
70-680 : Windows 7 Offline Files
More videos like this online at http://www.theurbanpenguin.com Offline files is not knew to Windows 7 and has been round for over a decade now. It is still useful and is used. We enable offline files though the share and then clients can synchronize files to their local machine to be avail
From playlist 70-680

There's No Such Thing As Offline?!? | Idea Channel | PBS Digital Studios
Viewers like you help make PBS (Thank you 😃) . Support your local PBS Member Station here: https://to.pbs.org/donateidea Are You Online? What an outdated question this has become! Of course you're online, unless you're an off-the-grid survivalist or a remote tribesmen!! From Facebook to
From playlist Newest Episodes

Google Docs: Editing Docs Offline
We're going to show you how to view and edit your files even when you don't have an Internet connection. It requires a little bit of setup to enable the feature, but once you set it up you'll have an offline copy of your documents that will sync with the online version whenever your device
From playlist Google Docs

Google Docs: Changing Ownership of a Doc
We're going to show you how to transfer ownership of a document to another person. The new owner can be someone who you've already shared the document with, or it could be someone new. This method does have some limitations. You can't transfer ownership with the mobile app. Also, if your
From playlist Google Docs

CRDTs for Mortals (Offline First Apps)
What do CRDTs and frontends have to do with each other? James talks about how CRDTs finally deliver on the promise of local-first apps, which provide superior user experience, and explains how simple CRDTs can be and how to leverage them to create robust local-first apps. EVENT: dotJS 20
From playlist Mobile Development

OHM2013: Another Rambling Talk About EMV
For more information visit: http://bit.ly/OHM13_web To download the video visit: http://bit.ly/OHM13_down Playlist OHM 2013: http://bit.ly/OHM13_pl Speaker: Tim Becker A brief introduction to EMV, the protocol spoken between smart card based credit cards and terminals. A mixture of plast
From playlist OHM 2013

Using Google Docs on a Mobile Device
The Google Docs mobile app is pretty different from the desktop browser version. We'll show you how to get around in the app and find some of the "hidden" features like word count, page setup, and offline mode. We're also going to look at some of the differences and limitations of the mo
From playlist Google Drive and Docs
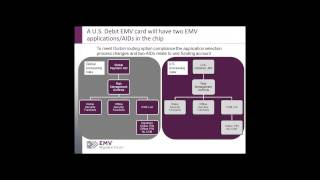
EMV 101: Fundamentals of EMV Chip Payment
Commonly used globally in place of magnetic stripe, EMV chip technology helps to reduce card fraud in a face-to-face card-present environment; provides global interoperability; and enables safer and smarter transactions across contact and contactless channels. EMV implementation was initia
From playlist Payments

Certificate Overview: Advanced Cybersecurity
More information: https://online.stanford.edu/professional-education/cybersecurity?utm_source=youtube&utm_medium=social&utm_campaign=webinar Gain vital skills needed for today’s cyber workforce. From state-of-the-art software security design principles to concrete programming techniques,
From playlist Computer Science & Cybersecurity

Write Your First Service Worker
Service workers are a hot topic in JavaScript right now, but how can you get started? In this video you'll learn how to write your very first service worker. Best of all, it'll only take 10 minutes! If you liked this video, check out Carmen's book at https://serviceworkerbook.com. Check
From playlist JavaScript

There is a lot of talk about Progressive Web Apps at the moment. It is a hot topic in the JavaScript community. In this talk, we will briefly explore what a PWA is and how to build one. We will look at the benefits of PWA's and more importantly their limitations. We then look a bit deeper
From playlist Progressive Web Apps

Decentralised public key infrastructure
Speaker - Tim Hobson, The Alan Turing Institute About the event This hybrid conference brought together prominent academics and key players in the field of digital identity from government and industry sectors. The event focused on the socio-technical infrastructure opportunities and ch
From playlist Turing trustworthy digital identity international conference 2022

Black Hat USA 2010: Attacking Kerberos Deployments 2/4
Speakers: Scott Stender, Brad Hill & Rachel Engel The Kerberos protocol is provides single sign-on authentication services for users and machines. Its availability on nearly every popular computing platform - Windows, Mac, and UNIX variants - makes it the primary choice for enterprise aut
From playlist BH USA 2010 - OS WARS

O'Reilly Webcast: What's New in Windows Server 2008 R2 AD
Want to learn what's new in Active Directory for Windows Server 2008 R2? Active Directory MVPs and authors Brian Desmond (Active Directory, 4th Edition) and Laura Hunter (Active Directory Cookbook, 3rd Edition) discuss exciting new features in R2 for AD including the AD Recycle Bin, AD Pow
From playlist O'Reilly Webcasts

JSChannel 2015 - Opening Keynote
Opening Keynote by: Douglas Crockford The web was originally imagined to be a simple distributed document retrieval system. It is now being used for applications that go far beyond the system's original capabilities and intentions. We have found ways to make it work, but they are difficu
From playlist JSChannel 2015

O'Reilly Webcast: Building Offline Web Apps with HTML5
For years, the terms "web" and "online" have been intrinsically linked in people's minds. With HTML5, the web's dependency on a connection to the internet has been broken. Web apps can now run offline in modern browsers thanks to HTML5 support for client-side storage of relational data, ke
From playlist O'Reilly Webcasts 2

22C3: Internet Voting in Estonia
Speaker: Tarvi Martens First-ever pan-national official occasion. Tarvi, the project manager for Estonian e-voting, is going to explain how the Internet voting system is built and how the Internet voting was made possible for the Estonian voters. For more information visit: http://bit.
From playlist 22C3: Private Investigations

Internet Explorer, Smart Locks - CS50 Podcast, Ep. 4
The CS50 Podcast is hosted by CS50's own David J. Malan and Colton Ogden at Harvard University. Each episode focuses on (and explains!) current events and news in tech and computer science more generally. https://www.youtube.com/playlist?list=PLhQjrBD2T381-QVEPQ5GODGTgMNfpvYzU In this ep
From playlist CS50 Podcast

CERIAS Security: Privacy and anonymity in Trust Negotiations 1/5
Clip 1/5 Speaker: Anna Squicciarini · University of Milano Trust negotiation is an emerging approach for establishing trust in open systems, where sensitive interactions may often occur between entities with no prior knowledge of each other. Although several proposals today exist of s
From playlist The CERIAS Security Seminars 2005 (1)

70-680 : Windows 7 Enable Features Offline with DISM
More videos like this online at http://www.theurbanpenguin.com Many new features have made their way into Windows 7. Imaging and image maintenance makes up a big percentage of these new features. Being able to service images offline is hugely importance and in this video we look at enablin
From playlist 70-680