Proof: Convergent Sequence is Bounded | Real Analysis
Any convergent sequence must be bounded. We'll prove this basic result about convergent sequences in today's lesson. We use the definition of the limit of a sequence, a useful equivalence involving absolute value inequalities, and then considering a maximum and minimum will help us find an
From playlist Real Analysis
Convergent sequences are bounded
Convergent Sequences are Bounded In this video, I show that if a sequence is convergent, then it must be bounded, that is some part of it doesn't go to infinity. This is an important result that is used over and over again in analysis. Enjoy! Other examples of limits can be seen in the
From playlist Sequences

The Sum of Convergent Sequences Converges Proof
The Sum of Convergent Sequences Converges Proof If you enjoyed this video please consider liking, sharing, and subscribing. You can also help support my channel by becoming a member https://www.youtube.com/channel/UCr7lmzIk63PZnBw3bezl-Mg/join Thank you:)
From playlist Advanced Calculus

Divergence of series -- Calculus II
This lecture is on Calculus II. It follows Part II of the book Calculus Illustrated by Peter Saveliev. The text of the book can be found at http://calculus123.com.
From playlist Calculus II
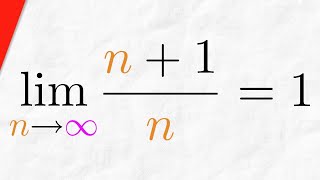
Proof: Sequence (n+1)/n Converges to 1 | Real Analysis
We will prove the sequence (n+1)/n converges to 1. In other words, we're proving that the limit of (n+1)/n as n approaches infinity is 1. We use the epsilon definition of a convergent sequence and the proof is straightforward, following the typical form of a convergent sequence proof. Re
From playlist Real Analysis

Absolute Convergence, Conditional Convergence, and Divergence
This calculus video tutorial provides a basic introduction into absolute convergence, conditional convergence, and divergence. If the absolute value of the series convergences, then the original series will converge based on the absolute convergence test. If the absolute value of the ser
From playlist New Calculus Video Playlist

How does cryptography ACTUALLY work?
In this video I'll attempt to introduce you to some of the maths behind modern cryptography, which is in a sense how the world around us works now. Surprisingly, it has a lot to do with the simple ideas of division and remainders. We'll cover modular arithmetic basics, continued fractions
From playlist Summer of Math Exposition Youtube Videos

FUT1433 SUSE Enterprise Storage Roadmap
This future session was delivered at SUSECON in April 2019, in Nashville, TN. Abstract: This session will provide a roadmap review for SUSE Enterprise Storage which is based on the opensource Ceph project. Particular detail will be given to SUSE Enterprise Storage 6 based on Ceph Nautilus
From playlist SUSECON 2019

Cryptography - Seminar 1 - Foundations
This seminar series is about the mathematical foundations of cryptography. In the first seminar Eleanor McMurtry introduces cryptography and explains some of the problems that need to be solved in order to develop proper foundations. The webpage for this seminar is https://lnor.net/uc-sem
From playlist Metauni

Univers Convergents 2019 - Séance 6/6 - Assassination Nation
Assassination Nation de Sam Levinson (USA - 2018 - 1h48) Séance du 25 juin 2019 Un débat en présence de : Francis Bach, Chercheur en mathématiques et informatique, INRIA Matthieu Bouthors, Président de l’association HZV (Hackerzvoice) et de la Nuit des Hackeurs Résumé : Lily et ses tro
From playlist Ciné-Club Univers Convergents

Proof: Absolute Value Theorem for Sequences | Real Analysis
We prove if the absolute value of a sequence converges to 0 then the original sequence does as well. So if (|a_n|) converges to 0 then (|a_n|) does as well. We go through two proofs of this, one using the definition of a convergent sequence and the other using the squeeze theorem. #RealAna
From playlist Real Analysis

28C3: Cellular protocol stacks for Internet (en)
For more information visit: http://bit.ly/28C3_information To download the video visit: http://bit.ly/28C3_videos Playlist 28C3: http://bit.ly/28C3_playlist Speaker: Harald Welte Almost everyone uses the packet oriented transmission modes of cellular networks. However, unlike TCP/I
From playlist 28C3: Behind Enemy Lines
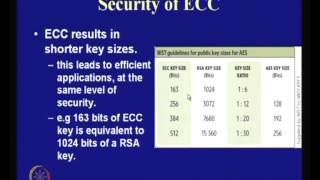
Application of Elliptic Curves to Cryptography
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

SOURCE Boston 2008: Understanding Emerging Threats: The case of Nugache
Speakers: Bruce Dang - Microsoft Dave Dittrich - University of Washington Distributed intruder attack tools have evolved from the original "handler/agent" DDoS tools of 1998, to very large and powerful botnets in the early 2000's. Methods of command and control (C2) have also evolved, fr
From playlist SOURCE Boston 2008

Unusual Properties: Divergent Rearrangements/ Divergent Integral with Convergent Sum
This video is about series with divergent rearrangements, and a function with a divergent integral.
From playlist Basics: Unusual Properties in Math

Privacy-Preserving Machine Learning with Fully Homomorphic Encryption
A Google TechTalk, presented by Jordan Fréry, 2023-01-17 ABSTRACT: In today's digital age, protecting privacy has become increasingly difficult. However, new developments such as Fully Homomorphic Encryption (FHE) provide a means of safeguarding sensitive client information. We are excite
From playlist Differential Privacy for ML

The Science of Forced Perspective at Disney Parks
Go to https://NordVPN.com/ArtofEngineering and use code ARTOFENGINEERING to get 68% off a 2-year plan plus 1 additional month for free. It’s risk-free with Nord’s 30-day money-back guarantee! A comprehensive guide to forced perspective techniques at the Disney theme parks. Support Art of
From playlist Theme Park Engineering

Probability and Information Theory
Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Proof: Sequence 1/n Converges to 0 | Real Analysis Exercises
We will prove the sequence 1/n converges to 0. In other words, we're proving that the limit of 1/n as n approaches infinity is 0. We use the epsilon definition of a convergent sequence and the proof is straightforward, following the typical form of a convergent sequence proof and using the
From playlist Real Analysis Exercises