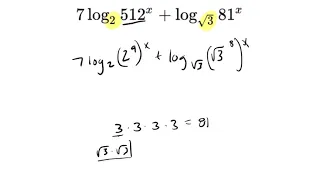
In this video, we simplify a logarithm.
From playlist Logs - Worked Examples

What are natural logarithms and their properties
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Ex: Determine the Value of a Number on a Logarithmic Scale (Log Form)
This video explains how to determine the value of several numbers on a logarithmic scale scaled in logarithmic form. http://mathispower4u.com
From playlist Using the Definition of a Logarithm

What are the properties of logarithms and natural logarithms
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

This is an worked example of logarithms in Algebra 2.
From playlist Logs Group Quiz

What are the properties of logarithms
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

When is a logarithm undefined? log4 (-32)
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Overview of log properties - Inverse properties
👉 Learn all about the properties of logarithms. The logarithm of a number say a to the base of another number say b is a number say n which when raised as a power of b gives a. (i.e. log [base b] (a) = n means that b^n = a). The logarithm of a negative number is not defined. (i.e. it is no
From playlist Rules of Logarithms

Some detail about cyclic groups and their application to cryptography, especially Diffie Hellman Key Exchange.
From playlist PubKey

Aurore Guillevic: Computing discrete logarithms in GF(pn): practical improvement of ...
Find this video and other talks given by worldwide mathematicians on CIRM's Audiovisual Mathematics Library: http://library.cirm-math.fr. And discover all its functionalities: - Chapter markers and keywords to watch the parts of your choice in the video - Videos enriched with abstracts, b
From playlist Women at CIRM

Solving the Logarithmic Equation log(A) = log(B) - C*log(x) for A
Solving the Logarithmic Equation log(A) = log(B) - C*log(x) for A Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys
From playlist Logarithmic Equations

Jan Maas : Gradient flows and Ricci cuevature in discrete and quantum probability
Recording during the thematic meeting : "Geometrical and Topological Structures of Information" the August 28, 2017 at the Centre International de Rencontres Mathématiques (Marseille, France) Filmmaker: Guillaume Hennenfent
From playlist Geometry

DLP Attacks and intro to El Gamal
We cover basic attacks on the discrete logarithm problem. The El Gamal Cipher is presented. We start discussion digital signatures.
From playlist PubKey

Eugenia Malinnikova : Uncertainty principles for discrete Schrödinger evolutions
Find this video and other talks given by worldwide mathematicians on CIRM's Audiovisual Mathematics Library: http://library.cirm-math.fr. And discover all its functionalities: - Chapter markers and keywords to watch the parts of your choice in the video - Videos enriched with abstracts, b
From playlist Analysis and its Applications

Bastien Vialla - Analyse du produit matrice creuse avec un ou plusieurs vecteur
Analyse du produit matrice creuse avec un ou plusieurs vecteur Licence: CC BY NC-ND 4.0
From playlist Journées Codage et Cryptographie 2014
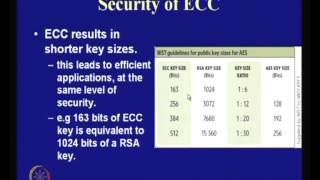
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Dominic Berry - Optimal scaling quantum linear systems solver via discrete adiabatic theorem
Recorded 25 January 2022. Dominic Berry of Macquarie University presents "Optimal scaling quantum linear systems solver via discrete adiabatic theorem" at IPAM's Quantum Numerical Linear Algebra Workshop. Abstract: Recently, several approaches to solving linear systems on a quantum compute
From playlist Quantum Numerical Linear Algebra - Jan. 24 - 27, 2022

Lecture 6: Gauge-equivariant Mesh CNN - Pim de Haan
Video recording of the First Italian School on Geometric Deep Learning held in Pescara in July 2022. Slide: https://www.sci.unich.it/geodeep2022/slides/2022-07-27%20Mesh%20-%20First%20Italian%20GDL%20School.pdf
From playlist First Italian School on Geometric Deep Learning - Pescara 2022

Logarithms - Basics | What are Logs? | Don't Memorise
What are Logarithms or logs? How are they related to Exponents? Watch this video to know the answers. To learn more about Logarithms, enroll in our full course now: https://infinitylearn.com/microcourses?utm_source=youtube&utm_medium=Soical&utm_campaign=DM&utm_content=4UNkQcBrLaQ&utm_ter
From playlist Logarithms

Charlotte Hardouin: Galois theory and walks in the quarter plane
Abstract: In the recent years, the nature of the generating series of walks in the quarter plane has attracted the attention of many authors in combinatorics and probability. The main questions are: are they algebraic, holonomic (solutions of linear differential equations) or at least hype
From playlist Combinatorics