Randomness Quiz Solution - Applied Cryptography
This video is part of an online course, Applied Cryptography. Check out the course here: https://www.udacity.com/course/cs387.
From playlist Applied Cryptography

What are Irrational Numbers? | Number System | Don't Memorise
Watch this video to know more about Rational numbers, Irrational Numbers, Real Numbers and Number System. To learn more about Irrational Numbers, enroll in our full course now: https://infinitylearn.com/microcourses?utm_source=youtube&utm_medium=Soical&utm_campaign=DM&utm_content=CtRtXoT_
From playlist Irrational Numbers
Exploring an amazing pattern that forms when we multiply numbers built only with the one digit
From playlist Number Patterns

Introduction to Complex Numbers (Free Ebook)
http://bookboon.com/en/introduction-to-complex-numbers-ebook This free ebook makes learning "complex" numbers easy through an interactive, fun and personalized approach. Features include: live YouTube video streams and closed captions that translate to 90 languages! Complex numbers "break
From playlist Intro to Complex Numbers

25c3: Making the theoretical possible
From playlist 25C3: Nothing to hide

How Predictable Are You? Three Digit Magic Trick
How predictable are you? Pick a 3 digit number with 3 different digits. Now reverse the digits to get a new number. You now have two numbers. Subtract the smaller number from the larger number. Now add up the digits of the result. Can I guess your number? My blog post for this video: http
From playlist Magic Tricks

NOTACON 2: Recent Attacks Against Hash Functions
Speaker: Matthew Fanto In recent months, a large amount of research into the security of cryptographic hash functions has revealed serious flaws in every widely used hash function, including MD4, MD5, RIPEMD, HAVAL, SHA-0, and SHA-1. These flaws have far reaching consequences, as hash fun
From playlist Notacon 2

Coding Math Mini #9: Random Distribution
This week we take another look at random numbers and the idea of distributing random numbers along a bell curve. Support Coding Math: http://patreon.com/codingmath Source Code: http://github.com/bit101/codingmath
From playlist Minis

DEFCON 17: Locally Exploiting Wireless Sensors
Speaker: Travis Goodspeed Engineer of Superior Buckles, Goodspeed and Gourneau Wireless sensors are often built with a microcontroller and a radio chip, connected only by a SPI bus. The radio, not the MCU, is responsible for symmetrical cryptography of each packet. When the key is loaded,
From playlist DEFCON 17

The Mathematics Used to Solve Crime
Sign up with brilliant and get 20% off your annual subscription: https://brilliant.org/MajorPrep/ STEMerch Store: https://stemerch.com/ Support the Channel: https://www.patreon.com/zachstar PayPal(one time donation): https://www.paypal.me/ZachStarYT Instagram: https://www.instagram.com/z
From playlist Applied Math

OWASP FROC 2010: Beware of Serialized GUI Objects Bearing Data 1/5
Clip 1/5 Speakers: David Byrne and Rohini Sulatycki, Trustwave A recently discovered view state vulnerability in Apache MyFaces and Sun Mojara allows an attacker to access all server-side session data, as well as some globally-scoped application variables. The technical details of the vul
From playlist OWASP FROC 2010

25c3: Messing Around with Garage Doors
Speakers: Timo Kasper, Thomas Eisenbarth Breaking Remote Keyless Entry Systems with Power Analysis We demonstrate a complete break of the KeeLoq crypto-system. Thanks to Power Analysis, even non-specialists can gain access to objects secured by a KeeLoq access control system. KeeLoq rem
From playlist 25C3: Nothing to hide

1. Signatures, Hashing, Hash Chains, e-cash, and Motivation
MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018 Instructor: Neha Narula, Tadge Dryja View the complete course: https://ocw.mit.edu/MAS-S62S18 YouTube Playlist: https://www.youtube.com/playlist?list=PLUl4u3cNGP61KHzhg3JIJdK08JLSlcLId Introduces currency, banking, and electro
From playlist MIT MAS.S62 Cryptocurrency Engineering and Design, Spring 2018

Speaker: Travis Goodspeed The Texas Instruments MSP430 low-power microcontroller is used in many medical, industrial, and consumer devices. When its JTAG fuse is blown, the device's firmware is kept private only a serial bootstrap loader (BSL), certain revisions of which are vulnerable to
From playlist 25C3: Nothing to hide

The Crimes of Ted Bundy And Night Stalker (Serial Killers Documentary) | Real Stories
The Crimes of Ted Bundy And Night Stalker - a double episode release of World's Most Evil Killers 1. The story of Ted Bundy, a suave, outwardly normal psychology graduate who admitted to killing at least 35 women before being executed in 1989. The story of Ted Bundy, a suave, outwardly no
From playlist Crime Documentaries
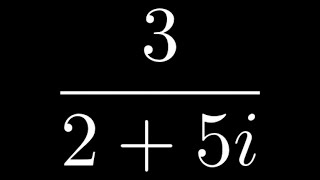
Dividing Complex Numbers Example
Dividing Complex Numbers Example Please Subscribe here, thank you!!! https://goo.gl/JQ8Nys
From playlist Complex Numbers

Tina Eliassi-Rad - The Pitfalls of Using ML-based Optimization - IPAM at UCLA
Recorded 03 March 2023. Tina Eliassi-Rad of Northeastern University, Computer Science & Network Science presents "The Pitfalls of Using ML-based Optimization" at IPAM's Artificial Intelligence and Discrete Optimization Workshop. Abstract: I will describe two graph problems where ML-based o
From playlist 2023 Artificial Intelligence and Discrete Optimization

We discuss what imaginary numbers are and how they are part of the larger set of complex numbers in this free math video tutorial by Mario's Math Tutoring. This is a nice introduction to working with i. We also go through some examples. 0:26 A Hierarchy of Different Types of Numbers 1:03
From playlist Imaginary & Complex Numbers