
Passive Recon - Subdomain Enumeration With Sublist3r
In this video, I demonstrate how to set up and utilize Sublist3r for subdomain enumeration. Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps penetration testers and bug hunters collect and gather subdomains for the domain they are targeting. Sub
From playlist Bug Bounty Hunting

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 08 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 02 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 07 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 12 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 06 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 18 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 10 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

Cryptography and Network Security by Prof. D. Mukhopadhyay, Department of Computer Science and Engineering, IIT Kharagpur. For more details on NPTEL visit http://nptel.iitm.ac.in
From playlist Computer - Cryptography and Network Security

Vic Reiner, Lecture I - 9 February 2015
Vic Reiner (University of Minnesota) - Lecture I http://www.crm.sns.it/course/4036/ Many results in the combinatorics and invariant theory of reflection groups have q-analogues for the finite general linear groups GLn(Fq). These lectures will discuss several examples, and open questions a
From playlist Algebraic topology, geometric and combinatorial group theory - 2015

jQuery Tutorial #4 - DOM Traversal with jQuery
Lots of jobs require you to be good at DOM traversal. This jQuery tutorial focuses on using jQuery as a DOM traversal library - which is where jQuery really shines. The DOM (Document Object Model) is all of the html elements that get generated when your browser reads the html file. DOM
From playlist Javascript Tutorial For Beginners

Recent Progress on Zimmer's Conjecture - David Fisher
Members' Seminar Topic: Recent Progress on Zimmer's Conjecture Speaker: David Fisher Affiliation: Indiana University, Bloomington; Member, School of Mathematics Date: December 3, 2018 For more video please visit http://video.ias.edu
From playlist Mathematics

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 16 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration
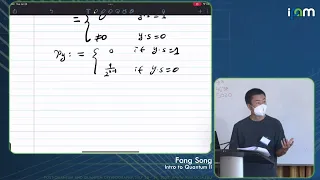
Fang Song - Introduction to quantum computing Part 2 of 3 - IPAM at UCLA
Recorded 26 July 2022. Fang Song of Portland State University presents "Introduction to quantum computing II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This lecture will focus on two major (families of) quantum algorithms: period finding (a.k.a. Hidd
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Does Reality TV Affect Our View On Surveillance? | Idea Channel | PBS Digital Studios
Viewers like you help make PBS (Thank you 😃) . Support your local PBS Member Station here: https://to.pbs.org/donateidea What have you been watching lately? There's a good chance (whether you admit to it or not) that you've been watching some reality TV. The "Reality TV" genre is mega pop
From playlist Newest Episodes

Bound on the number of rational points on curves Mazur conjectured, after Faltings's proof of the Mordell conjecture, that the number of rational points on a curve depends only on the genus, the degree of the number field and the Mordell-Weil rank. This conjecture was established in a few
From playlist DART X

Xavior Spade's Channel: https://www.youtube.com/channel/UC5Aaysw0-njB9xH8uvNFvvg LEARN THE VOODOO CARD TRICK HERE: https://sellfy.com/p/OiqQ/ YO! So glad to be bringing the Elmsley Count to my channel and I couldn't have asked for a better teacher. This tutorial for the elmsley count
From playlist Tutorials

Ethical Hacking Tutorial | Comprehensive Subdomain Enumeration | Session 05 | #cybersecurity
Don’t forget to subscribe! This ethical hacking tutorial series is about comprehensive subdomain enumeration. Through this tutorial series, I will be demonstrating how to install, configure and use different tools for subdomain enumeration. We will try to go through the following subdom
From playlist Comprehensive Subdomain Enumeration

