
The role of the hard drive buffer and interrupts when a file is transferred from primary memory (RAM) to a secondary storage device.
From playlist Computer Hardware and Architecture

Segmented, Paged and Virtual Memory
Memory management is one of the main functions of an operating system. This video is an overview of the paged and segmented memory management systems. It describes how a segmented memory management system employs segments of different sizes, which can result in fragmented free space and
From playlist Operating Systems

What are bounded functions and how do you determine the boundness
👉 Learn about the characteristics of a function. Given a function, we can determine the characteristics of the function's graph. We can determine the end behavior of the graph of the function (rises or falls left and rises or falls right). We can determine the number of zeros of the functi
From playlist Characteristics of Functions

Functions of equations - IS IT A FUNCTION
👉 Learn how to determine whether relations such as equations, graphs, ordered pairs, mapping and tables represent a function. A function is defined as a rule which assigns an input to a unique output. Hence, one major requirement of a function is that the function yields one and only one r
From playlist What is the Domain and Range of the Function
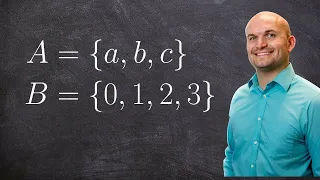
How to determine if an ordered pair is a function or not
👉 Learn how to determine whether relations such as equations, graphs, ordered pairs, mapping and tables represent a function. A function is defined as a rule which assigns an input to a unique output. Hence, one major requirement of a function is that the function yields one and only one r
From playlist What is the Domain and Range of the Function

Determine if the equation represents a function
👉 Learn how to determine whether relations such as equations, graphs, ordered pairs, mapping and tables represent a function. A function is defined as a rule which assigns an input to a unique output. Hence, one major requirement of a function is that the function yields one and only one r
From playlist What is the Domain and Range of the Function
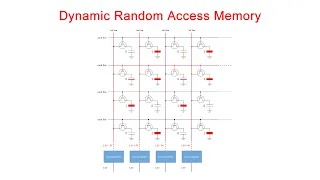
Dynamic Random Access Memory (DRAM). Part 1: Memory Cell Arrays
This is the first in a series of computer science videos is about the fundamental principles of Dynamic Random Access Memory, DRAM, and the essential concepts of DRAM operation. This particular video covers the structure and workings of the DRAM memory cell. That is, the basic unit of st
From playlist Random Access Memory

Fetch Decode Execute Cycle in more detail
This computer science video illustrates the fetch decode execute cycle. The view of the CPU focusses on the role of various registers including the accumulator, memory address register, memory data register, current instruction register and the program counter. The arithmetic and logic un
From playlist Computer Hardware and Architecture

The information cost of quantum memoryless protocols - M. Lauriere - Main Conference - CEB T3 2017
Mathieu Lauriere (NYU Shanghai) / 12.12.2017 Title: The information cost of quantum memoryless protocols Abstract: In this talk, we will consider memoryless quantum communication protocols, where the two parties do not possess any memory besides their classical input and they take turns
From playlist 2017 - T3 - Analysis in Quantum Information Theory - CEB Trimester

12. Parallel Storage Allocation
MIT 6.172 Performance Engineering of Software Systems, Fall 2018 Instructor: Julian Shun View the complete course: https://ocw.mit.edu/6-172F18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP63VIBQVWguXxZZi0566y7Wf Prof. Shun discusses the differences between malloc()
From playlist MIT 6.172 Performance Engineering of Software Systems, Fall 2018

For more information and to download the video visit: http://bit.ly/30C3_info Playlist 30C3: http://bit.ly/30c3_pl Speaker: Andreas Bogk Violation of memory safety is still a major source of vulnerabilities in everyday systems. This talk presents the state of the art in compiler instrume
From playlist 30C3

3. Buffer Overflow Exploits and Defenses
MIT 6.858 Computer Systems Security, Fall 2014 View the complete course: http://ocw.mit.edu/6-858F14 Instructor: James Mickens In this lecture, Professor Mickens discusses topics related to buffer overflow exploits, including baggy bounds handling, mitigation approaches, and return-orient
From playlist MIT 6.858 Computer Systems Security, Fall 2014

Everything You Need to Know About Deep Deterministic Policy Gradients (DDPG) | Tensorflow 2 Tutorial
Deep Deterministic Policy Gradients (DDPG) is an actor critic algorithm designed for use in environments with continuous action spaces. This makes it great for fields like robotics, that rely on applying continuous voltages to electric motors. You'll get a crash course with a quick lecture
From playlist Deep Reinforcement Learning Tutorials - All Videos

Online Learning in Reactive Environments - Raman Arora
Seminar on Theoretical Machine Learning Topic: Online Learning in Reactive Environments Speaker: Raman Arora Affiliation: Johns Hopkins University; Member, School of Mathematics Date: December 18, 2019 For more video please visit http://video.ias.edu
From playlist Mathematics

27c3: I Control Your Code (en)
Speaker: Mathias Payer Attack Vectors Through the Eyes of Software-based Fault Isolation Unsafe languages and an arms race for new bugs calls for an additional line of defense in software systems. User-space virtualization uses dynamic instrumentation to detect different attack vectors a
From playlist 27C3: We come in peace

Vlog #004: C++/Python methods in memory
If you instantiate an object of a class, is the method bytecode copied to the object as well? If not, then how do virtual methods work?
From playlist Gynvael's Vlog

What is a Function? Calculus for Beginners: Dr Chris Tisdell Live Stream
What is a function and how are they useful? This video will answer these questions from an elementary mathematics point of view. Functions are a bit like a machine that follows a processing rule. You input something (like a number), the machine processes the number according to the rule,
From playlist Calculus for Beginners

Borrowing memory that's being used: catalytic approaches to the Tree Evaluation Problem - James Cook
Computer Science/Discrete Mathematics Seminar I Topic: Borrowing memory that's being used: catalytic approaches to the Tree Evaluation Problem Speaker: James Cook Affiliation: University of Toronto Date: April 6, 2020 For more video please visit http://video.ias.edu
From playlist Mathematics

