
In this video I briefly go over the advantage to the Schnorr signature, and how to sign and verify.
From playlist Cryptography and Coding Theory

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

Fundamental concepts of Digital Signatures are discussed. ElGamal and Schnorr Digital Signature schemes are analyzed. Digital signature standard is presented.
From playlist Network Security

RSA Signature - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

Digital Signatures: RSA and El Gamal
We describe the theory and applications of digital signatures, and provide two examples of digital signature algorithms: RSA and El Gamal
From playlist PubKey

Theory and Practice of Cryptography
Google Tech Talks December, 12 2007 ABSTRACT Topics include: Introduction to Modern Cryptography, Using Cryptography in Practice, Proofs of Security and Security Definitions and A Special Topic in Cryptography Speaker: Steve Weis Steve Weis received his PhD from the Cryptography and In
From playlist Cryptography, Security

Using the property of exponents to multiply expressions
👉 Learn how to simplify expressions using the power rule of exponents. When several terms of an expression is raised to an exponent outside the parenthesis, the exponent is distributed over the individual terms in the expression and the exponent outside the parenthesis is multiplied to eac
From playlist Simplify Using the Rules of Exponents

Jonathan Katz - Introduction to Cryptography Part 2 of 3 - IPAM at UCLA
Recorded 25 July 2022. Jonathan Katz of the University of Maryland presents "Introduction to Cryptography II" at IPAM's Graduate Summer School Post-quantum and Quantum Cryptography. Abstract: This session will focus on public-key cryptography, including key exchange, public-key encryption,
From playlist 2022 Graduate Summer School on Post-quantum and Quantum Cryptography

Signature Methods for Time Series Data || Sam Morley
Signatures are a mathematical tool that arise in the study of paths. Roughly speaking, they capture the fine structure of a path. It turns out that signatures are extremely useful for analysing time series data in a data science context. This is party because they can take irregularly samp
From playlist Python

Simplify an expression using power to product and power to quotient rule
👉 Learn how to simplify expressions using the power rule of exponents. When several terms of an expression is raised to an exponent outside the parenthesis, the exponent is distributed over the individual terms in the expression and the exponent outside the parenthesis is multiplied to eac
From playlist Simplify Using the Rules of Exponents

Some Cryptographic Tools (in Blockchains) by Manoj Prabhakaran
DISCUSSION MEETING : FOUNDATIONAL ASPECTS OF BLOCKCHAIN TECHNOLOGY ORGANIZERS : Pandu Rangan Chandrasekaran DATE : 15 to 17 January 2020 VENUE : Madhava Lecture Hall, ICTS, Bangalore Blockchain technology is among one of the most influential disruptive technologies of the current decade.
From playlist Foundational Aspects of Blockchain Technology 2020

1. Signatures, Hashing, Hash Chains, e-cash, and Motivation
MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018 Instructor: Neha Narula, Tadge Dryja View the complete course: https://ocw.mit.edu/MAS-S62S18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP61KHzhg3JIJdK08JLSlcLId Introduces currency, banking, and electro
From playlist MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018
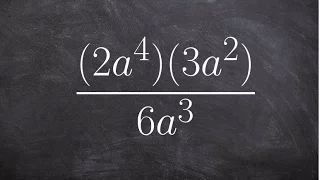
Learn the basics for simplifying an expression using the rules of exponents
👉 Learn how to simplify expressions using the quotient rule of exponents. The quotient rule of exponents states that the quotient of powers with a common base is equivalent to the power with the common base and an exponent which is the difference of the exponents of the term in the numerat
From playlist Simplify Using the Rules of Exponents | Quotient Rule

Test models for filtering and prediction of moisture-coupled tropical waves - John Harlim
Test models for filtering and prediction of moisture-coupled tropical waves John Harlim, NCSU, Raleigh, USA. DISCUSSION MEETING: MATHEMATICAL PERSPECTIVES ON CLOUDS, CLIMATE, AND TROPICAL METEOROLOGY 25 JANUARY, 2013
From playlist Mathematical Perspectives on Clouds, Climate, and Tropical Meteorology

CERIAS Security: Privacy Policy-driven Access Control with Mixed Credentials 5/5
Clip 5/5 Speaker: Shouhuai Xu · University of Texas at San Antonio Access control in decentralized systems is an important problem that has not been fully understood, except perhaps that it should be based on credentials. There are mainly two research approaches towards this goal: one
From playlist The CERIAS Security Seminars 2005 (2)

Stanford Seminar: Building Systems Using Malicious Components
EE380: Colloquium on Computer Systems Building Systems Using Malicious Components: How I learned to Stop Worrying and Trust SNARK Proofs Speaker: Eran Tromer, Tel Aviv University and Columbia University "Computers are unreliable and vulnerable to attacks. Therefore, we shouldn't belie
From playlist Stanford EE380-Colloquium on Computer Systems - Seminar Series

testing/quick: Go's little-known blackbox test harness (Go from A to Z — Zürich Gophers Meetup)
Google Tech Talk October 30, 2015 (click "show more" for more info) Presented by Matt T. Proud "Go from A to Z — Zürich Gophers Meetup" Talks given by local users of the Go Programming Language at Google Zürich on 2015-10-30. http://www.meetup.com/Zurich-Gophers Matt T. Proud: "testing/
From playlist Go from A to Z — Zürich Gophers Meetup

Probabilistic Cellular Automata From Cluster Signatures
For the latest information, please visit: http://www.wolfram.com Speakers: Jordan Huffman & Rodrigo Obando Wolfram developers and colleagues discussed the latest in innovative technologies for cloud computing, interactive deployment, mobile devices, and more.
From playlist Wolfram Technology Conference 2016

This video shows how RSA encryption is used in digital signatures. Questions? Feel free to post them in the comments and I'll do my best to answer!
From playlist Cryptography and Coding Theory
