL Bellman-Ford NETWORK - 2022 Neural BFNet - Graph Neural Networks w/ Link Prediction AI
Neural Bellman-Ford Networks - A brand-new representation learning framework based on paths for link prediction: A. representation of a pair of nodes as the generalized sum of all path representations between the nodes, B. with each path representation as the generalized product of the e
From playlist Learn Graph Neural Networks: code, examples and theory
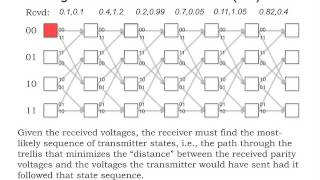
MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012 View the complete course: http://ocw.mit.edu/6-02F12 Instructor: George Verghese This lecture starts with a review of encoding and decoding. The Viterbi algorithm, which includes a branch netric and a path metric,
From playlist MIT 6.02 Introduction to EECS II: Digital Communication Systems, Fall 2012

Shannon 100 - 28/10/2016 - Ruediger URBANK
Happy Numbers: 68 Years of Coding, 6² + 8² = 100 Years of Shannon, 1² + 0² + 0² = 1 Goal Ruediger Urbank (EPFL) This year, we celebrate Shannon’s 100th birthday and it has been 68 years since he laid the foundations of communications. To realize his number 1 goal or error free communica
From playlist Shannon 100

Stream archive: Recording videos for Axum course (2022-11-10)
Broadcasted live on Twitch -- Watch live at https://www.twitch.tv/brookzerker
From playlist Uncut Live Streams

What is Brute Force Attack? | Password Cracking Using Brute Force Attacks | Edureka
🔥Edureka CyberSecurity Course (Use code: YOUTUBE20) : https://www.edureka.co/cybersecurity-certification-training This Edureka video on "What is Brute Force Attack?" will give you an introduction to Brute Force Attacks. You will learn how hackers hack password using Brute Force Attack. Thi
From playlist Cyber Security Training for Beginners | Edureka

Seminar on Applied Geometry and Algebra (SIAM SAGA): Gretchen Matthews
Title: Multivariate Goppa Codes Speaker: Gretchen Matthews, Virginia Tech Date: Tuesday, May 10, 2022 at 11:00am Eastern Abstract: Goppa codes were introduced in 1971 by V. D. Goppa using a univariate polynomial g(x), called a generator polynomial, over a finite field. Properties of the G
From playlist Seminar on Applied Geometry and Algebra (SIAM SAGA)

Xavier Caruso: Ore polynomials and application to coding theory
In the 1930’s, in the course of developing non-commutative algebra, Ore introduced a twisted version of polynomials in which the scalars do not commute with the variable. About fifty years later, Delsarte, Roth and Gabidulin realized (independently) that Ore polynomials could be used to de
From playlist Algebraic and Complex Geometry

Algebra - Minimum and Maximum (4 of 4)
Visit http://ilectureonline.com for more math and science lectures! This video is part of a four part lecture in algebra where we'll take a look at problems involved in determining maximums and minimums such as the maximum area a fence of fixed length can enclose in the shape of a square
From playlist ALGEBRA 16 - FINDING MAXIMUM AND MINIMUM VALUES

Lec 22 | MIT 6.451 Principles of Digital Communication II
Lattice and Trellis Codes View the complete course: http://ocw.mit.edu/6-451S05 License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.451 Principles of Digital Communication II

