
A great way to improve your skills when learning to code is by solving coding challenges. Solving different types of challenges and puzzles can help you become a better problem solver, learn the intricacies of a programming language, prepare for job interviews, learn new algorithms, and mo
From playlist Learn To Code
How to sign a document in Microsoft Word
Doing this tutorial for a friend! He needed to know how to write his signature in a word document. Here is how you do it!
From playlist Microsoft Word Tutorials

In this video, you’ll learn about HTML and how it is used to code webpages. We hope you enjoy! To learn more, check out our Basic HTML tutorial here: https://edu.gcfglobal.org/en/basic-html/ #whatishtml #htmlcode #learnhtml
From playlist HTML

Introduction to Computer Programming for beginners || Coding for beginners
Computer programming is the process of performing a particular computation (or more generally, accomplishing a specific computing result), usually by designing and building an executable computer program. Programming involves tasks such as analysis, generating algorithms, profiling algorit
From playlist Programming

The C programming language (unit 2) - 4 of 5 (old version; watch new version instead)
A continuation of discussing the C programming language. This unit goes more into depths on pointers and arrays. Visit http://codeschool.org
From playlist The C language (unit 2)

From playlist Week 9 2014

From playlist CS50 Shorts 2013

(IC 2.6) Prefix codes - remarks and what's next
Definition of a prefix code (a.k.a. prefix-free code a.k.a. instantaneous code) for lossless compression. A playlist of these videos is available at: http://www.youtube.com/playlist?list=PLE125425EC837021F
From playlist Information theory and Coding
O'Reilly Webcast: The Google+ History API
n this hands-on webcast presented by Jennifer Murphy, author of Developing with Google+, we will explore the Google+ platform and walk through the Google+ History API. In this webcast you will learn: What is the Google+ History API? Learn how your application can write moments to
From playlist O'Reilly Webcasts 2

Speaker: Collin Mulliner Symbian Exploit and Shellcode Development SymbianOS is one of the major smart phone operating system and has been around for many years still exploitation has not been researched yet. The lack of proper exploitation techniques is mostly due to the fact that until
From playlist 25C3: Nothing to hide

COMP1400 Week 5, Lecture 2
From playlist Programming for Designers - COMP1400-T2 (2011)

DeepSec 2011: Windows Pwn 7 OEM - Owned Every Mobile?
Speaker: Alex Plaskett The talk aims to provide an introduction into the Windows Phone 7 (WP7) security model to allow security professionals and application developers understand the unique platform security features offered. Currently very little public information is available about Wi
From playlist DeepSec 2011

0070 - [ C++ ] Signing AWS API requests
This is #70 in my series of live (Twitch) coding streams, working on various projects in C++. This stream I finished up the work on code to sign AWS API calls, passing all the valid Amazon signature 4 test cases! Notebook page: https://tinyurl.com/y8gqkaya -- Watch live at https://w
From playlist Excalibur

Jeff Erickson - Lecture 1 - Two-dimensional computational topology - 18/06/18
School on Low-Dimensional Geometry and Topology: Discrete and Algorithmic Aspects (http://geomschool2018.univ-mlv.fr/) Jeff Erickson (University of Illinois at Urbana-Champaign, USA) Two-dimensional computational topology - Lecture 1 Abstract: This series of lectures will describe recent
From playlist Jeff Erickson - School on Low-Dimensional Geometry and Topology: Discrete and Algorithmic Aspects

R Shiny for Data Science Tutorial – Build Interactive Data-Driven Web Apps
Learn how to build interactive data-driven web apps in R using the Shiny package. ✏️ Course developed by Chanin Nantasenamat (aka Data Professor). Check out his YouTube channel for more bioinformatics and data science tutorials: https://www.youtube.com/dataprofessor ⭐️ Code ⭐️ 💻 Apps 1-5
From playlist Introduction to R Shiny

When you learn a new language, like French or German or even English, you first learn how to read. Then you learn how to write. When you learn a new *programming* language, you first learn how to write. And that’s it. Imagine that you were never formally taught how to read. And that you w
From playlist Software Development

Simplified Oauth 2 0 -- NodeJS Tutorial
In this tutorial we look at how to build a "Sign in with Github" OAuth solution. We will use node to build the backend with 3 routes and a frontend to go with it with HTML, CSS and Javascript. We will also look at how to create a new OAuth application in Github.com. The routes we need ar
From playlist NodeJS

CS50P - Lecture 7 - Regular Expressions
This is CS50P, CS50's Introduction to Programming with Python. Enroll for free at https://cs50.edx.org/python. Slides, source code, and more at https://cs50.harvard.edu/python. Playlist at https://www.youtube.com/playlist?list=PLhQjrBD2T3817j24-GogXmWqO5Q5vYy0V. TABLE OF CONTENTS 00:00:0
From playlist CS50's Introduction to Programming with Python (CS50P) 2022

Not Everyone Should Code or 10 Signs That Programming Is Not For You
If you are confused about whether you should learn to program, then programming is probably not for you. You will pass years searching for questions about either you should learn or not. But then some people are already into programming but aren’t sure if they can make it their career or n
From playlist Learn To Code
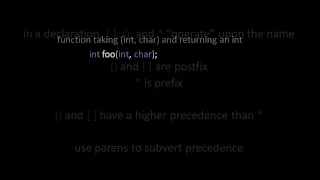
Introduction to the C programming language. Part of a larger series teaching programming. See http://codeschool.org
From playlist The C language