
balanced vane pump inventor animation
http://www.mekanizmalar.com/menu-pump.html
From playlist Pumps
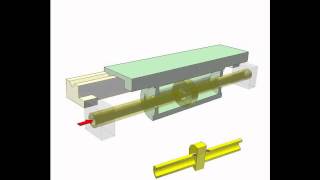
Hydraulic cylinder with fixed piston
Green cylinder with machine table reciprocates. Pressure fluid is conducted into cylinder via holes on fixed piston rod. The hoses can be stationary. In case using holes on the cylinder the hoses have to move with the cylinder. The arrows show flows of pressure fluid.
From playlist Mechanisms
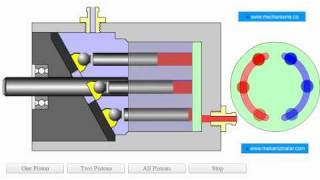
Fixed Swashplate Rotating Barrel
http://www.mekanizmalar.com/fixed_swashplate_rotating_barrel.html An axial piston pump has a number of pistons (usually an odd number) arranged in a circular array within a housing which is commonly referred to as a cylinder block, rotor or barrel. This cylinder block is driven to rotate
From playlist Pneumatic and Hydraulics

IDEspinner Buffer Overflows pt1
This movie tries to show how you can create a bufferoverflow Credits go out to IDEspinner
From playlist Buffer overflow

http://www.mekanizmalar.com/menu_pneumatic.html This video shows working principle of pressure compensated hydraulic piston pump. Notice how angle of swash plate changes when slider move above 80 bar. Also notice the pressure gauge.
From playlist Pumps
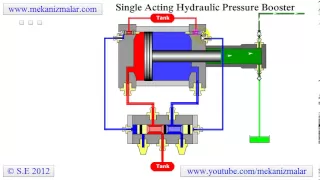
Pressure Booster Single Acting
Hydraulic pressure booster ( or intensifier ) converts normal shop-line air pressure to high-pressure hydraulic power. This is most economical way of obtaining high pressure oil if pressurized air available.
From playlist Pneumatic and Hydraulics

Animation - How an axial flow variable displacement piston pump works.
Hi Guys, Hydraulic pumps are of various types, axial flow variable displacement piston pump are used in heavy hydraulic construction equipments. Tracked excavator machines commonly use this type of pumps. The advantage of this pump is that, the flow is variable compared to gears pumps in
From playlist engineering explained

variable displacement piston pump
http://www.mekanizmalar.com/variable_displacement_piston_pump.html
From playlist Pumps

Systems of Differential Equations with Forcing: Example in Control Theory
This video explores linear systems of differential equations with forcing. We motivate these problems with a simple control example where we stabilize and inverted pendulum with external forcing based on state feedback. Playlist: https://www.youtube.com/playlist?list=PLMrJAkhIeNNTYaO
From playlist Engineering Math: Differential Equations and Dynamical Systems

CERIAS Security: Perturbation of Multivariable Public-key Cryptosystems 2/5
Clip 2/5 Speaker: Jintai Ding · University of Cincinnati Public key cryptography is an indispensable part of most modern communication systems. However, quantum computers can break cryptosystems like RSA, which are based on For more information go to the Cerias website (http://bit
From playlist The CERIAS Security Seminars 2005 (2)

Removing Rust with Vinegar and Salt
I'm cleaning up a vice I got from my grandpa to put on my newly finished bench. I read an article (http://www.finewoodworking.com/2014/06/05/salt-and-vinegar-natures-rust-remover) about using salt and vinegar to remove rust, so I thought I'd give it a try. SOME TOOLS I USE Buying through
From playlist Lawn mower

Virtual Open House Live Session: Kitchen Chemistry
Learn about emulsions, gelification and spherification as you make your own salad dressing and mayo with MagLab chemist Dr. Martha Chacon Recorded on Zoom: 3/2/21 at 6:30pm
From playlist Virtual Open House: Live Demos

LSOP Live: Kitchen Chemistry, September 4, 2020
Join the LSOP crew for some science fun in the kitchen! Color-changing tea, making cheese in 1 minute, making ink disappear, and, for our grand finale, a rather frothy microwave surprise.
From playlist LSOP Live

Rust Removal Vinegar #304 tubalcain - compare to electrolysis
In this video, I remove rust on tools with a mild acid--VINEGAR. Search youtube for my other rust removal videos-- "electrolysis vinegar tubalcain". THANKS FOR WATCHING! SUBSCRIBE if you enjoy the content! I have tubalcain tee shirts available. Visit STOREFRONTIER and search tubalcain!
From playlist #4 MACHINE SHOP TIPS tubalcain playlist #301 thru #400

Balsamic Rosemary Pork Tenderloin Recipe - by Laura Vitale - Laura in the Kitchen Episode 116
To get this complete recipe with instructions and measurements, check out my website: http://www.LauraintheKitchen.com Official Facebook Page: http://www.facebook.com/LauraintheKitchen Twitter: @Lauraskitchen
From playlist Laura in the Kitchen: Main Course Italian Recipes | CosmoLearning Culinary

Candy Cane Science Experiment (Chemistry)
Try this simple science experiment for kids using candy canes submerged in different liquids - water, oil, and vinegar. ▶️ Get supplies to do candy cane science yourself: https://www.beardedscienceguy.com/how-to-do-candy-cane-science ▶️ How to do candy cane science: Step 1: Place a cand
From playlist 15 Science Experiments for Kids 2016

Food Additives Explained | Bang Goes The Theory | Earth Lab
Liz Bonnin demonstrates the use of additives in our food with the addition of E415 to see how it can stabilise a mixture amongst ingredients. Subscribe for more awesome science - http://www.youtube.com/subscription_center?add_user=HeadsqueezeTV http://www.youtube.com/user/HeadsqueezeTV
From playlist Bang Goes The Theory

Carbonated Grape Salad with Goat Cheese
Recipe at: http://ciaprochef.com/grapes/recipe16/ What else can you do with a fresh table grape besides eat it? Chefs active in the realm of molecular gastronomy are manipulating ingredients in ways never imagined. Chef Scott Samuel of the Culinary Institute of America was asked to develo
From playlist Culinary Institute of America: Cooking Demonstrations | CosmoLearning.org Culinary
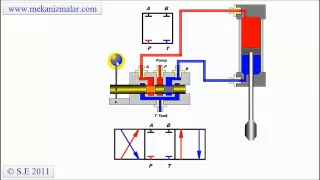
http://www.mekanizmalar.com This is a flash animation of a hydraulic closed center valve.
From playlist Pneumatic and Hydraulics

Phase separation in the Cahn-Hilliard equation
This is a simulation of the Cahn-Hilliard equation on a rectangular domain with periodic boundary conditions, starting from a random initial state. Like the Allen-Cahn equation, the Cahn-Hilliard equation models phase separation in various alloys or other mixtures of two different substanc
From playlist Reaction-diffusion equations