
The role of the hard drive buffer and interrupts when a file is transferred from primary memory (RAM) to a secondary storage device.
From playlist Computer Hardware and Architecture

In this video, you’ll learn more about the difference between hard and soft skills. Visit https://www.gcflearnfree.org/subjects/work/ for our text-based Work & Career tutorials. This video includes information on: • Hard skills, which include physical skills that are important to your job
From playlist Critical Skills For Today

Segmented, Paged and Virtual Memory
Memory management is one of the main functions of an operating system. This video is an overview of the paged and segmented memory management systems. It describes how a segmented memory management system employs segments of different sizes, which can result in fragmented free space and
From playlist Operating Systems

The Persistence of Memory pt 2! C tutorial 8
memory leaks, free, malloc, double free, null pointer
From playlist C Tutorial

Vintage 1962 "Digital Computer Techniques" - core memory, magnetic storage, etc.
Original un-edited 1962 film. A “somewhat dry” Army/Navy film of basic computer concepts. Detailed descriptions & diagrams of computing “input, store, control, arithmetic, output”, etc. Machine peripherals shown briefly. Film quality starts poor, but gets better towards the end. Nice d
From playlist Computers of the 1960's

Stanford Seminar - Rethinking Memory System Design for Data-Intensive Computing
"Rethinking Memory System Design for Data-Intensive Computing"- Onur Mutlu of Carnegie Mellon University About the talk: The memory system is a fundamental performance and energy bottleneck in almost all computing systems. Recent system design, application, and technology trends that requ
From playlist Engineering
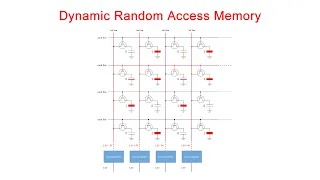
Dynamic Random Access Memory (DRAM). Part 1: Memory Cell Arrays
This is the first in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This particular video covers the structure and workings of the DRAM memory cell. That is, the basic unit of st
From playlist Random Access Memory

Computer Basics: What Is a Computer?
Computers are all around us, and they play an important role in our lives. But what exactly is a computer? We're going to answer that question and give you an overview of some of the different types of computers you might use. 0:00 Intro 0:22 Ones and zeros 0:39 Hardware and software 1:0
From playlist Starting out with Technology

How to Focus - Learn How You Can Focus Without Getting Distracted
https://memorycourse.brainathlete.com/memorytips/?WickedSource=Youtube&WickedID=How-To-Focus Get memory training tips at link above now Being focused is a skill. In this day and age, we have all kinds of distraction, from cell phones to video games and easy access to anything and everythi
From playlist Brain Training

Week 5: Wednesday - CS50 2011 - Harvard University
CS50 Library. Heap. Pointers, continued. Forensics.
From playlist CS50 Lectures 2011

Why Code with Code Smells is Harder to Understand
Check out Felienne Hermans' book 📖 The Programmer's Brain | http://mng.bz/N86v 📖 To save 40% off this book ⭐ DISCOUNT CODE: twitherm40 ⭐ Felienne reveals how knowledge of cognitive science can deepen our understanding of code smells to help us write better code and make its reading easier!
From playlist Software Development

Neuropsychological Deficits in BPD and Implications for Treatment
Neuropsychological Deficits: BPD is associated with a range of cognitive deficits, with no two individuals necessarily showing the same types of difficulties. The most frequently affected neuropsychological domains include memory, response inhibition and planning. These deficits a
From playlist Yale NEA-BPD Conference: Manage Related Cognitive Challenges

Week 7: Monday - CS50 2009 - Harvard University
Valgrind. Bitwise operators. Hash tables. Trees. Binary search trees. Tries. Huffman coding.
From playlist CS50 Lectures 2009

From playlist CS50 Lectures 2012

Operating system for beginners || Operating system basics
An operating system (OS) is system software that manages computer hardware, software resources, and provides common services for computer programs. Time-sharing #operating_systems schedule tasks for efficient use of the system and may also include accounting software for cost allocation o
From playlist Operating System

Everything You Need to Know About Deep Deterministic Policy Gradients (DDPG) | Tensorflow 2 Tutorial
Deep Deterministic Policy Gradients (DDPG) is an actor critic algorithm designed for use in environments with continuous action spaces. This makes it great for fields like robotics, that rely on applying continuous voltages to electric motors. You'll get a crash course with a quick lecture
From playlist Deep Reinforcement Learning Tutorials - All Videos

Essential concepts of operating systems. Part of a larger series teaching programming. Visit http://codeschool.org
From playlist Operating System Basics

Loss Functions : Data Science Basics
What are loss functions in the context of machine learning?
From playlist Data Science Basics

Week 5: Wednesday - CS50 2010 - Harvard University
CS50 Library. Stack and heap, continued. Pointers, continued. File I/O. Forensics. Linked lists.
From playlist CS50 Lectures 2010
