
Symmetric Key Cryptography: The XOR Cipher
This is the fourth in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers the XOR logical operation, that is the exclusive OR operation, explaining how it can be used to encrypt and decrypt a sequence of binary digits. XOR is an im
From playlist Cryptography
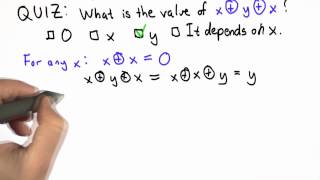
Xor Function Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Xor Function - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cbc Implementation Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Bitwise Operators 3: The XOR Operation
This computer science video describes the bitwise operation XOR. It explains how the XOR (eXclusive OR) operation works with unsigned integers and how the XOR operation can be used with a bitmask to manipulate the contents of a register containing bit flags. It also demonstrates how the
From playlist Bitwise Operators

Intercepting Messages Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Symmetric Key Cryptography: Cryptographic Techniques
This is the fifth in a series about cryptography; an extremely important aspect of computer science and cyber security. It reviews how the XOR logical operation can be used to encrypt at the bit level in symmetric key cryptography, then shows how this can be combined with permutation step
From playlist Cryptography

Symmetric Key Cryptography: The Keyword Cipher
This is the second in a series about cryptography; an extremely important aspect of computer science and cyber security. It covers a substitution cipher called the keyword cipher, also known as the Vigenère cipher. It explains how a keyword, or key phrase, can be used to effectively gene
From playlist Cryptography

From playlist Week 2 2015 Shorts

An informal introduction to cryptography. Part of a larger series teaching programming at http://codeschool.org
From playlist Cryptography

Yes, You Too Can Break Crypto: Exploiting Common Crypto Mistakes
Cryptography is tricky. Sure, everybody knows not to roll out their own crypto, but is it enough? Are the standard algorithms, libraries, and utilities always used the right way? This is of course a rhetorical question! Humans keep making mistakes that other humans can exploit, and Murphy’
From playlist Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Cryptography I Intro to Stream Ciphers
From playlist Crypto1

Cryptography I Intro to Stream Ciphers
From playlist Crypto1

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Guessing Keys Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Cryptograph: Substitution Cipher (Caesar Cipher)
This lesson explains how to encrypt and decrypt a message using a Caeser cipher. Site: http://mathispower4u.com
From playlist Cryptography