
Welcome to a slightly nerdy display of rodent fractal flames! What is a fractal flame? Well... "Fractal flames is a member of the iterated function system class of fractals created by Scott Draves in 1992. Draves' open-source code was later ported into Adobe After Effects graphics softwa
From playlist Nerdy Rodent Uploads!

Protect Your Computer from Malware | Federal Trade Commission
Malware is short for "malicious software." It includes viruses and spyware that get installed on your computer or mobile device without your consent. These programs can cause your device to crash and can be used to monitor and control your online activity. Learn more about how to avoid, d
From playlist Recommended videos

CIC News 24-08-2012: Gauss/Flame,DHS FNS,phishing
For the interactive Qwiki visit: http://bit.ly/CIC_240812 Mentioned articles: Gauss-pursuing researcher trips over Kaspersky-operated sinkhole: http://bit.ly/SxIaR2 New Gauss and Flame link was a mistake, researchers say: http://cnet.co/PDaSzB ADDITIONAL INFORMATION ON GAUSS AND FLAME LEA
From playlist Vlogs

Flare-On FireEye 2018 CTF - Malware Analysis With Amr Thabet - Flare Minesweeper
Hey guys! HackerSploit here back again with another video, in this video, I am joined by Amr Thabet, he is malware researcher. He used to work in Symantec in their Attack Investigation Team dealing with major attacks from NSA like Region and Stuxnet (he was one of the people who converted
From playlist Malware Analysis

DEFCON 14: Hacking Malware: Offense Is the New Defense
Speakers: Valsmith, Co-Founder, Offensive Computing Danny Quist, co-founder Offensive Computing Abstract: The proliferation of malware is a serious problem, which grows in sophistication and complexity every day, but with this growth, comes a price. The price that malware pays for advanc
From playlist DEFCON 14

CIC News 27-07-2012: Madi, ICS / SCADA, Android
For the interactive Qwiki visit: http://bit.ly/CIC_270712 Want to help collect and share news related to cybercrime en information security? Join the CIC Collaboration Project: Video: http://bit.ly/ciccollabv Website: http://cic.christiaan008.tk Twitter: https://twitter.com/christiaan008
From playlist Vlogs

Why can't you visit the Statue of Liberty's Torch? - IT'S HISTORY
👉 Grab Atlas VPN for 1.39$/mo before the deal expires! https://atlasv.pn/History Complete history of The Statue of Liberty - The Statue of Liberty has long stood as a beacon of light and hope for all of America. Built in France by renowned sculptor Frederic Auguste Bartholde, the story
From playlist New Jersey History
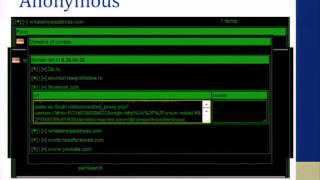
DEFCON 20: Owning Bad Guys {And Mafia} With Javascript Botnets
Speakers: CHEMA ALONSO SECURITY RESEARCHER, INFORMATICA64 MANU "THE SUR" PENETRATION TESTER, INFORMATICA64 Man in the middle attacks are still one of the most powerful techniques for owning machines. In this talk MITM schemas in anonymous services are going to be discussed. Then attendee
From playlist DEFCON 20

CIC News 19-09-2012: Flame, IE vuln, TDSS botnet
For the interactive Qwiki visit: http://bit.ly/CIC190912 Mentioned articles: Cyber clues link U.S. to new computer viruses: http://reut.rs/Rw4WFn Coders Behind the Flame Malware Left Incriminating Clues on Control Servers: http://bit.ly/OckcfI Have I Got Newsforyou: Analysis of Flamer C&C
From playlist Vlogs

Just a change of heart, fractal flame style. Geeky stuff about fractal flames: https://en.wikipedia.org/wiki/Fractal_flame #Fractal
From playlist Nerdy Rodent Uploads!

Fractal Flame, Let's go! (Day 1)
Now we begin our quest to better creating fractal flames... -- Watch live at https://www.twitch.tv/simuleios
From playlist Fractal

How the Krack Hack Breaks Wi-Fi Security
To support SciShow and learn more about Brilliant, go to https://brilliant.org/Scishow. After 14 years of going unnoticed, a vulnerability in Wi-Fi security was published last week. It's a serious problem, but it's already in the process of being fixed. We're conducting a survey of our v
From playlist Uploads

The Browser Wars Are Over -- Firefox Lost
Firefox still exists because it's good enough, not because people use it. Find us on Github -- https://github.com/mtwb47/ Follow us http://twitter.com/mtwb http://patreon.com/thelinuxcast http://twitter.com/thelinuxcast http://thelinuxcast.org #firefox #rant #web
From playlist Linux Rants

CIC News 9-7-2012: Duqu, EU, Monkif botnet
For the interactive Qwiki visit: http://bit.ly/recart_090712 Want to help collect and share news related to cybercrime en information security? Join the CIC Collaboration Project: Video: http://bit.ly/ciccollabv Website: http://cic.christiaan008.tk Twitter: https://twitter.com/christiaan
From playlist Vlogs

Stanford Seminar - Building a Trustworthy Business in the Post-Snowden Era
"Building a Trustworthy Business in the Post-Snowden Era" -Alex Stamos, Artemis Internet Colloquium on Computer Systems Seminar Series (EE380) presents the current research in design, implementation, analysis, and use of computer systems. Topics range from integrated circuits to operatin
From playlist Engineering

OWASP AppSecUSA 2012: Iran's Real Life Cyberwar
Speaker: Phillip Hallam-Baker The recent Stuxnet, Flame and CA compromises involving Comodo and DigiNotar had three common elements, each was government sponsored, each involved Iran and all three involved a PKI compromise. The presenter will share experience of dealing with the Iranian a
From playlist OWASP AppSecUSA 2012

OHM 2013: A holistic view of Firefox OS
For more information visit: http://bit.ly/OHM13_web To download the video visit: http://bit.ly/OHM13_down Playlist OHM 2013: http://bit.ly/OHM13_pl Speaker: Stefan Arentz Firefox OS is a new mobile operating system developed by Mozilla. It is built on web technology and is following the
From playlist OHM 2013

Gov 2.0 Expo 2010: Jeff Jonas, "Spear Phishing the Masses: When Open Data is Dark"
Jeff Jonas (IBM Entity Analytics), "Spear Phishing the Masses: When Open Data is Dark"
From playlist Gov 2.0 Expo 2010

In this disorganized video, Matt takes a look at possible Firefox alternatives. -----💲💲 Support the Show 💲💲-- http://patreon.com/thelinuxcast -- Follow us 🐧🐧 -- http://twitter.com/thelinuxcast http://twitter.com/mtwb Subscribe at http://thelinuxcast.org Contact us thelinuxcast@gmail.c
From playlist Linux Top 5
