
Radix Sort In C | Radix Sort Algorithm Explained | C Language Tutorial For Beginners | Simplilearn
This video is based on Radix Sort In C. The Radix Sort Algorithm Explained in C Tutorial will briefly help beginners with a theoretical explanation of the program's working and implementation of the Radix Sort Algorithm. The C Language Tutorial For Beginners will cover the following topics
From playlist C++ Tutorial Videos

Radix Sort Algorithm | Radix Sort In Data Structure | Sorting Algorithms Explained | Simplilearn
This video is based on radix sort Algorithm. This radix sort in data structures tutorial make sure that sorting algorithms explained well to help beginners learn radix sort. The video also covers practical demo for a better learning experience. This video will cover the following concept
From playlist Data Structures & Algorithms

Verifying an identity by multiplying
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

CERIAS Security: Recent Attacks on MD5 2/6
Clip 2/6 Speaker: John Black · University of Colorado at Boulder Cryptology is typically defined as cryptography (the construction of cryptographic algorithms) and cryptanalysis (attacks on these algorithms). Both are important, but the latter is more fun. Cryptographic hash functions
From playlist The CERIAS Security Seminars 2006
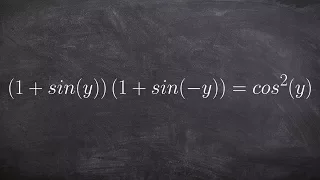
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities
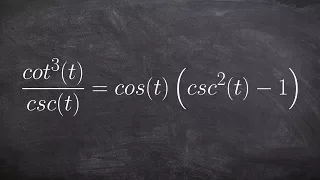
Verifying a trigonometric Identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

34b: Numerical Algorithms I - Richard Buckland UNSW
Introduction to numerical algorithms Lecture 34 comp1927 "computing2"
From playlist CS2: Data Structures and Algorithms - Richard Buckland

Tutorial for verifying trigonometric identities
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

MIT 6.006 Introduction to Algorithms, Fall 2011 View the complete course: http://ocw.mit.edu/6-006F11 Instructor: Victor Costan License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.006 Introduction to Algorithms, Fall 2011
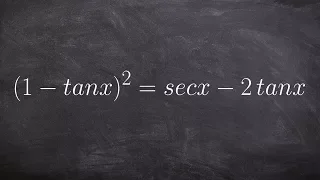
How to verify a trigonometric identity by expanding one side
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Conformal Field Theory Study of Topological State of Matter by Sujit Sarkar
DISCUSSION MEETING INDIAN STATISTICAL PHYSICS COMMUNITY MEETING ORGANIZERS Ranjini Bandyopadhyay, Abhishek Dhar, Kavita Jain, Rahul Pandit, Sanjib Sabhapandit, Samriddhi Sankar Ray and Prerna Sharma DATE: 14 February 2019 to 16 February 2019 VENUE: Ramanujan Lecture Hall, ICTS Bangalo
From playlist Indian Statistical Physics Community Meeting 2019

Verifying an identify by expanding an expression
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

"Fortunately, Unfortunately": How to Tell Whether a Number Is Prime #MegaFavNumbers
How can we tell whether or not a large integer is prime? Well, there's some bad news and some good news (and more bad news, and more good news, and...) My contribution to #MegaFavNumbers (and my first go at YouTube, so, you know, go easy on me). Matt Parker's video, which got me thinking
From playlist MegaFavNumbers

Faster Primality Test - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Multiply and verify the trigonometric identity
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities

Lecture 9: Table Doubling, Karp-Rabin
MIT 6.006 Introduction to Algorithms, Fall 2011 View the complete course: http://ocw.mit.edu/6-006F11 Instructor: Erik Demaine License: Creative Commons BY-NC-SA More information at http://ocw.mit.edu/terms More courses at http://ocw.mit.edu
From playlist MIT 6.006 Introduction to Algorithms, Fall 2011

10. Markov and Hidden Markov Models of Genomic and Protein Features
MIT 7.91J Foundations of Computational and Systems Biology, Spring 2014 View the complete course: http://ocw.mit.edu/7-91JS14 Instructor: Christopher Burge Prof. Christopher Burge begins by reviewing Lecture 9, then begins his lecture on hidden Markov models (HMM) of genomic and protein f
From playlist MIT 7.91J Foundations of Computational and Systems Biology

What is the Public Key Encryption?
A 1976, two Stanford researchers devised an encryption method that revolutionized cryptography by making it easier to send encrypted information without having to agree on a key beforehand. With the help of a short animation, cryptographer Tal Rabin explains how these "public" keys work.
From playlist Technology
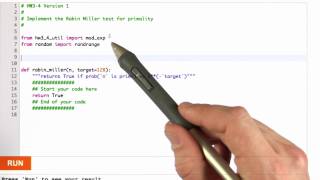
Rabin Miller Primality Test - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Learn how to verify an identify by distributive property
👉 Learn how to verify trigonometric identities by expanding the trigonometric expressions. When the given trigonometric expressions involve multiplications with more than one term in parenthesis, we start by expanding the expressions using the distributive property. After we have expande
From playlist Verify Trigonometric Identities