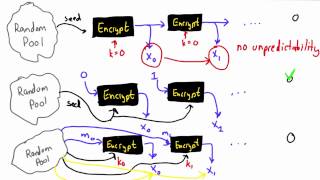
Pseudo Random Number Generator Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

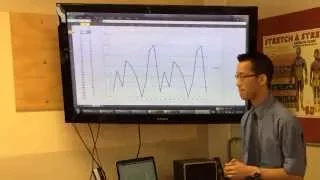
Pseudo Random Number Generator - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Random Oracle - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Randomness Quiz - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Randomness - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Randomness Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Random Password Generator Using Python | How To Create Password Generator | #Shorts | Simplilearn
🔥Explore Our Free Programming Courses With Completion Certificate by SkillUp: https://www.simplilearn.com/skillup-free-online-courses?utm_campaign=RandomPasswordGeneratorShorts&utm_medium=ShortsDescription&utm_source=youtube Random Password Generator is a python program generated by a mix
From playlist #Shorts | #Simplilearn

23C3: Analysis of a strong Random Number Generator
Speaker: Thomas Biege This paper (and slides) will descibe the inner workings of the the random number generator (/dev/{u}random) of Linux. Additionally some possible security flaws are shown (entropy overestimation, zero'izing the pool, etc.) For more information visit: http://bit.ly/
From playlist 23C3: Who can you trust

CCoE Webinar Series: Stronger Security for Password Authentication
Originally recorded August 28th, 2017 Passwords are an infamous bottleneck of information security: The users choose them badly and then forget them, and the servers store (at best!) a table of password hashes which, in the all-too-common event that the server is hacked, allows the attack
From playlist Center for Applied Cybersecurity Research (CACR)

Shell Scripting - Password Generator
Hey guys! HackerSploit here back again with another video, in this series we will be looking at how to create shell scripts. A shell script is a computer program designed to be run by the Unix shell, a command-line interpreter. The various dialects of shell scripts are considered to be scr
From playlist Shell Scripting

OWASP AppSecUSA 2011:How NOT to Implement Cryptography for the OWASP Top 10 (Reloaded)
Speaker: Anthony J. Stieber This talk is an update of a talk in 2008 at the OWASP Minneapolis-St.Paul Chapter which was about encryption as it applies to parts of the OWASP Top Ten. The new talk uses fresh examples of application cryptography successes and failures, and also incorporates
From playlist OWASP AppSecUSA 2011

CERIAS Security: Towards Secure and Re-usable Multiple Password Mnemonics 5/7
Clip 5/7 Speaker: Umut Topkara · Purdue University This talk will focus on human aspects of authentication mechanisms. I will present two methods that we have developed to reinforce the security of existing systems by improving their usability. Previous studies have repeatedly show
From playlist The CERIAS Security Seminars 2007

Crypto Security: Passwords and Authentication - Livestream aantonop
Looking for an entertaining, trustworthy, unbiased opinion on crypto security? This is it. In this upcoming bonus Livestream, aantonop answers your questions about passwords and authentication, two basic but incredibly important and misunderstood topics. Whether you’re new or an expert, yo
From playlist English Subtitles - aantonop Videos with subtitles in English

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

Cryptography is a complex and confusing subject. In this talk you will learn about the core components of cryptography used in software development: securing data with encryption, ensuring data integrity with hashes and digital signatures, and protecting passwords with key derivation funct
From playlist Blockchain

Live CEOing Ep 664: Language Design in Wolfram Language [Design of Symbols]
In this episode of Live CEOing, Stephen Wolfram discusses upcoming improvements and features to the Wolfram Language. If you'd like to contribute to the discussion in future episodes, you can participate through this YouTube channel or through the official Twitch channel of Stephen Wolfram
From playlist Behind the Scenes in Real-Life Software Design

Ethical Hacking - Basics Of Ethical Hacking | Session 04 | #crybersecurity
Don’t forget to subscribe! This project will cover the basics to start ethical hacking and learn the tools and techniques of the industry. This project should teach someone how with limited or no hacking experience and teach them the basics to get started in the cyber security industry.
From playlist Basics Of Ethical Hacking

CERIAS Security: Towards Secure and Re-usable Multiple Password Mnemonics 4/7
Clip 4/7 Speaker: Umut Topkara · Purdue University This talk will focus on human aspects of authentication mechanisms. I will present two methods that we have developed to reinforce the security of existing systems by improving their usability. Previous studies have repeatedly show
From playlist The CERIAS Security Seminars 2007

Discrete Structures: Random number generators, checksums, hashing
Learn about random number generators, checksums, and hashing. We'll start with the von Neumann random number generator and the contemporary linear congruential generator. Then we'll go over the Luhn algorithm used for credit card number validation and then introduce hash functions such as
From playlist Discrete Structures, Spring 2022